Open Source Surveillance takes intelligence gathering and cyber espionage to a whole new level. It can be used for offensive security, but from the other hand can be also helpful in OSINT and law enforcement investigations. Thanks to 18 modules, OSS can show real-time view of the city from variety of cameras, social media posts or Internet facing devices. Read article to get familiar with the tool and potential cases it can help with.
Due to size of the screenshots please turn on desktop version if you are on mobile.
TL;DR
Open Source Surveillance is real-time intelligence gathering tool, which uses data from variety of sources, including social media, cameras, transportation, Internet of things and Industrial Control System devices, WIFI network and much more.
More info & screenshots
https://www.os-surveillance.io
Newest update
Gather geo intel in a blink of an eye with new Open Source Surveillance update. It brings new modules, improved interface and enhanced performance to collect data even more efficiently. Now it's easier than ever to detect, track, and monitor potential threats in real-time. #OSINT pic.twitter.com/WekVAgx9GZ
— Offensive OSINT (@the_wojciech) March 30, 2023
Access
Application is almost done, there are some small UI/CSS bugs or unexpected exceptions, but it's fully working intelligence gathering tool that can give a lot of fun and help with variety of cases.
If you are law enforcement officer, investigative journalist, intelligence analyst or OSINT researcher and want to give the tool a try please reach out to me from your corporate email address. Please also let me know if you are subscriber via Paypal or Stripe to get access
Patreon access

Wait for gif to load which presents live view of the tool
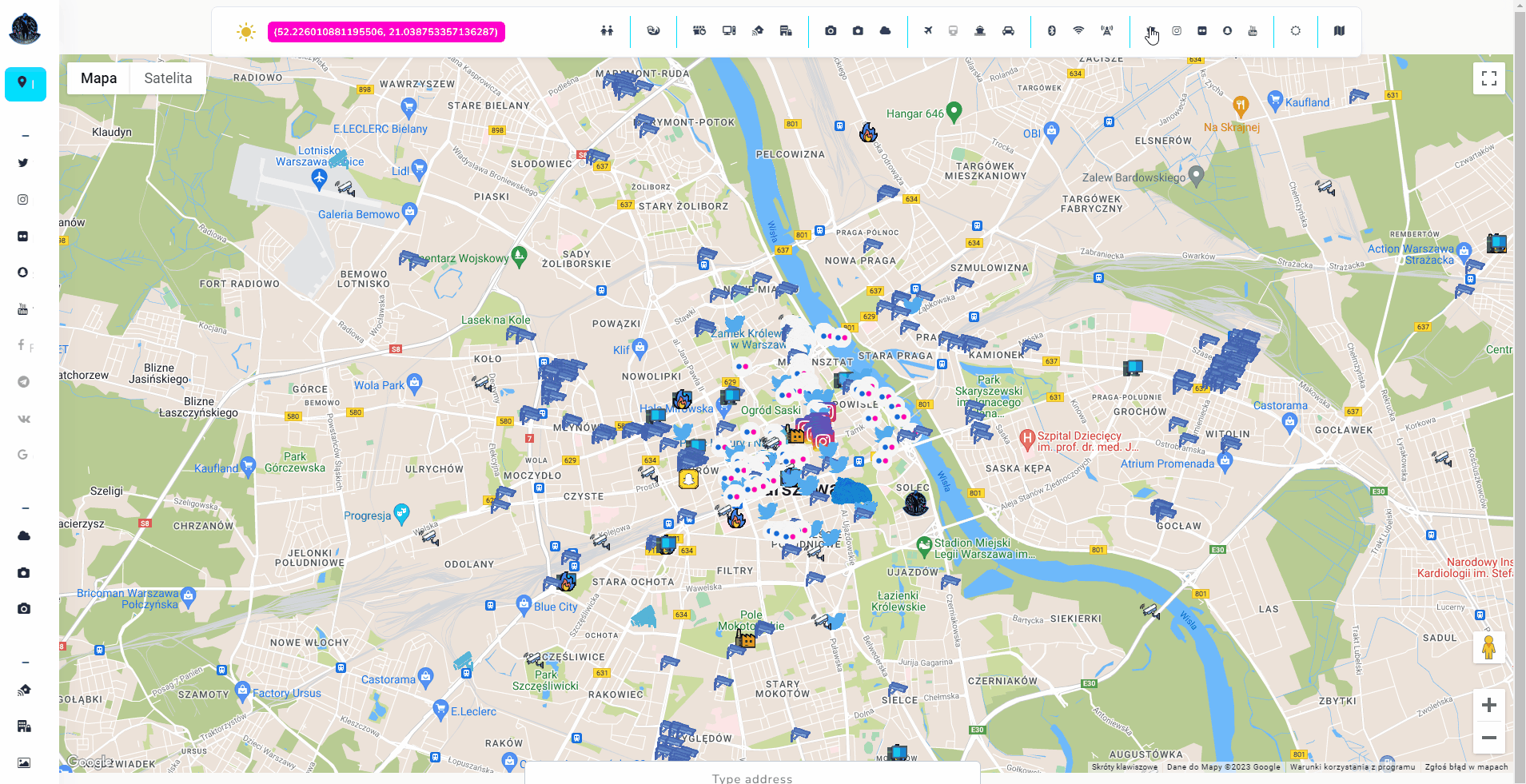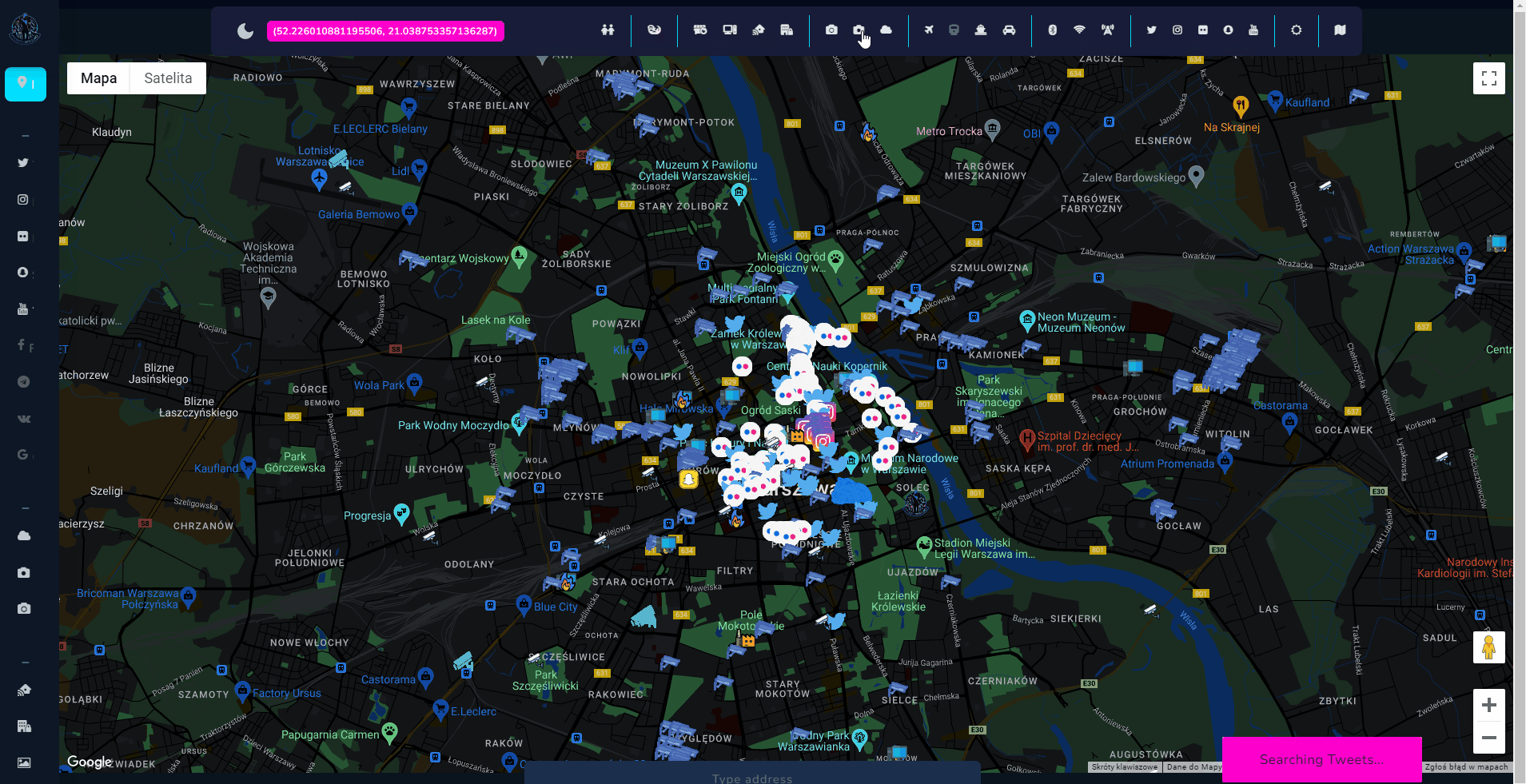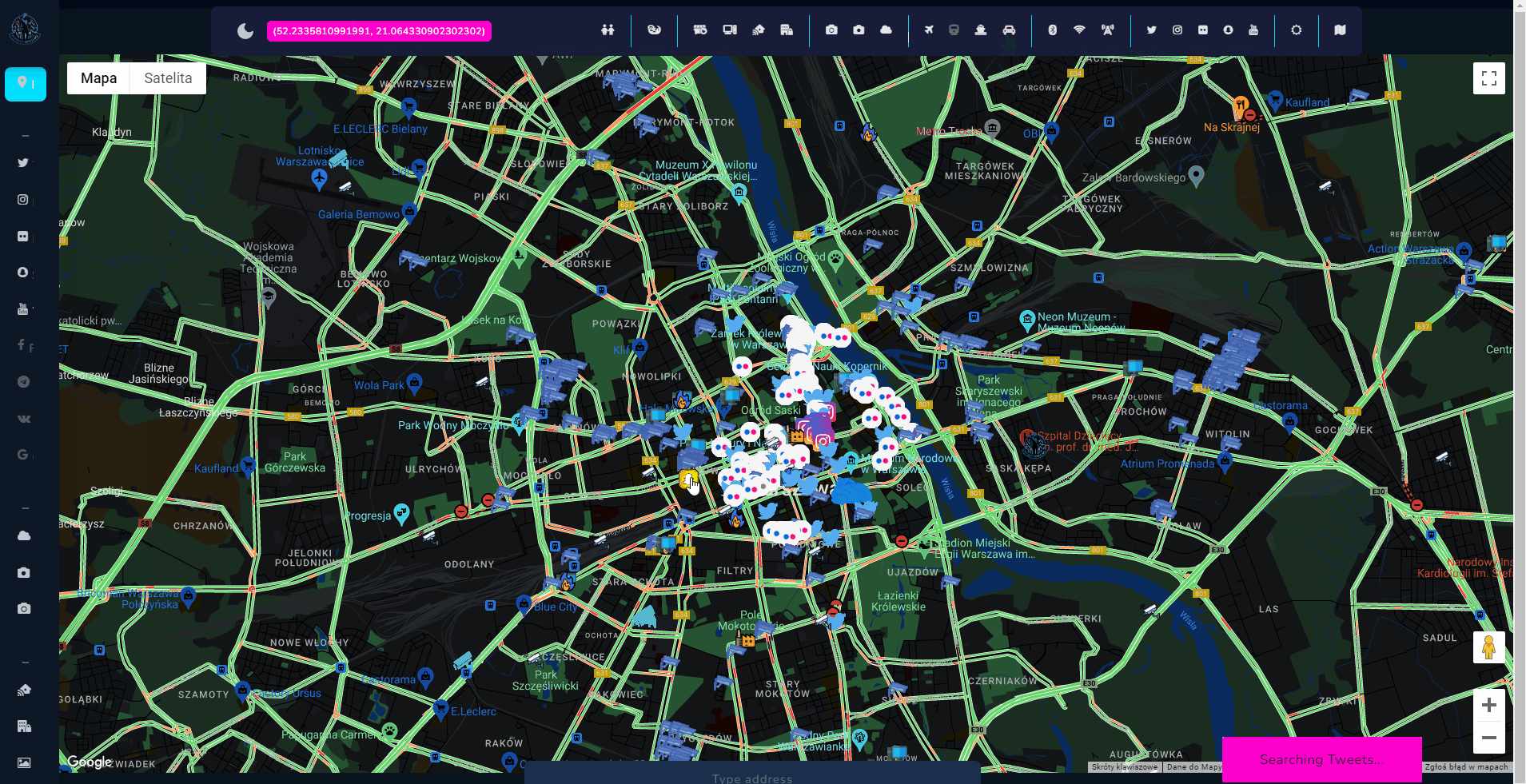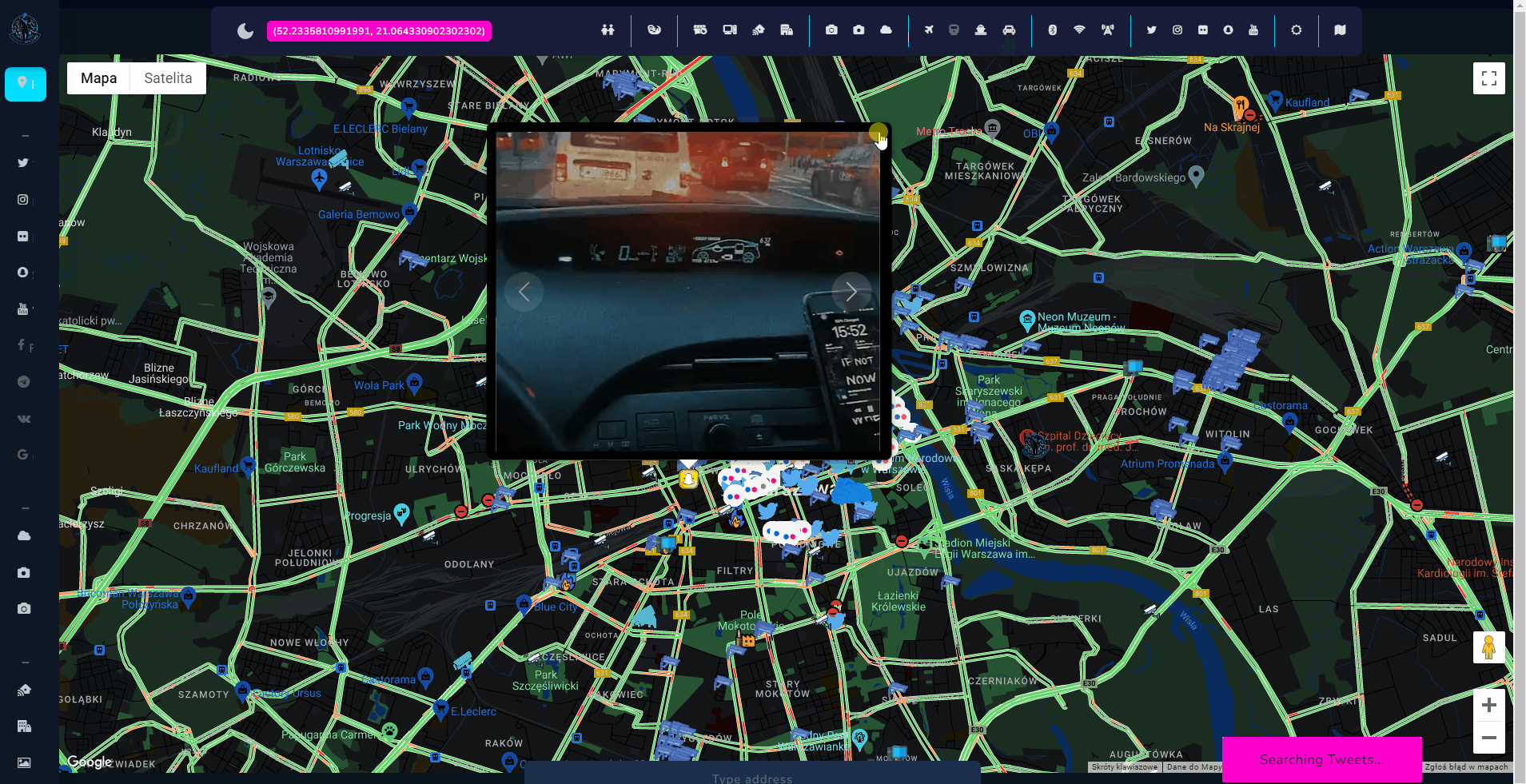
Introduction
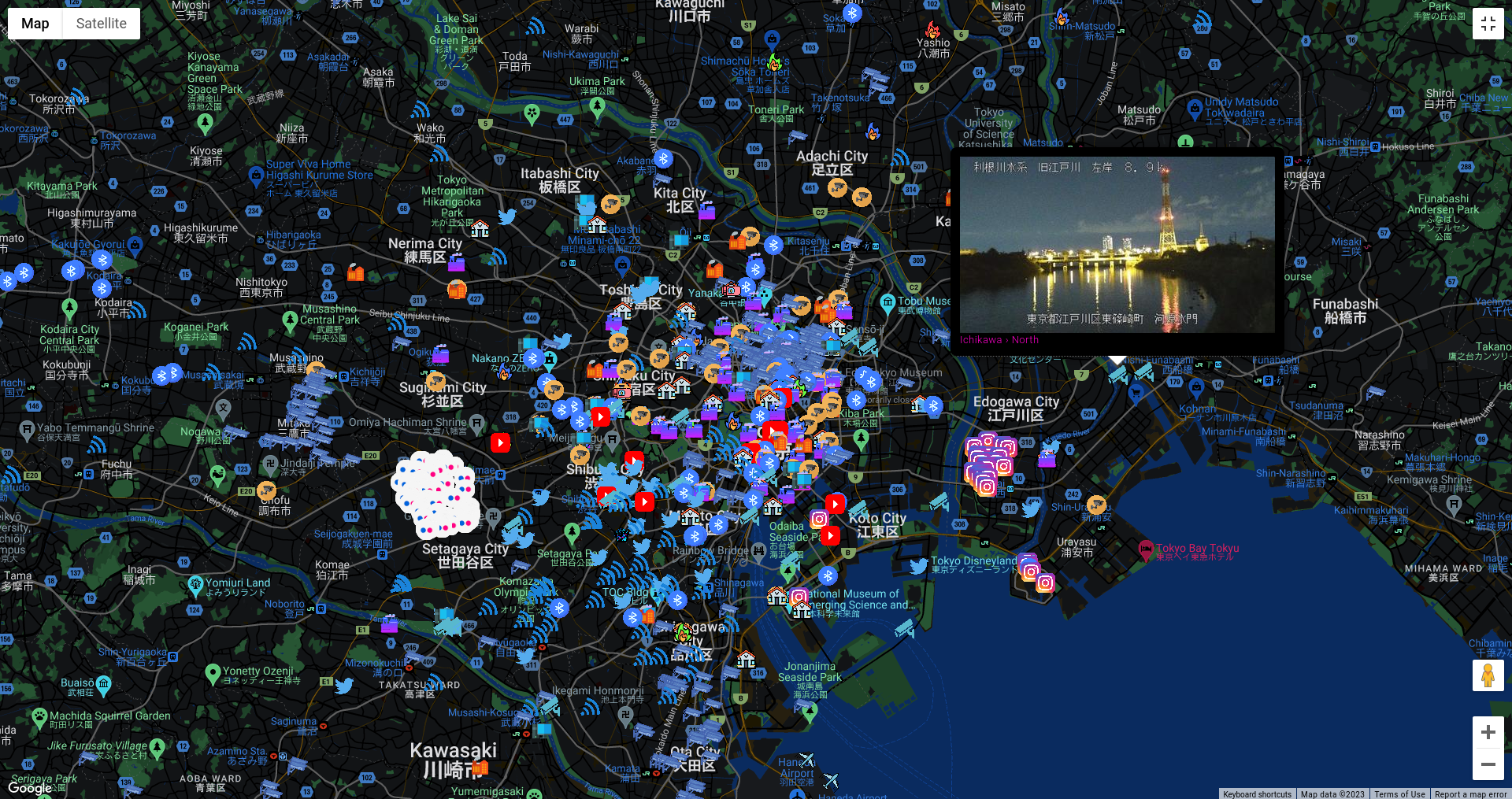
Nowadays, almost every our step is tracked and under surveillance. It does not matter if it's online activity or 'on the ground', have you ever thought how many cameras are you on during simple walk in your city? How many Snaps, Instagram photos or Tweets are being taken at specific location? Where are unsecure Wifi networks that might end in cyber security breach? Are there any Internet facing Industrial Control System devices operating in critical infrastructure?
Open Source Surveillance can give you answer for above questions and much much more depending on your goal, whether it's getting access to some devices, finding exact coordinates of the photo or checking activity on social media during protests.
Tool itself is quite complex (design, implementation, API sources) but the concept stays as easy as possible, and User Interface is very intuitive, so let's talk about the project and how to get out of it as much as possible.
Open Source Surveillance
Tool has been developed to assist in variety of OSINT investigations that require to research specific place or location. First case that comes to mind is geolocation task of some photo. If you suspect that picture might have been taken in some city, you can easily scan for current and historical view via Snapchat, Twitter, Instagram, Flickr and even YouTube, or look on live footage from street cameras. However, possibilities of the tool are much more beyond that.
Choosing a target
As mentioned, tool is most useful when gathering intelligence about specific places, which can be country, city, district or even street. I recommend to set your target as a city and around 40-50km around it, since some sources are not always accurate. You can add as many 'targets' i.e. places to scan, as you want, and each one has separate 'workspace', which is independent from other searches.
Give your investigation a title, select place you want to research and click Save.
API Keys
In the background, database with predefined keys exists and provide the keys, depending on usage and rate limitations. So during big load and lot of requests it might be unavailable. In that case, user needs to provide their own API keys or tokens for each affected module in "Keys" tab.
Modules
Modules are separated by category and all of them are quite different from each other. It's related to how some API works. As a quick example - Flickr shows photos in 5km radius but Wigle can present results only on given boundaries.
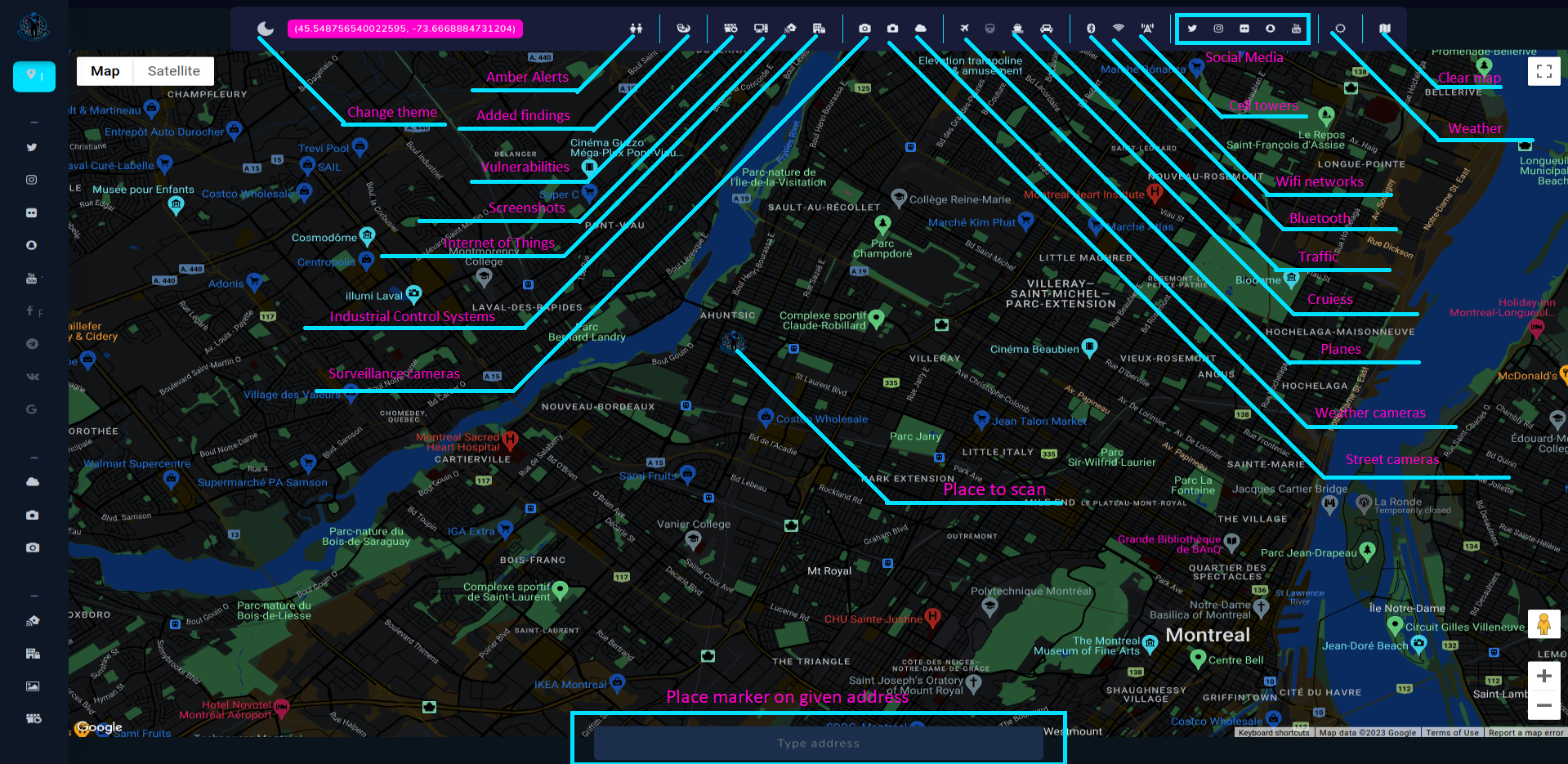
Almost each module has option to Scan, Show results from database and Hide from map for better customization of all findings.
We will quickly go through all modules to get acquainted with method of operating and what kind of findings we can expect.
Social Media
We all know that almost every social media platform allow to add location to your posts including ones with photos and videos, so it's relatively easy to extract all information especially when service has an API, like Twitter.
Twitter
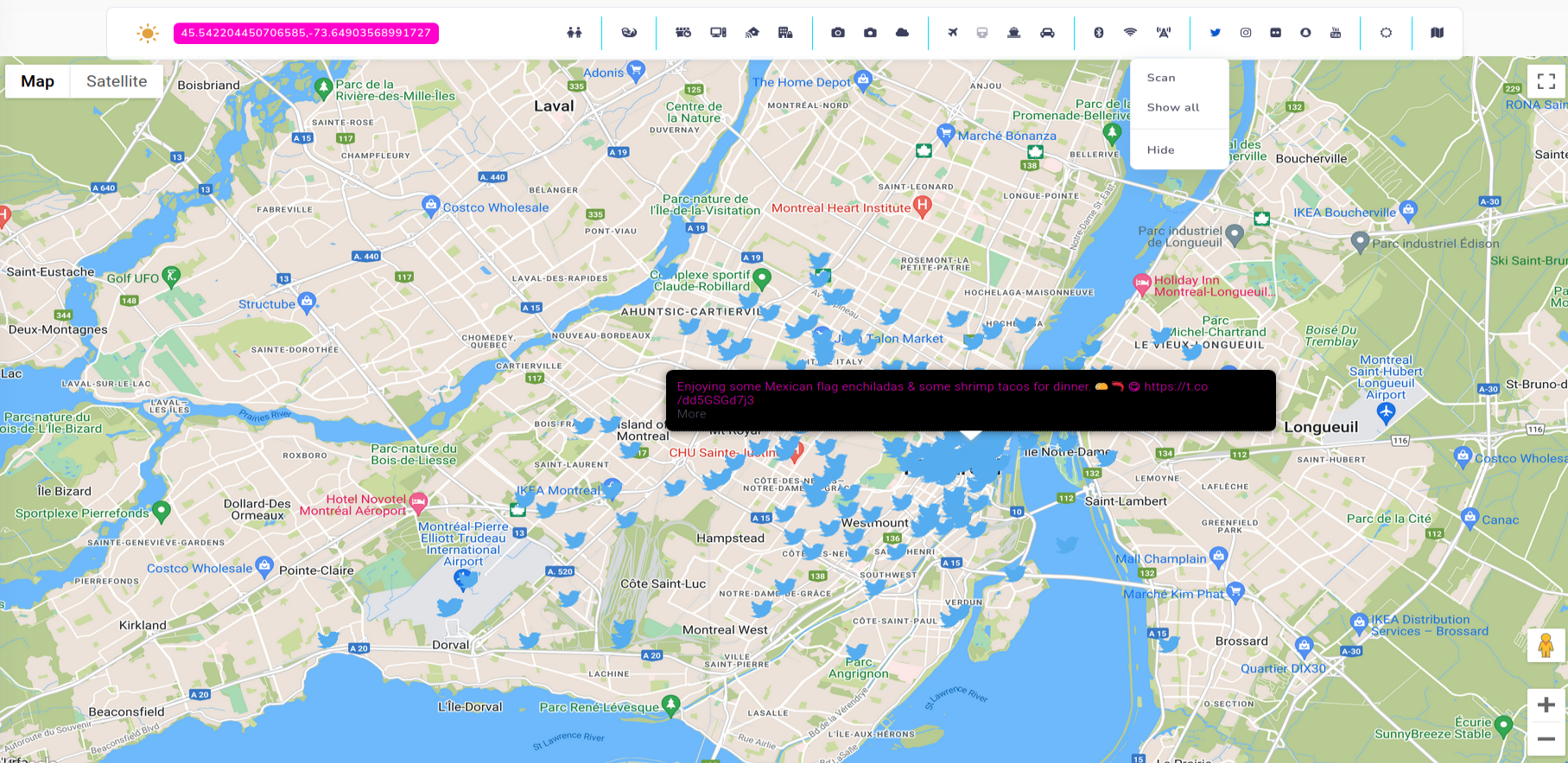
Every tweet is saved into database, with all gathered details, and can be accessed anytime. We know in this case, this Mexican Bar is 3 Amigos.
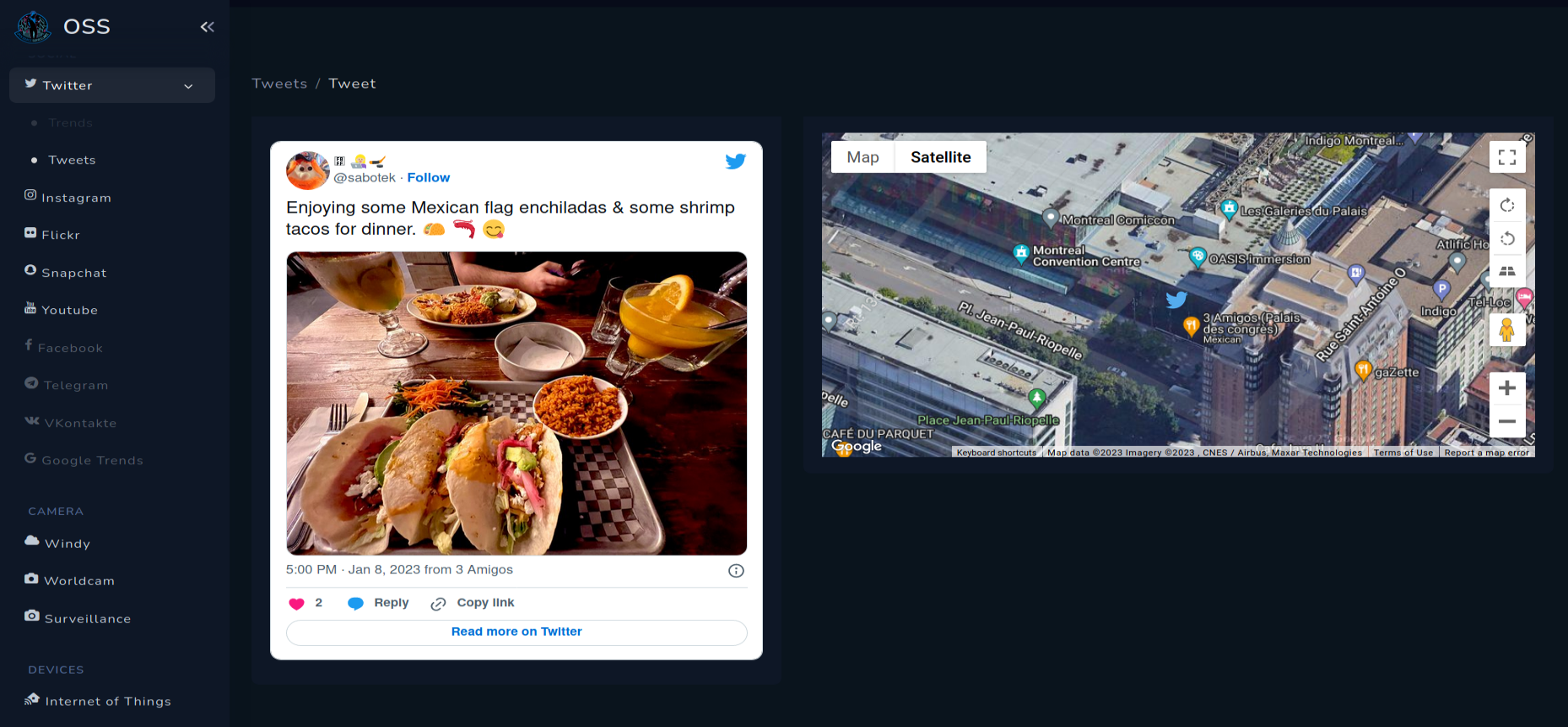
Snapchat
Snapchat is not accurate, but gives you all Snaps in 5 kilometres radius. If there are more than one Snap, you can view them all in the popup on the map.
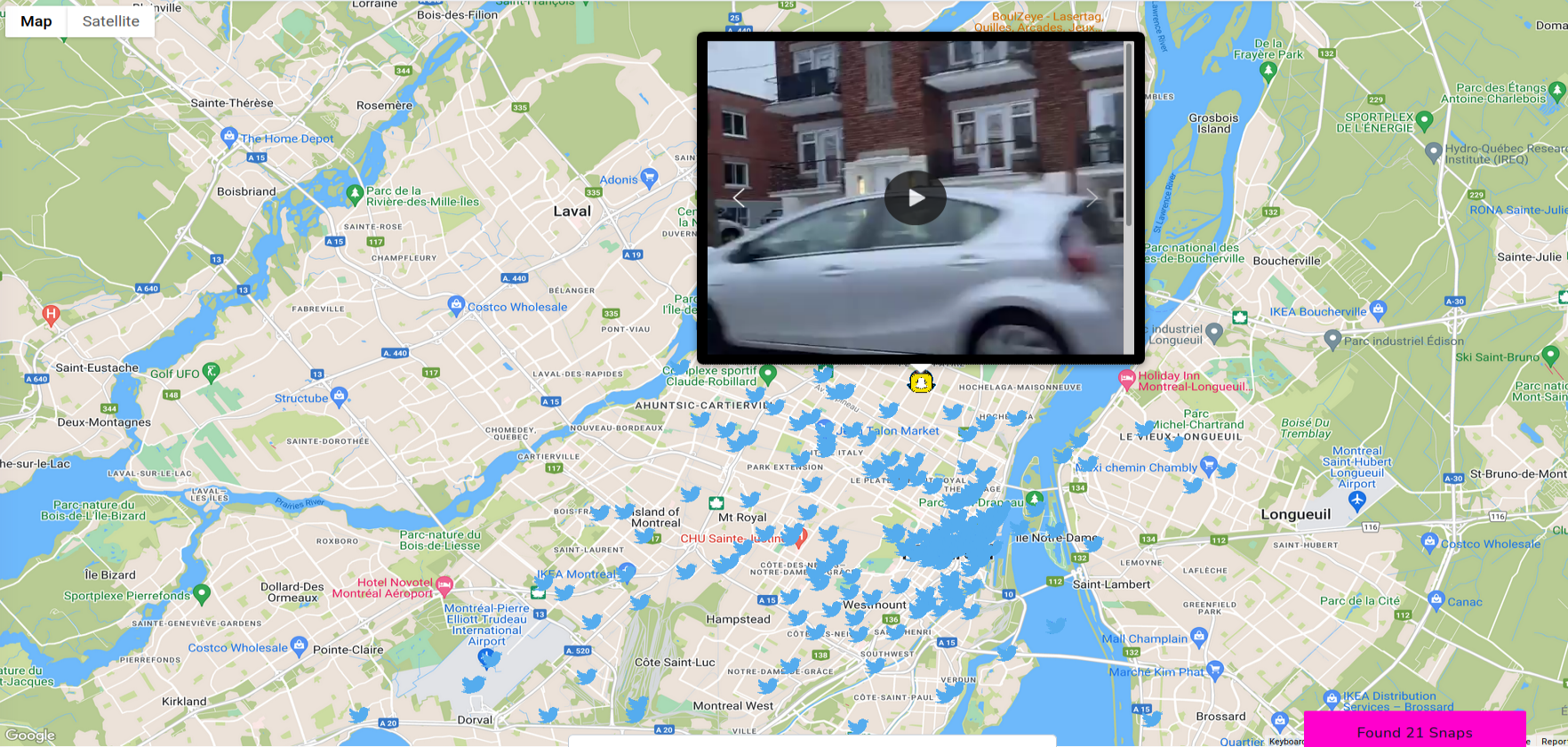
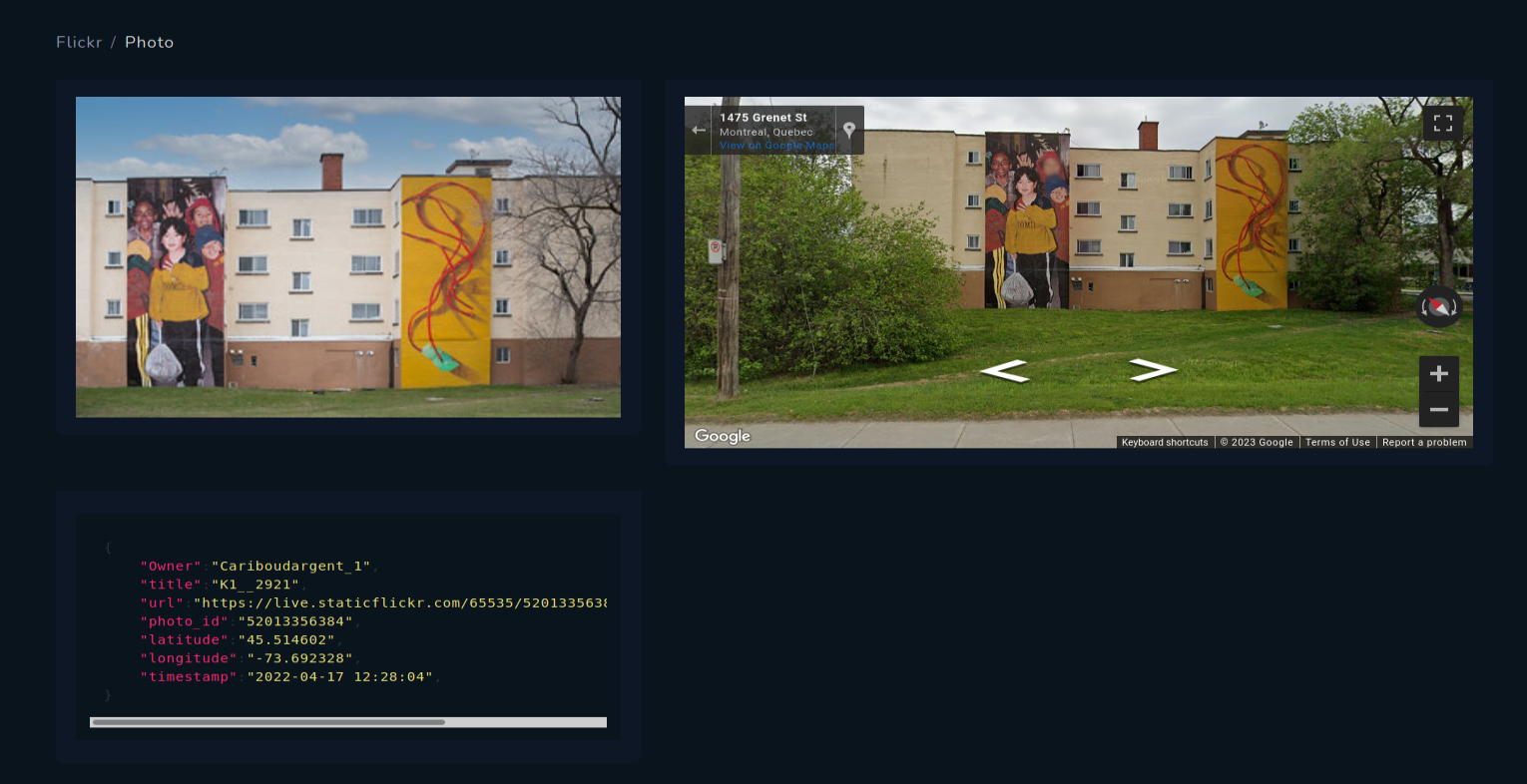
Flickr
Flickr from the other hand is the most accurate from all of the social medias, and there are literally thousands picture in every city, what is very useful for OSINT geolocation tasks.
Very accurate location of Flickr photos
Instagram works differently than previous modules, it shows places that are "registered" in Instagram and Meta in general. After having ID of the place, it's possible to extract photo.
Open Source Surveillance shows you only external link to the photos of given place on Instagram.
Every place is saved with external links to particular Instagram place.
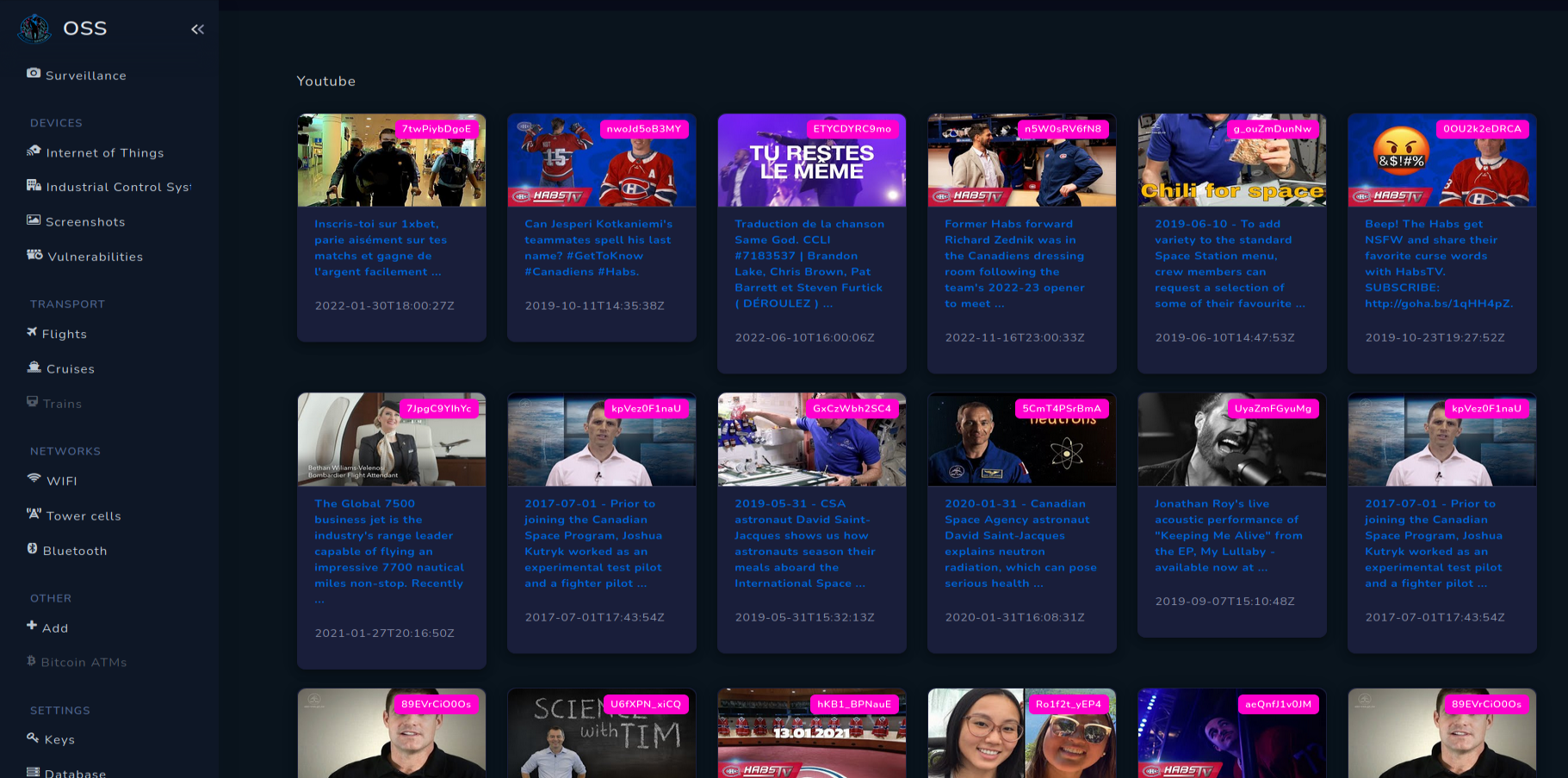
YouTube
YouTube grabs videos from API on radius 20km, with limit 50 per search. Mostly videos are from events like concerts or sports games but you can find very differentiated topics.
Networks
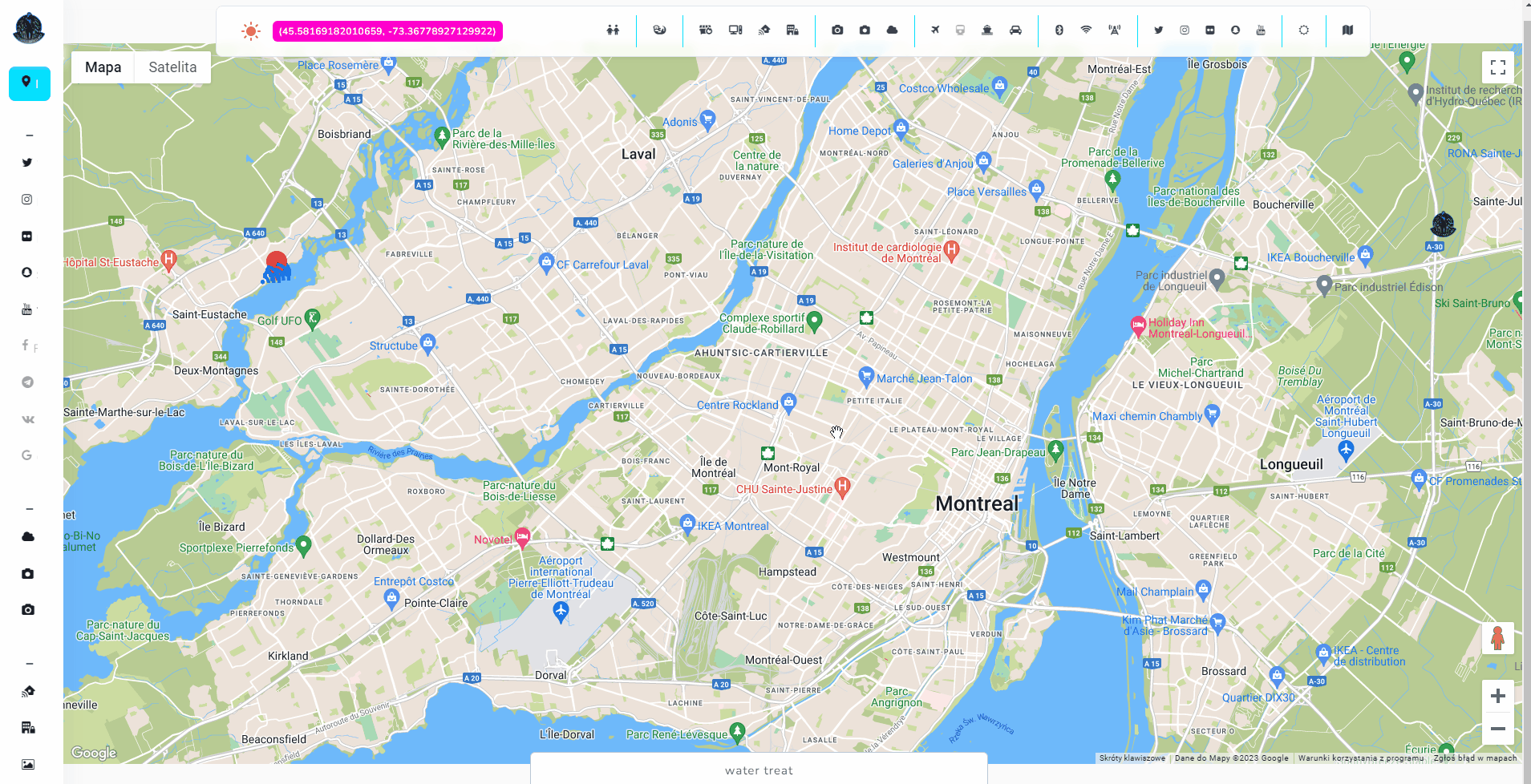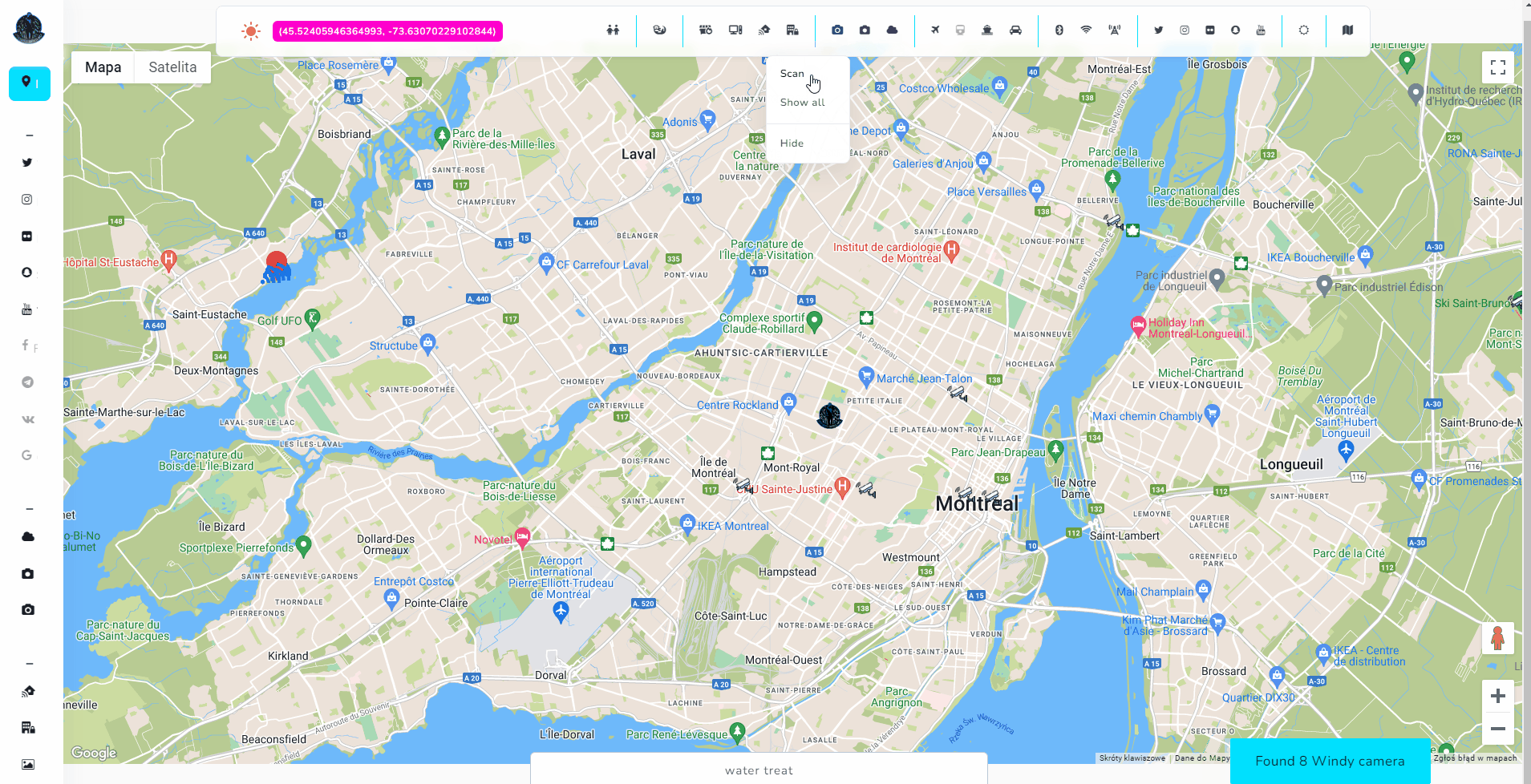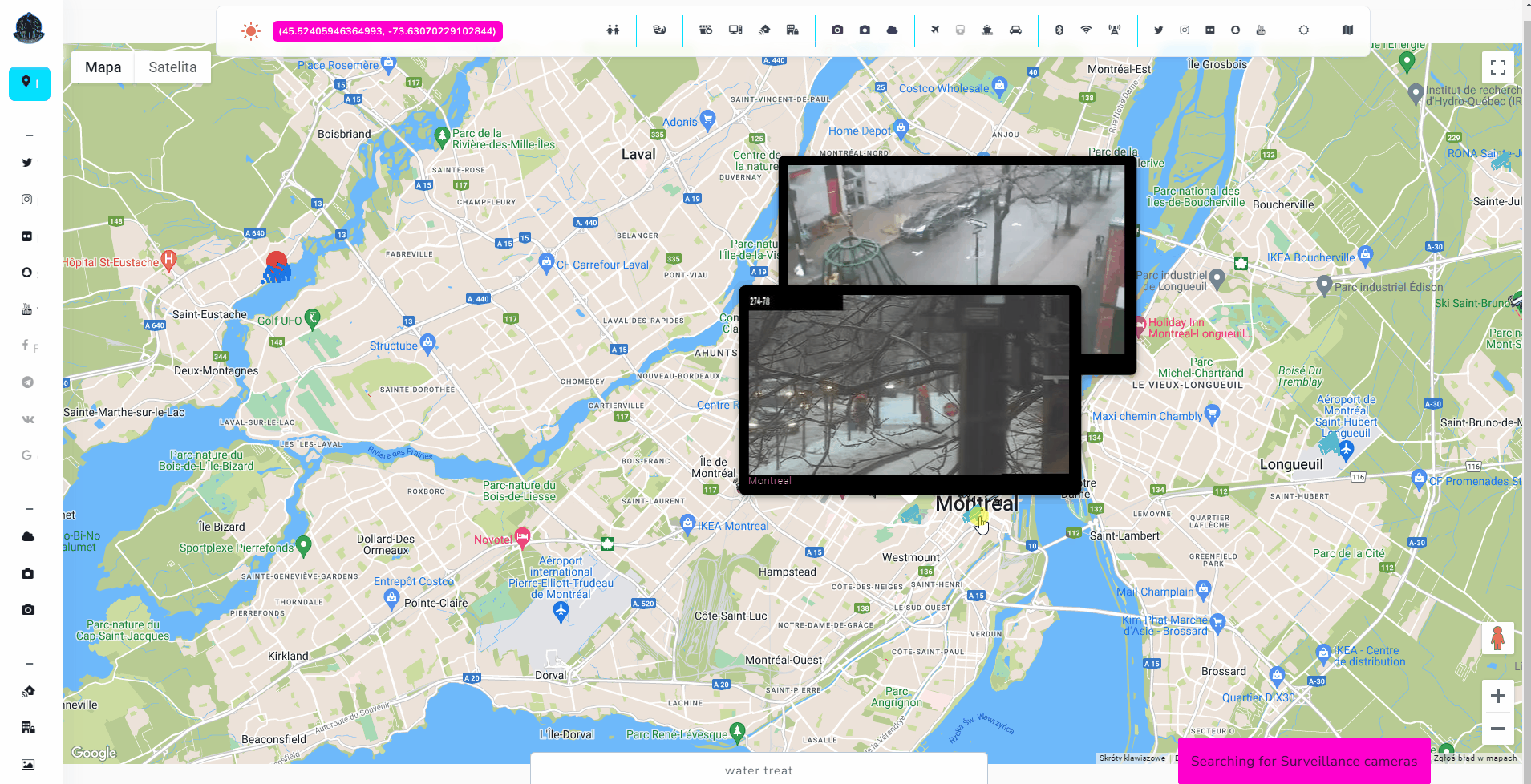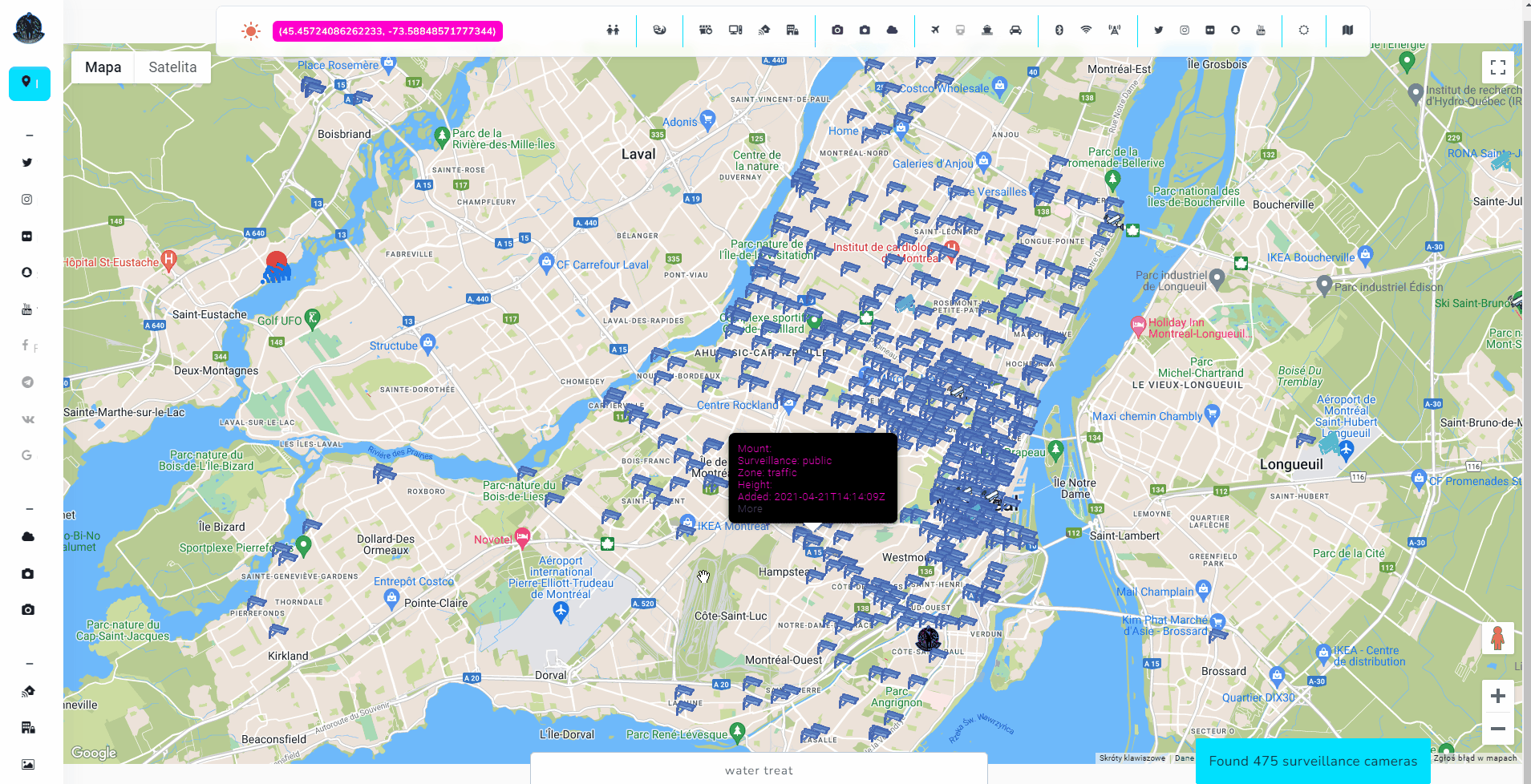
Every piece of information is important when dealing with location based investigations. To make Open Source Surveillance very detailed, Wigle network search has been implemented.
Easily display Wifi and Bluetooth networks or cell towers on the map, or search it by SSID. Both methods work on map bounds rather than placed marker.
So, zoom into the place you want to search WIFI for, and click Scan from collapsible menu. I like to search for critical infrastructure facilities and check SSIDs and encryption of the networks. How to have more fun with this feature I will show later.
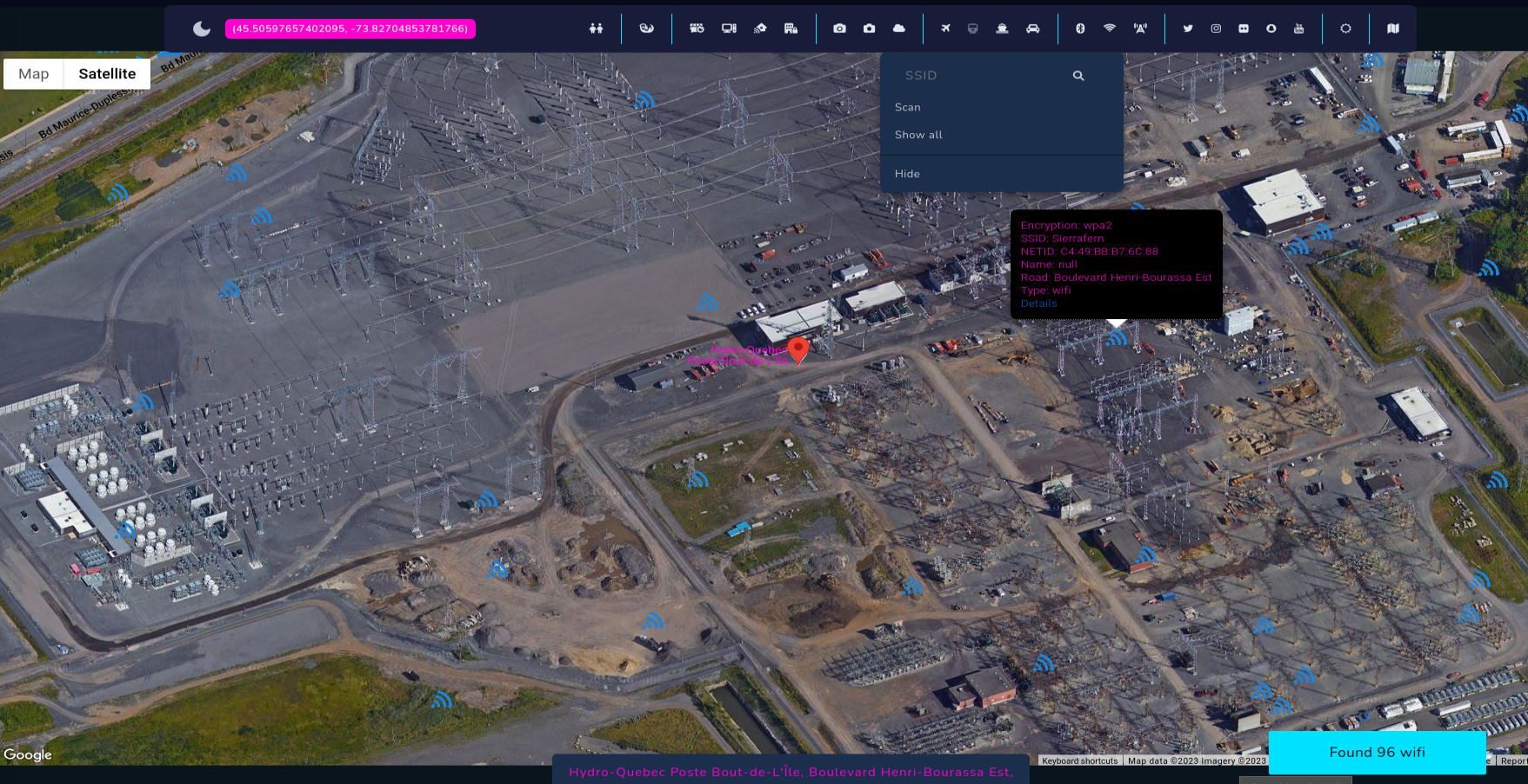
To search for specific network by SSID you need to zoom out to the bounds you want to search in, type input in SSID field and click magnifying glass icon.
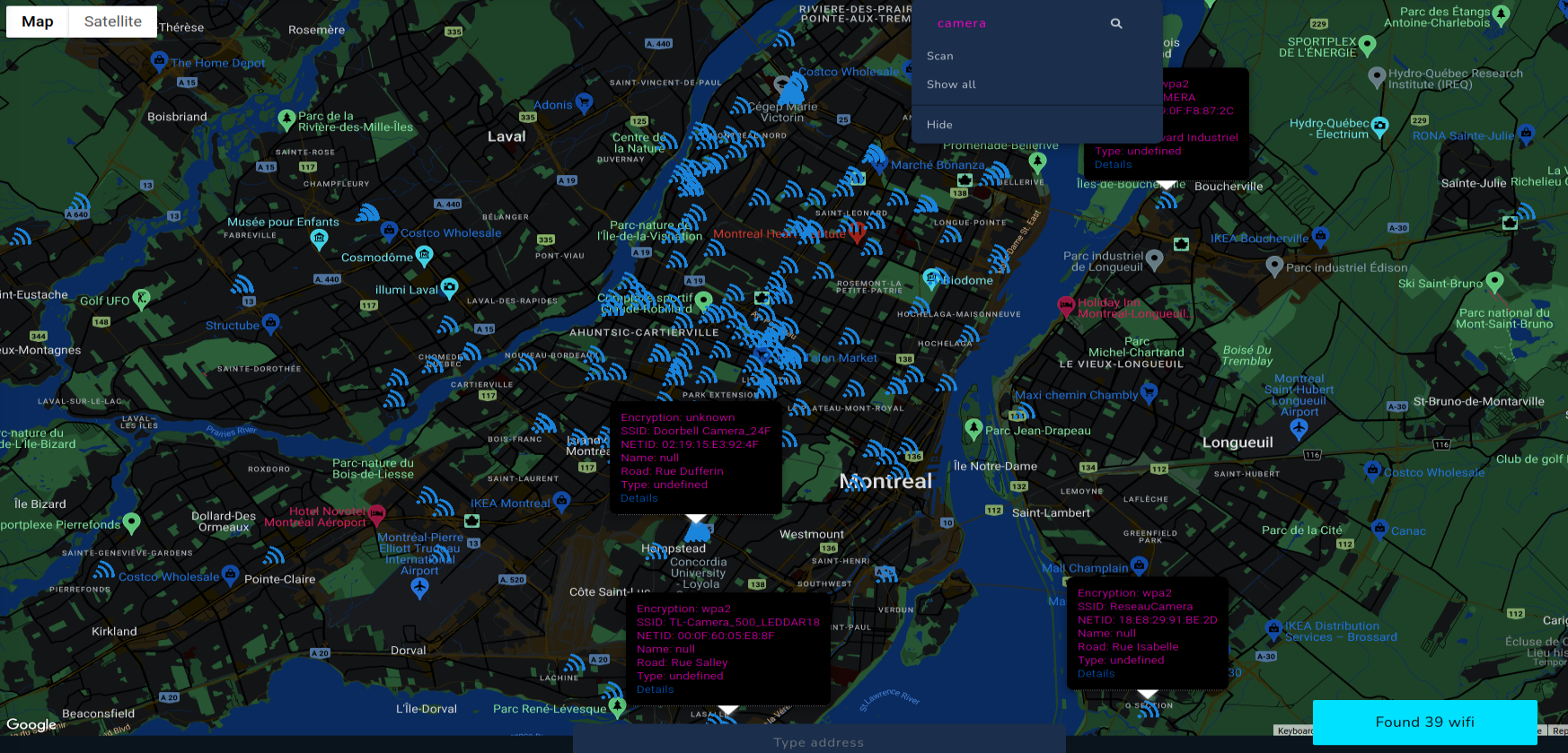
Above screenshot shows how to search WIFI with "camera" in SSID. If information from Wigle is up to date, you will physically come across these networks in scanned places.
After that, it's super easy to search for networks with WEP encryption or without password, go to the place and get access. That's another way how you hack your way into cameras and potentially different buildings and facilities.
In the same way we can use Bluetooth and Cell tower features.
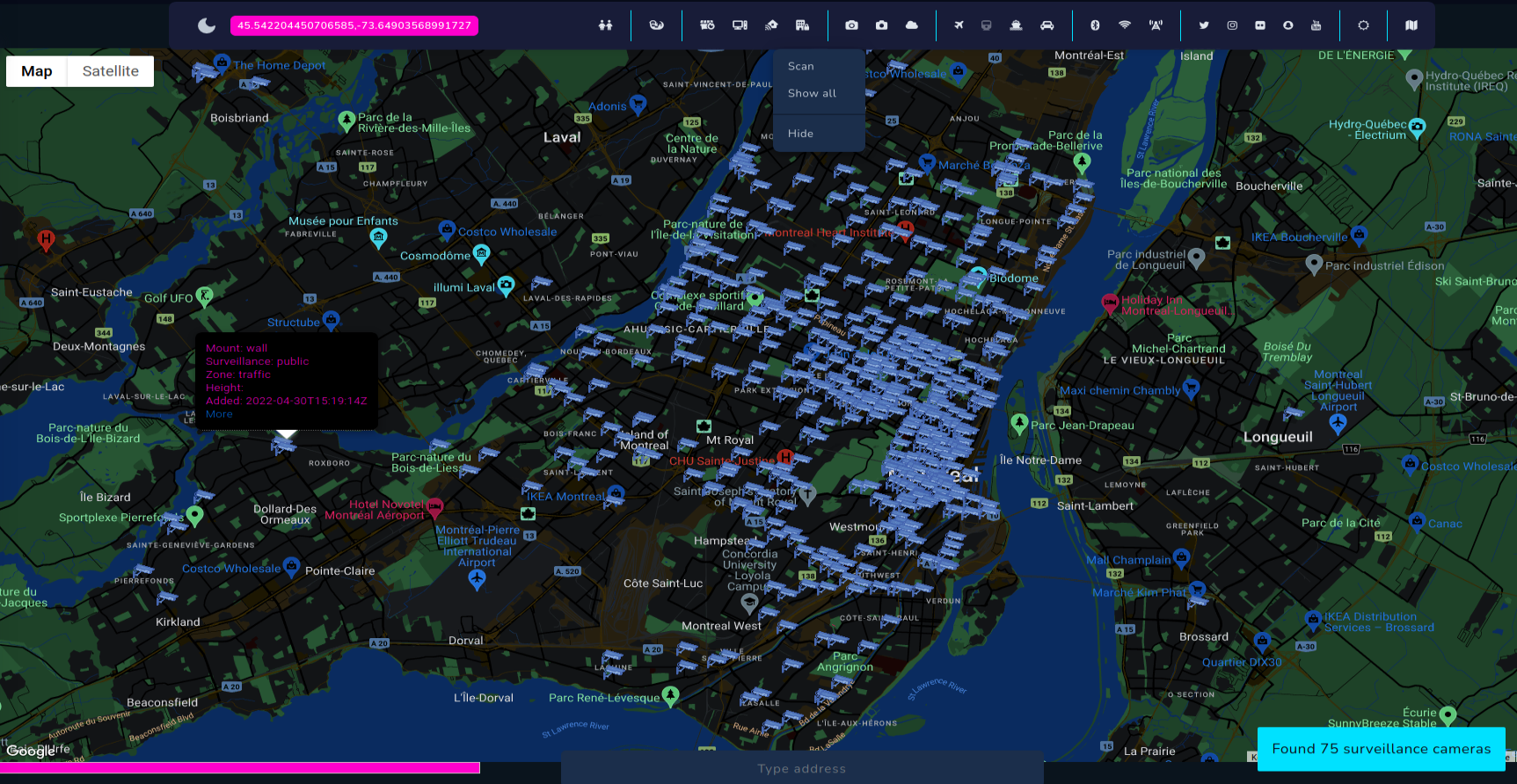
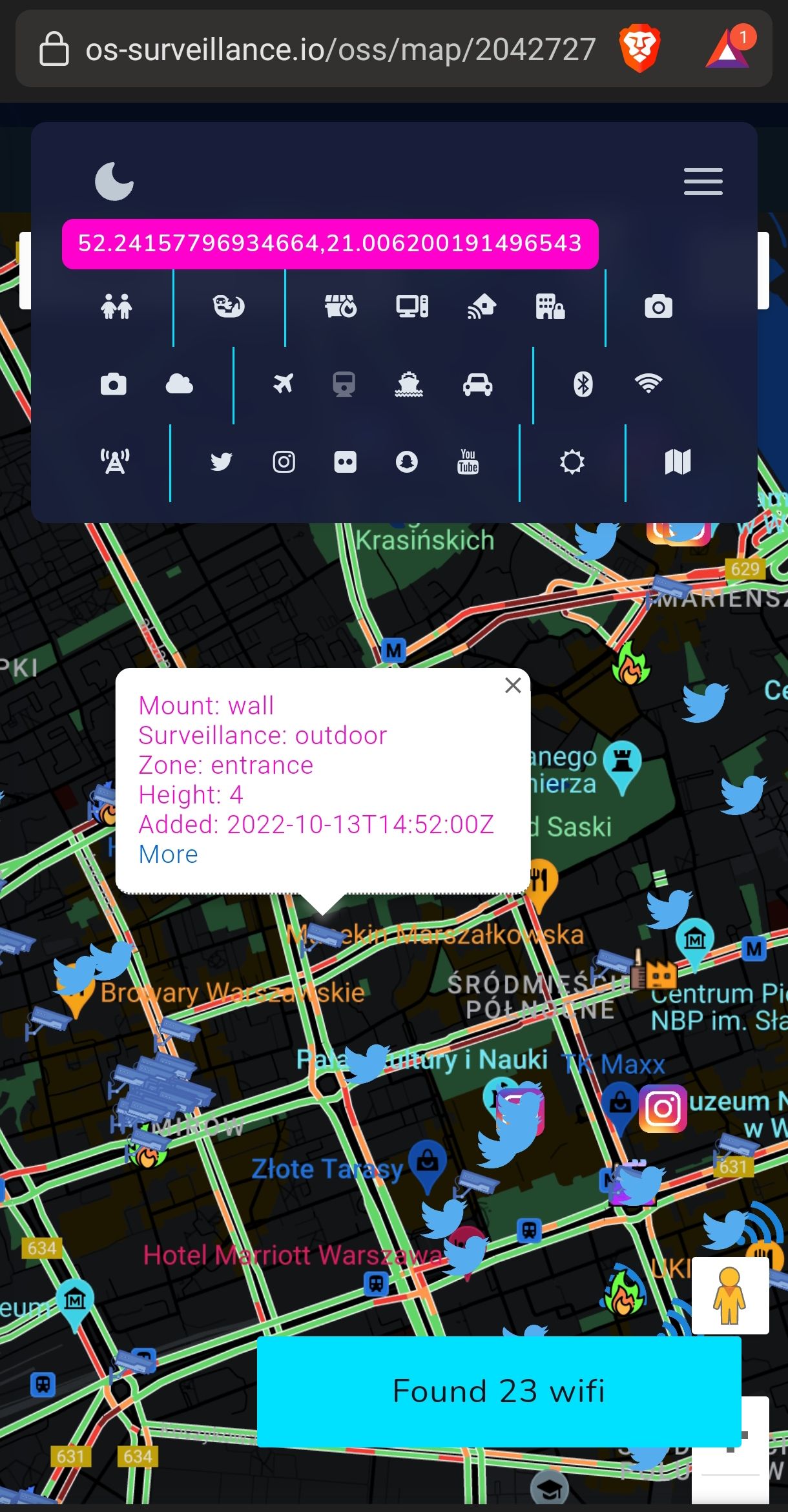
Cameras
Cameras are the heart of every modern city and currently it's hard to be completely untraceable when going outside. There are literally thousands of such devices in every city, including street, weather or surveillance cameras. Some of the are accessible online, some of them are unsecured or Internet exposed and some of them are completely private.
Open Source Surveillance gathers information about devices from different open sources and allows to get live footage from weather cameras or exact position of some CCTV.
- Surveillance cameras
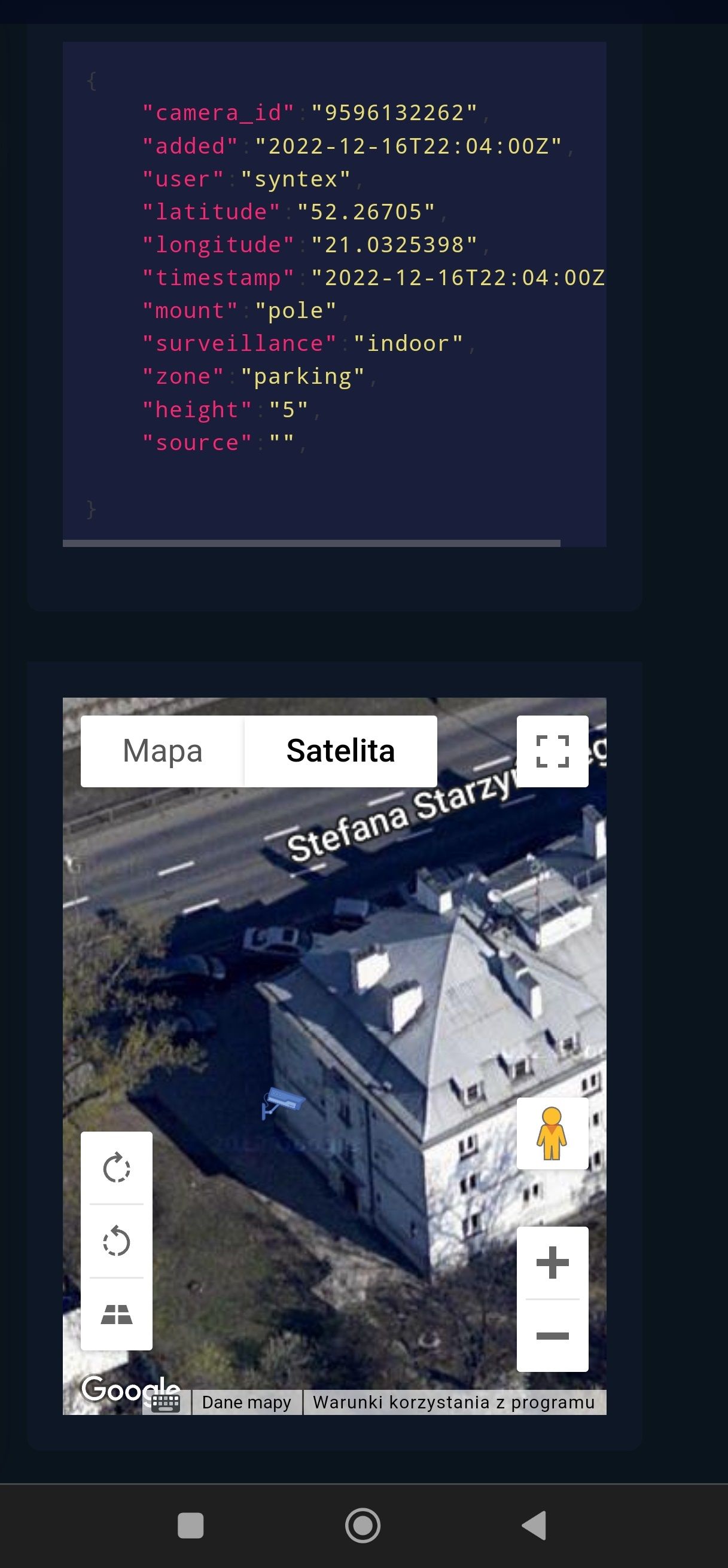
To confirm authenticity of the finding, we need to go deeper and find cameras on street view.
Zoom in on one of the place shows couple surveillance cameras on the building at Rue Montfort street.
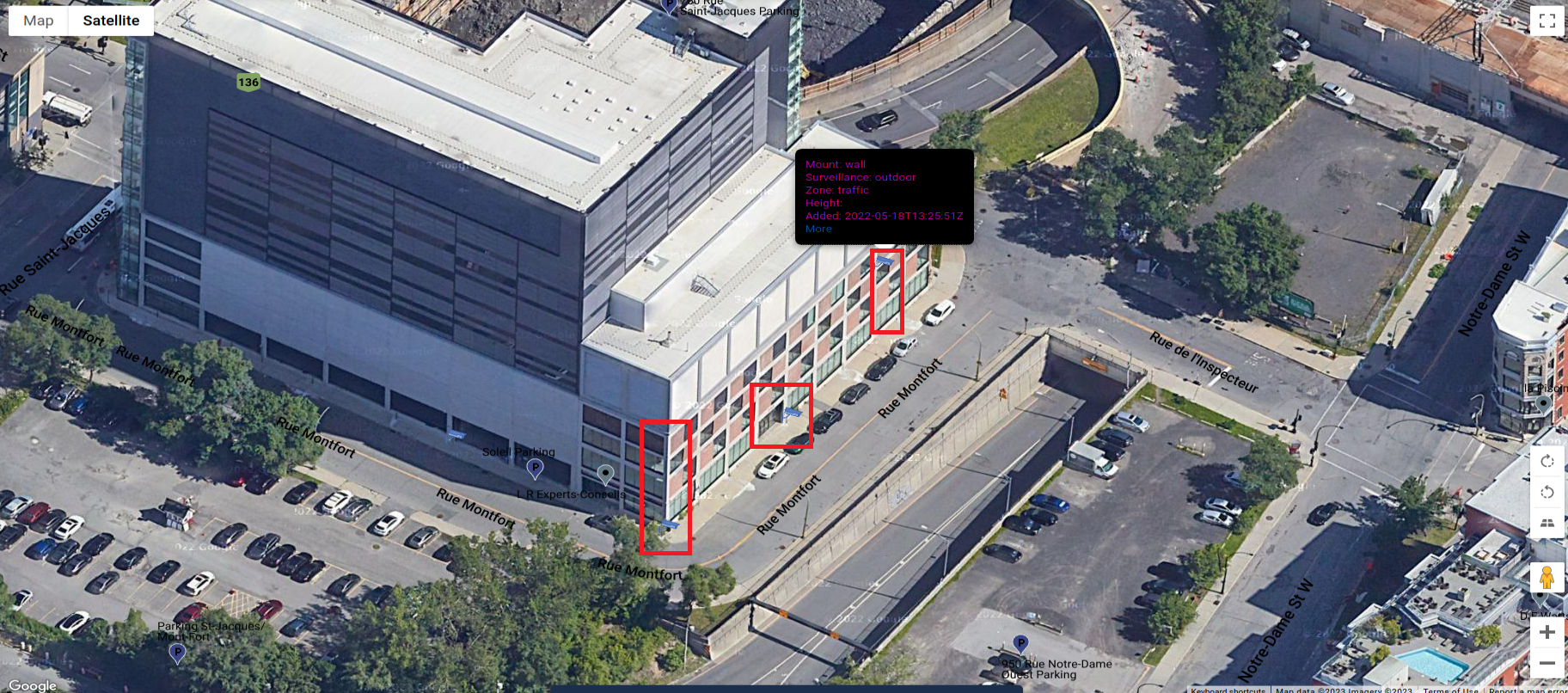
Street view clearly shows cameras in exact same place as on the map.

These devices operates everywhere, on parking spots, near entry of the buildings, on the roofs or poles.
- Street & Weather cameras
Some services gives you live footage of cameras in different part of the cities. It is intended to check for traffic and weather but it has additional meaning for OSINT.
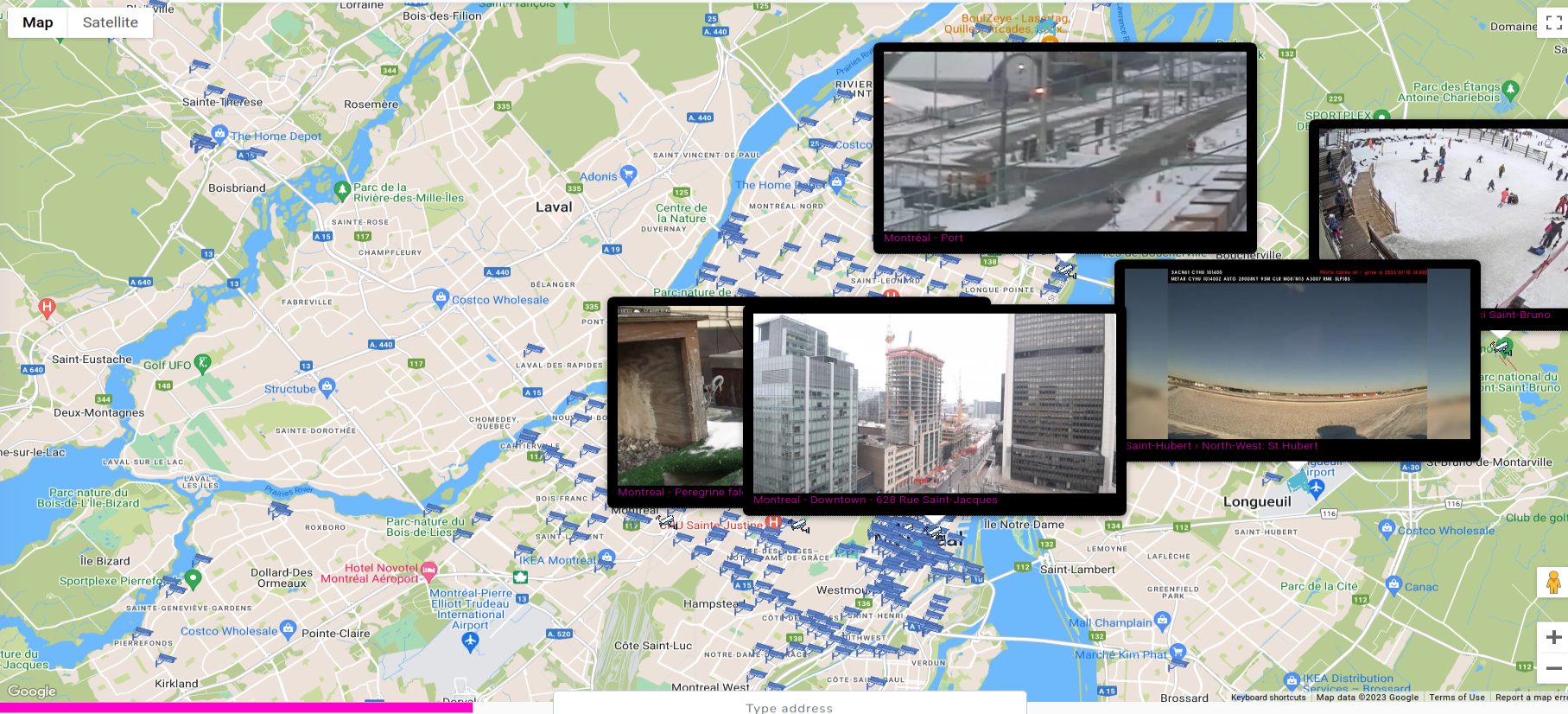
We can find such cameras in the city as well as very remote places, so it's worth to scan multiple times in different parts of investigated location.
Devices
Now, we can experience same feature as in Kamerka (https://kamerka.io) which includes most popular Internet of Things and Industrial Control System devices.
In Open Source Surveillance everything is about geolocation, and some devices might be pinpointed to particular facility where they operate. I've chosen ones that disclose their location, as part of the response, and thanks to this can be geolocated.
More about this technique can be found below

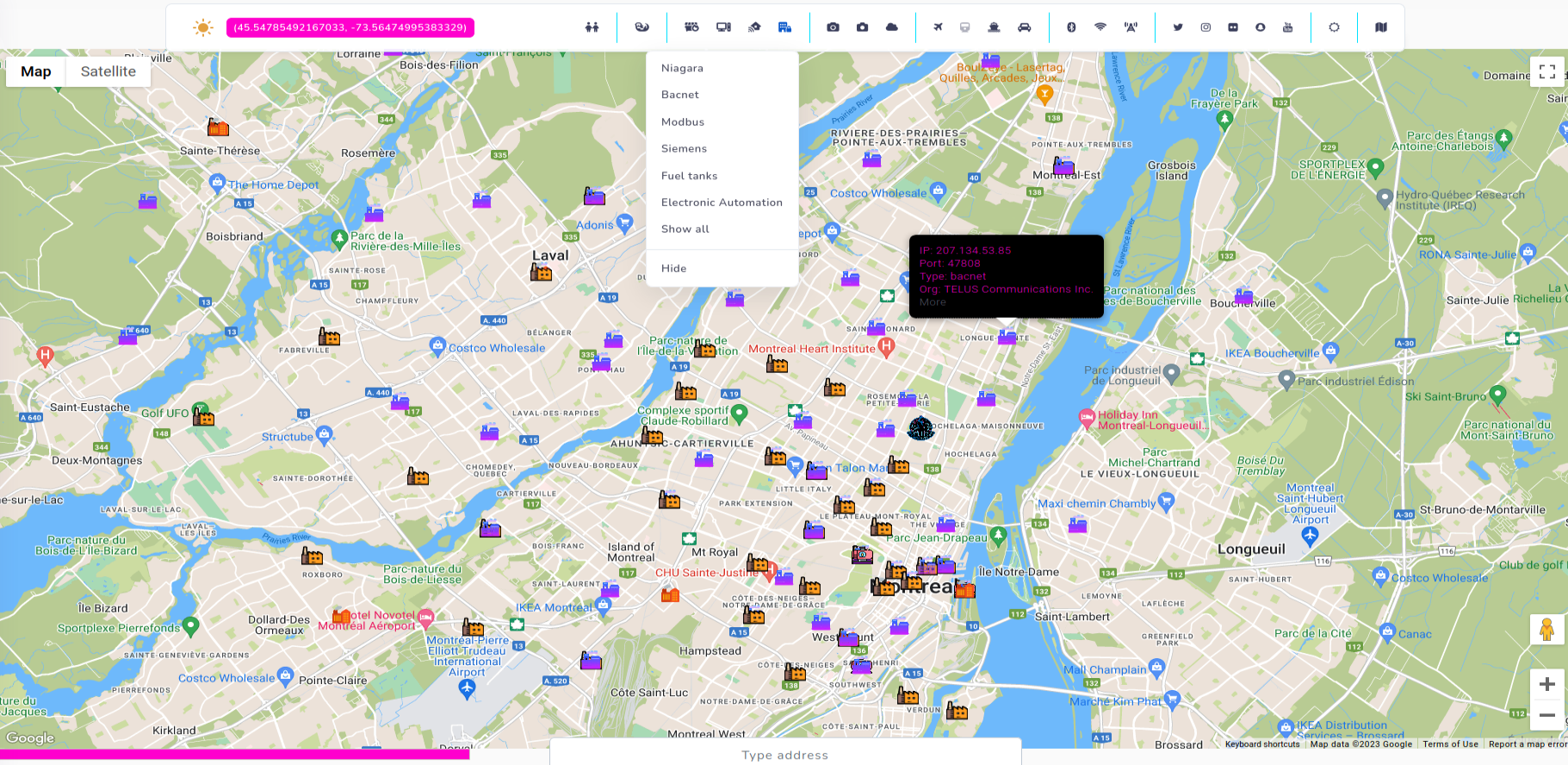
I use this feature in same way as in Kamerka - by searching devices that indicate operating in critical infrastructure or sensitive facilities.
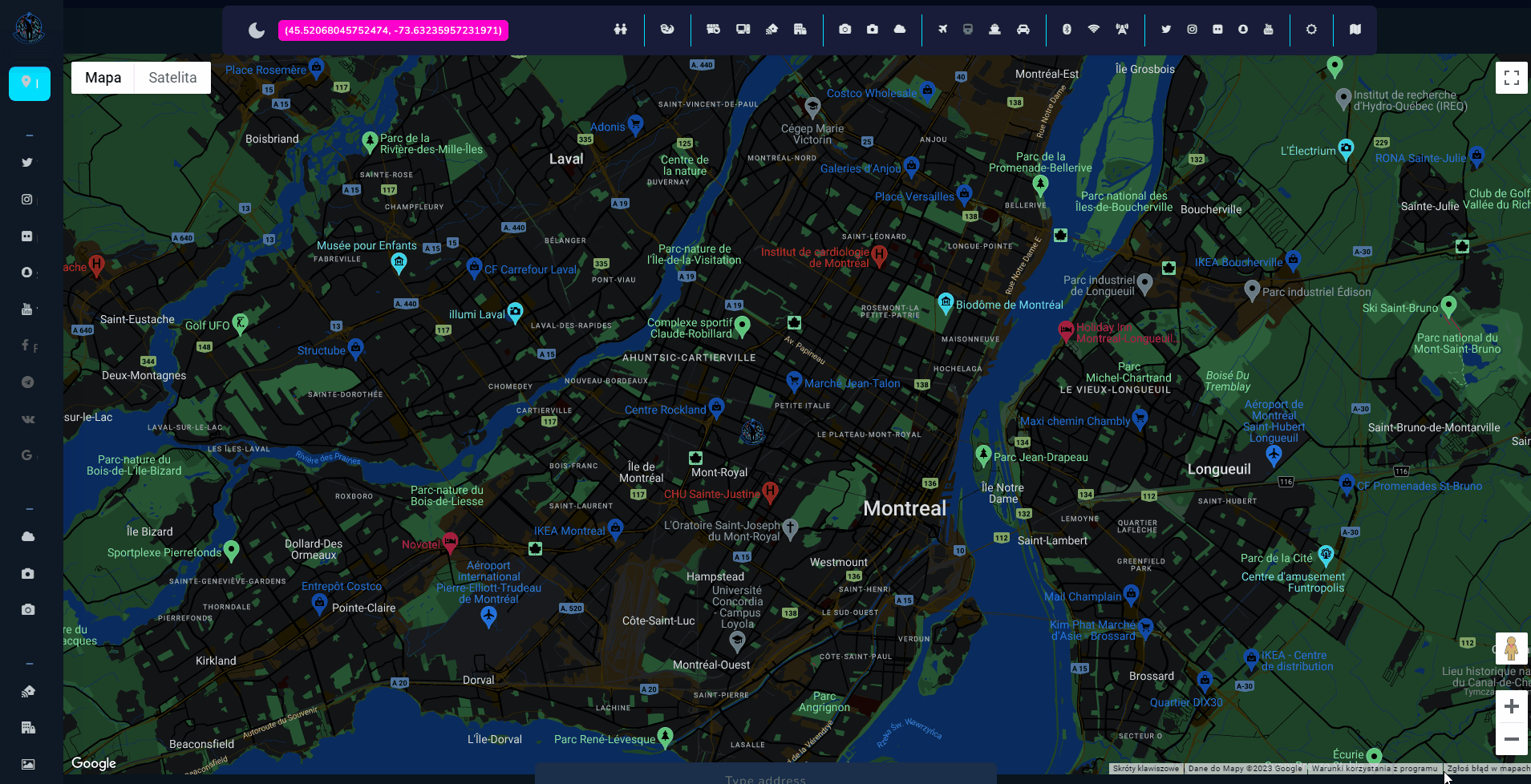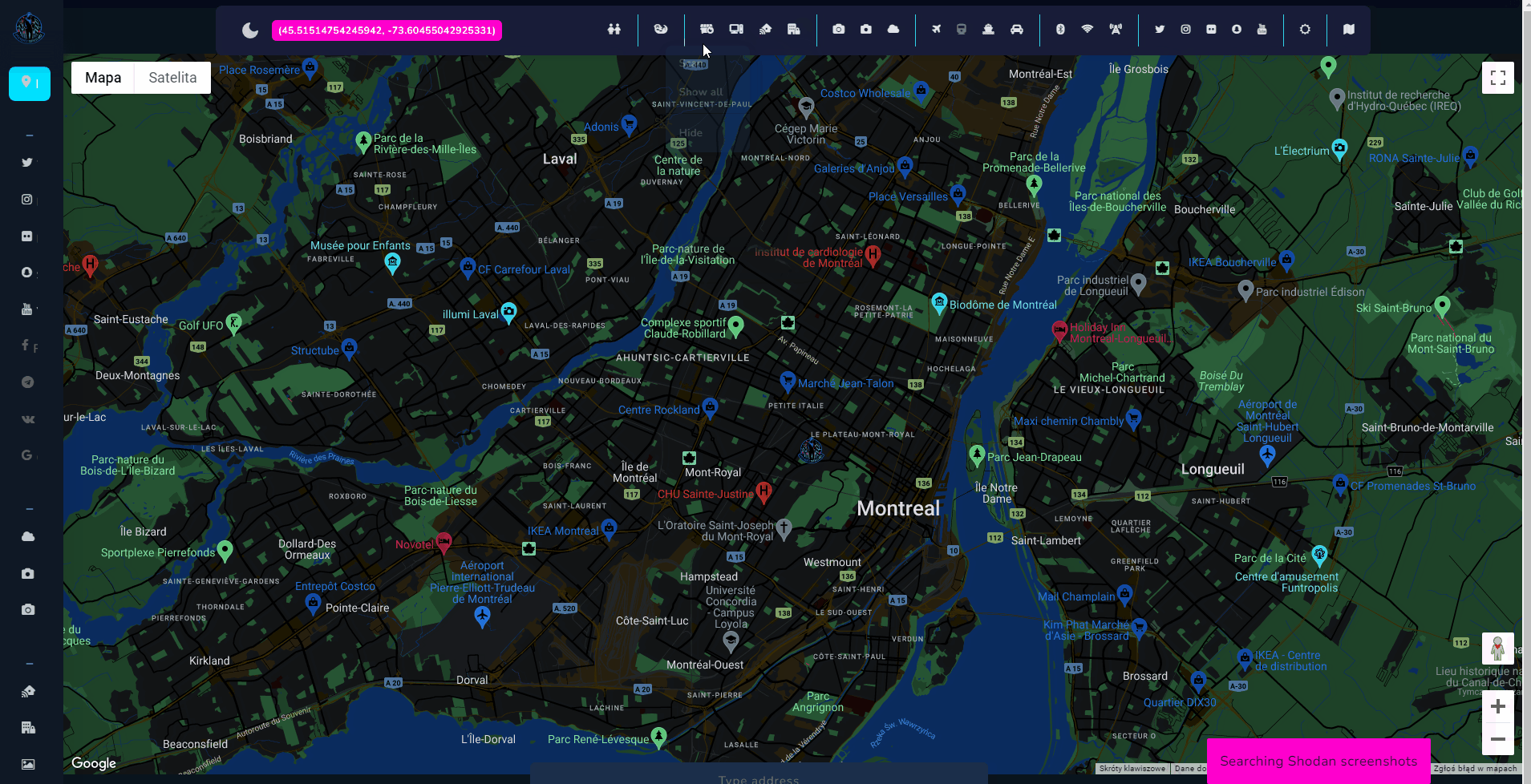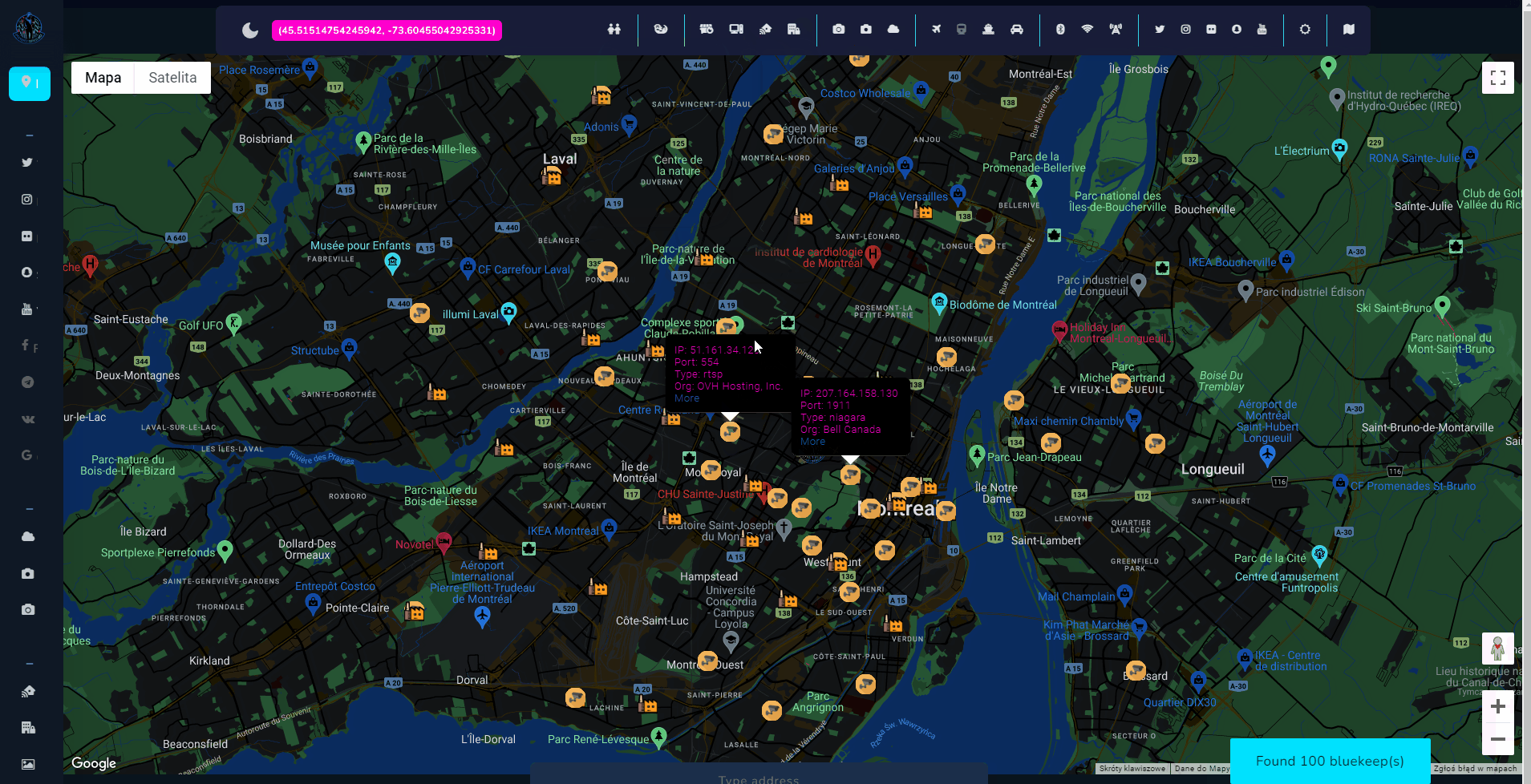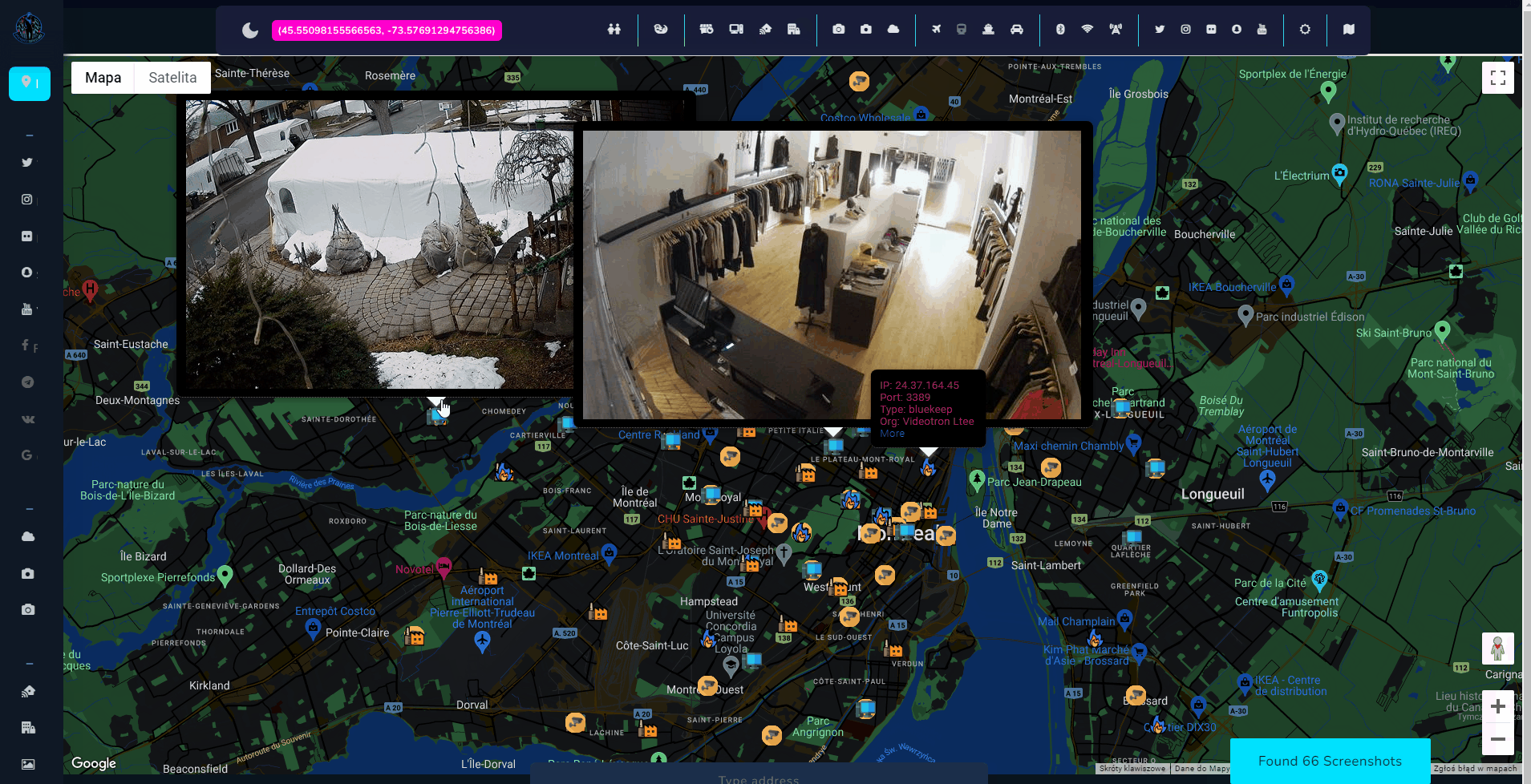
In addition, Internet of Things feature includes RTSP, MQTT, Amcrest or Netwave cameras. Last two are easily hackable and with only one request, we can obtain audio from camera or hijack a footage. If you know more Shodan dorks to collect vulnerable IoT devices, please let me know.
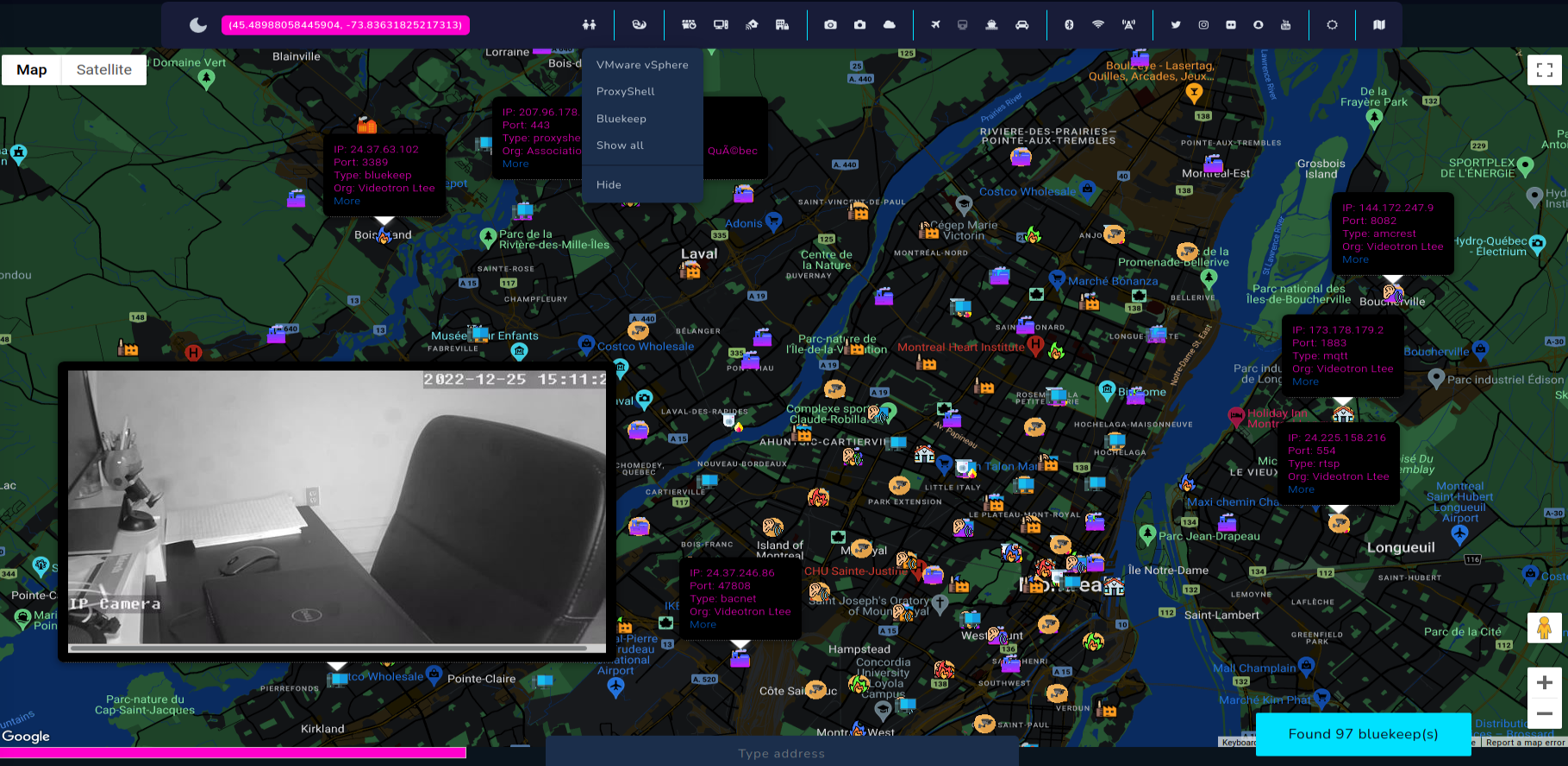
Vulnerabilities like ProxyShell or Bluekeep has been added as part of the Shodan module. It's worth to remember, if finding is placed on the map, it does not matter that it's is located exactly in this particular place. Additional research regarding network, domain, IP, organization, ISP, infrastructure and domains must be performed, however many times IP location is quite right and the vulnerable machines exist physically on given location.
OSS also has a feature to display screenshots, excluding RDP, what gives us live feed from variety of private cameras or VNCs.
Transportation & Weather
Open Source Surveillance is a real-time intelligence gathering tool and transportation must have been one of the feature. It shows live traffic from Google and location of planes and cruises. It also, same as Wigle, works on bounds, so you must zoom in or out to search on specific place.
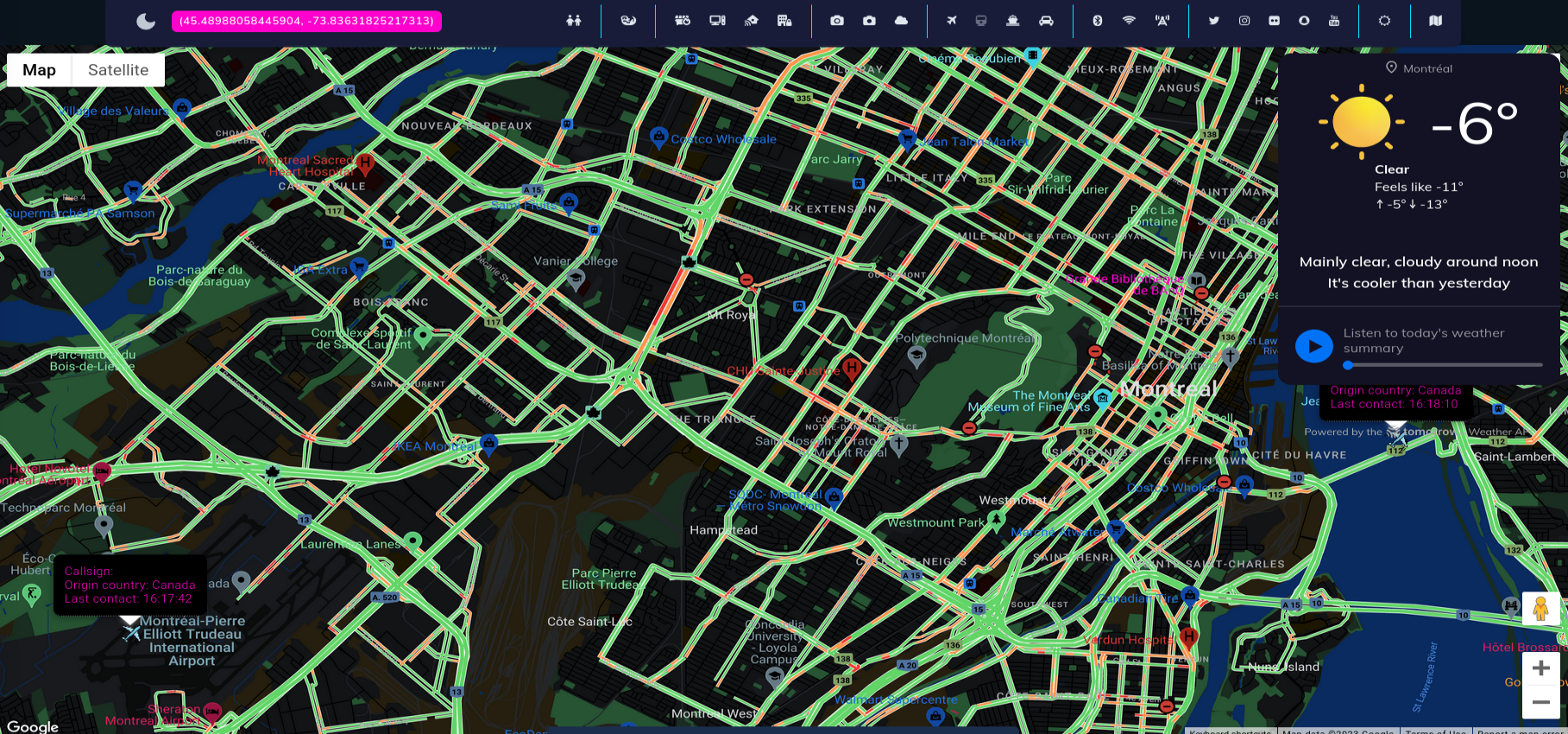
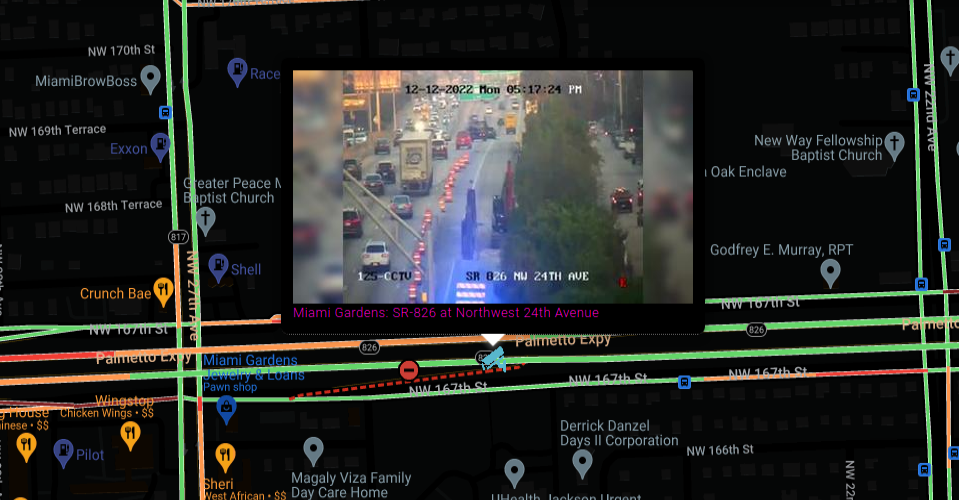
Google is very accurate, and feed that you get from cameras are indeed live. Below screenshot confirms it 100%, according Google, part of the road is unavailable and footage from one of cameras shows exactly same thing.
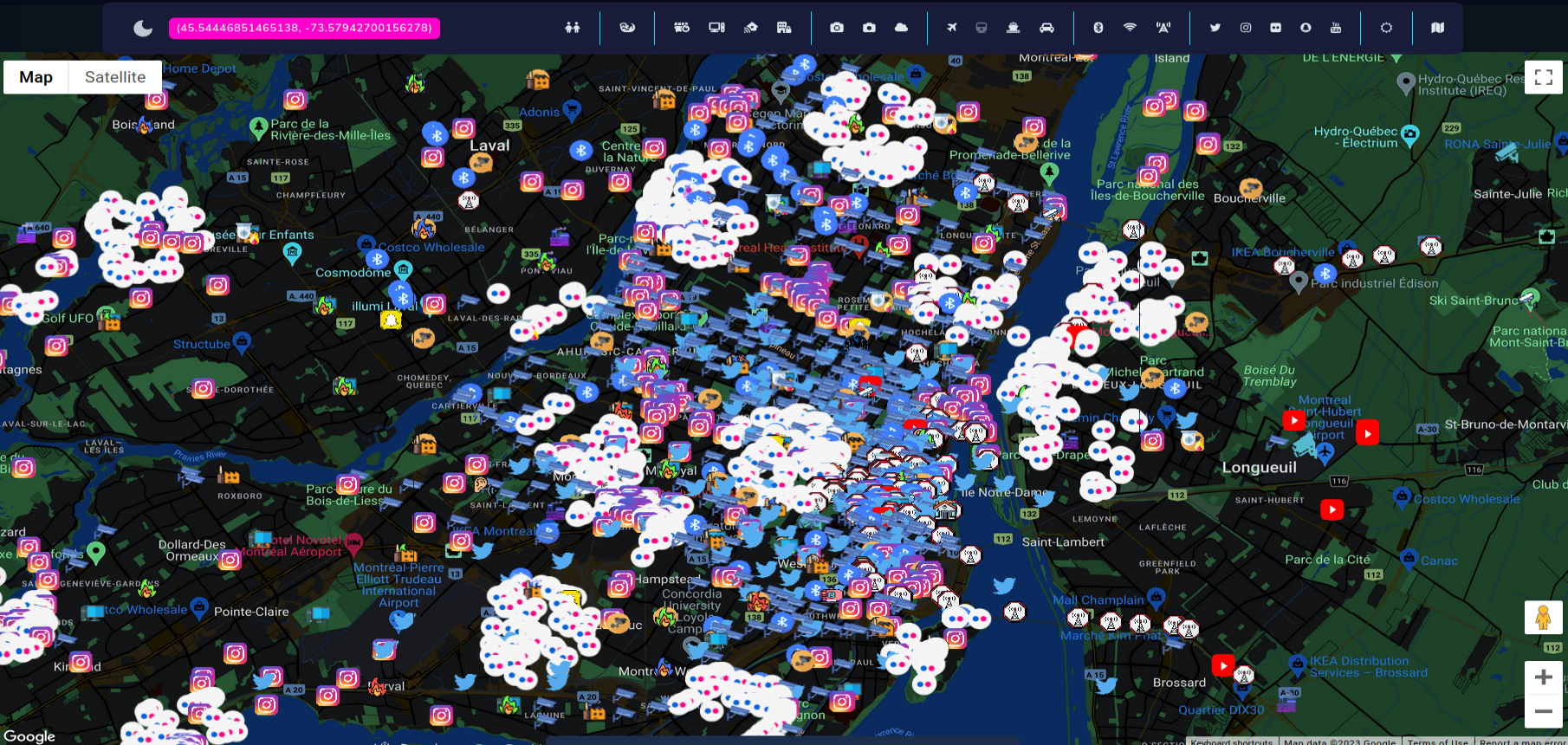
And that's how it looks everything combined, however we didn't explore whole city and most sensitive places. It was just small introduction and tutorial, but with some imagination you can do amazing things with this tool.
I have a plan to implement more modules, so if you have any feedback about new social media or real-time data source, let me know.
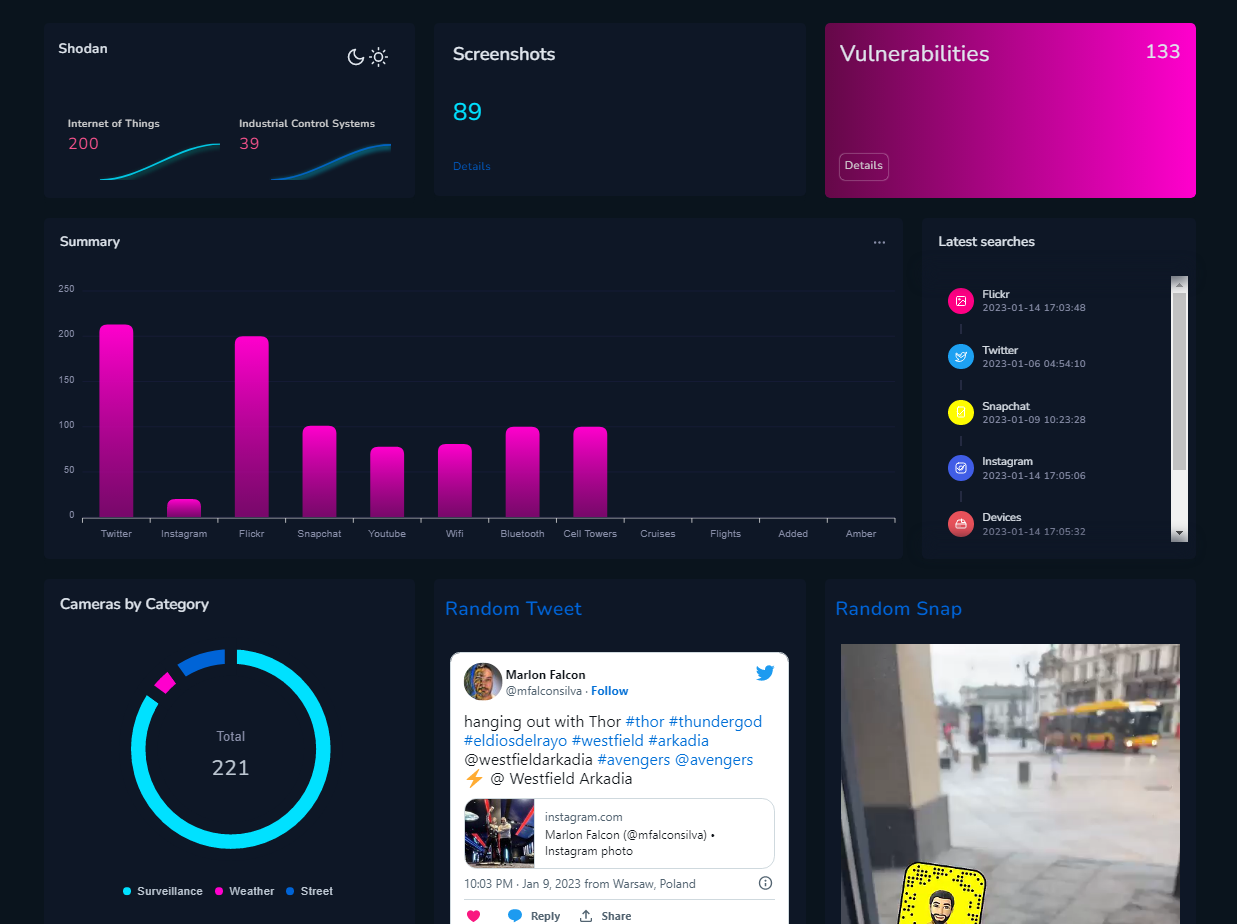
Dashboard
Clear dashboard will help to sum everything up. It presents amounts of findings from each category, on a different charts. Moreover, it lists random Snap, Tweet and timestamps of latest social media searches.
We've finished this long user manual and now can get into real world investigations.
Real world cases
First of all, it is interesting experience to see the city from this perspective, you can find very amazing staff, but the real fun starts when you are actually looking for something, it might be a geolocation task, tracking evidence on the ground or securing IoT/ICS devices.
There are many possibilities to use the tool so I just present couple cases I work on during tests of Open Source Surveillance.
#OSINTForGood
On 8th of January in Brasil, Bolsonaro supporters raided Congress, Supreme court and other presidential offices during riots in capital. Below is the live view of the event.
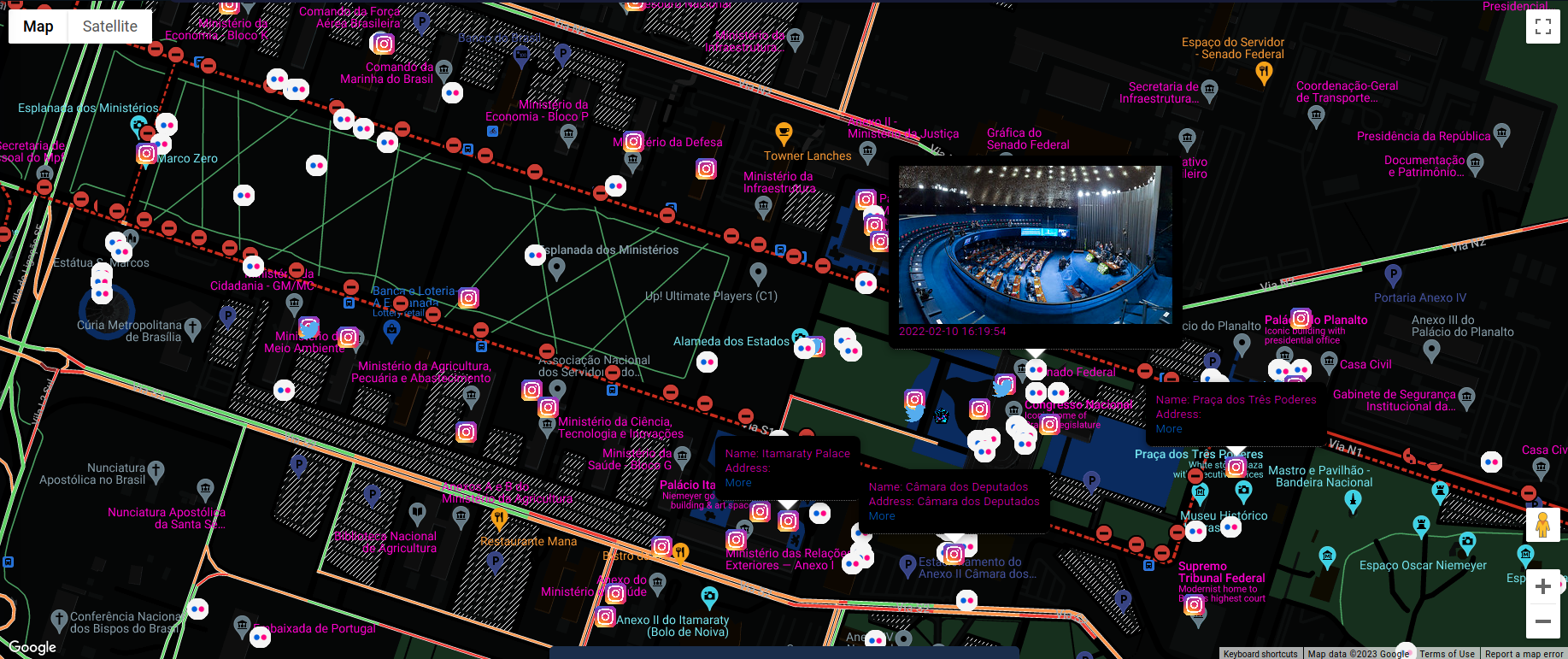
In includes feed from Twitter, Instagram and Flickr - more services will come in next update, however it's still enough to gather necessary evidence and get inside look on the event though.
Tweets with geolocation show videos or photos where it was taken. It of course contains timestamp so you can do a timeline of events based on the found media.
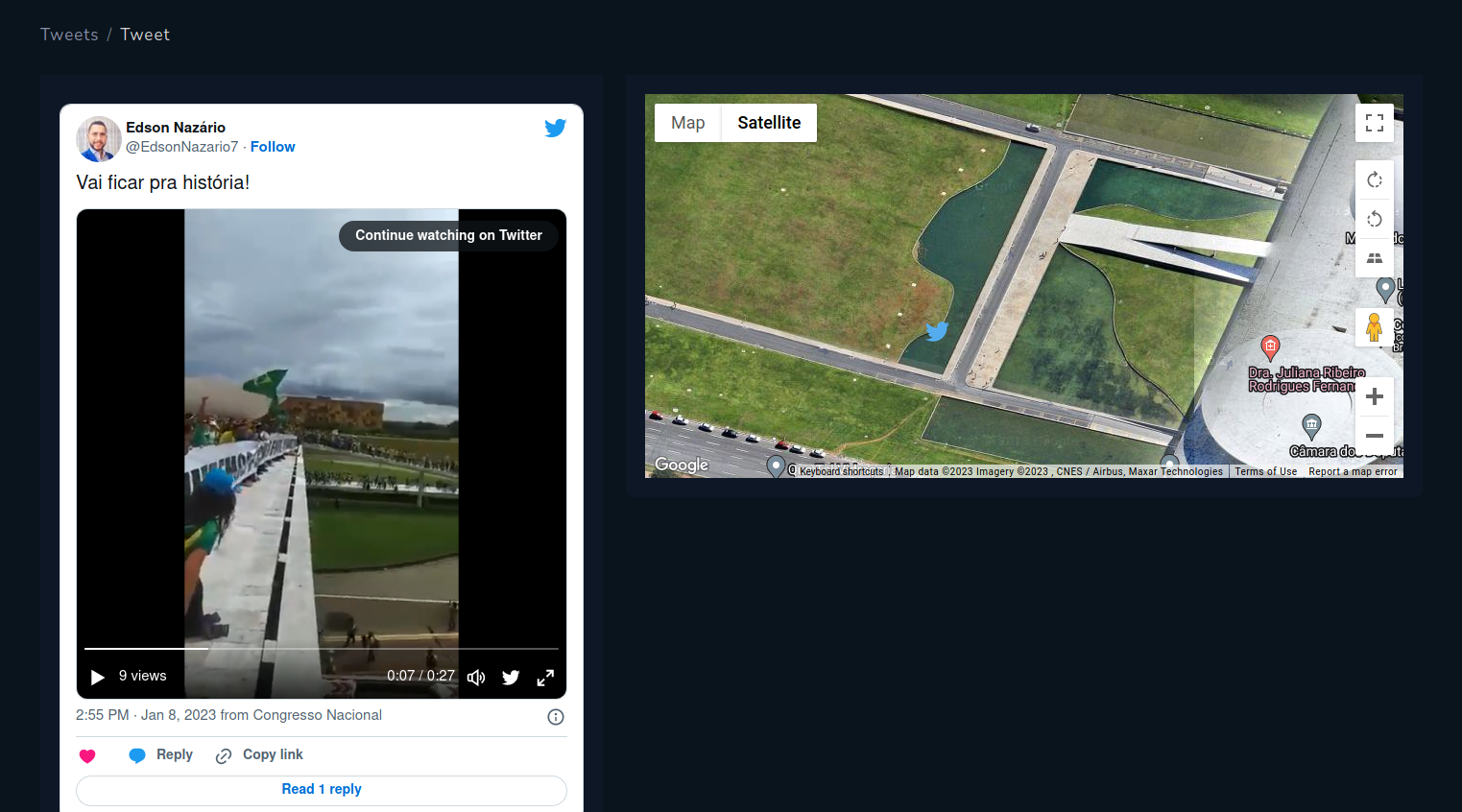
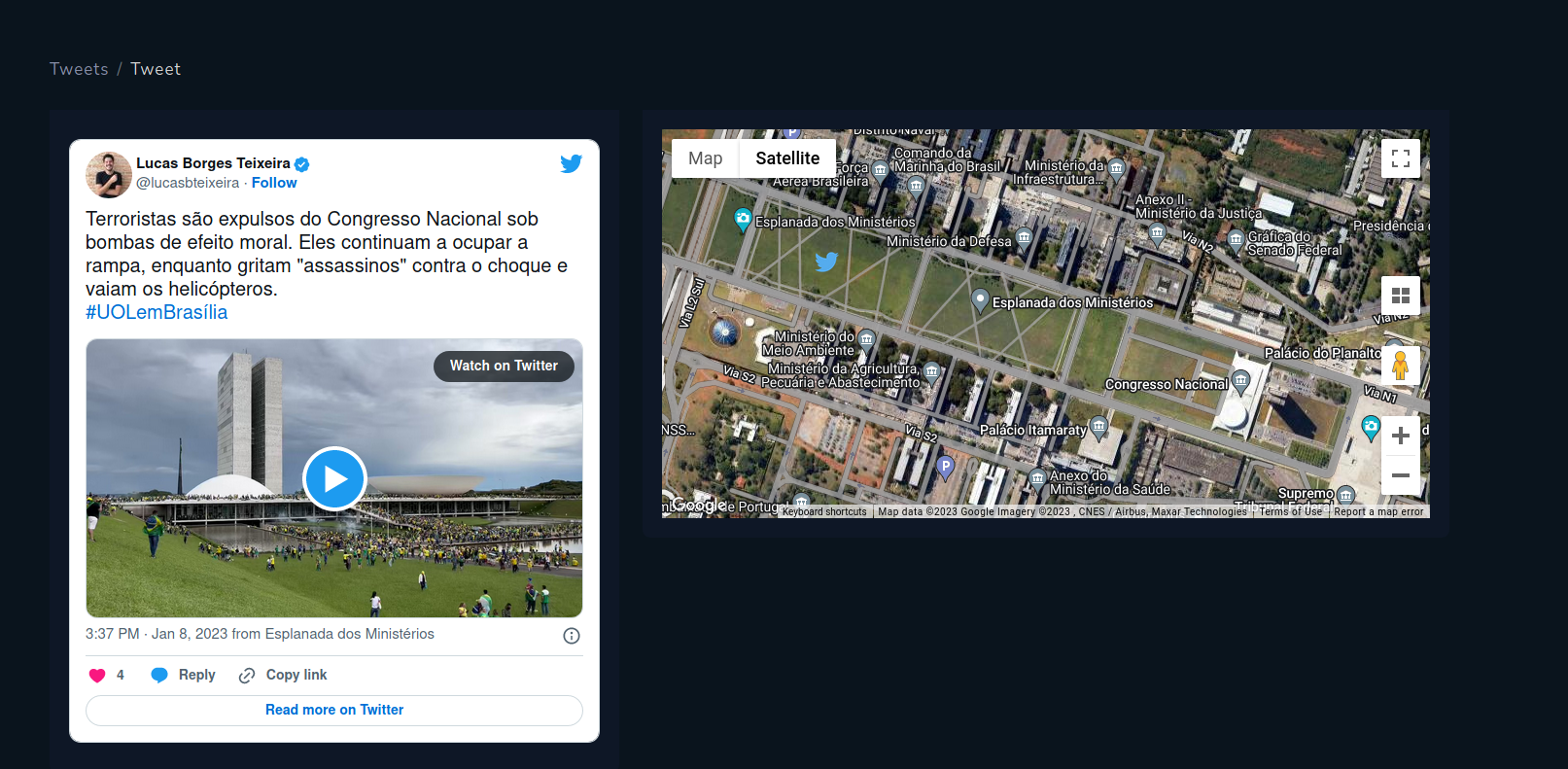
Geolocated Tweets from protest in Brazil
Instagram also allows to sort posts by recent and explore it on given location. Screenshots below show photos from places where protest happened.
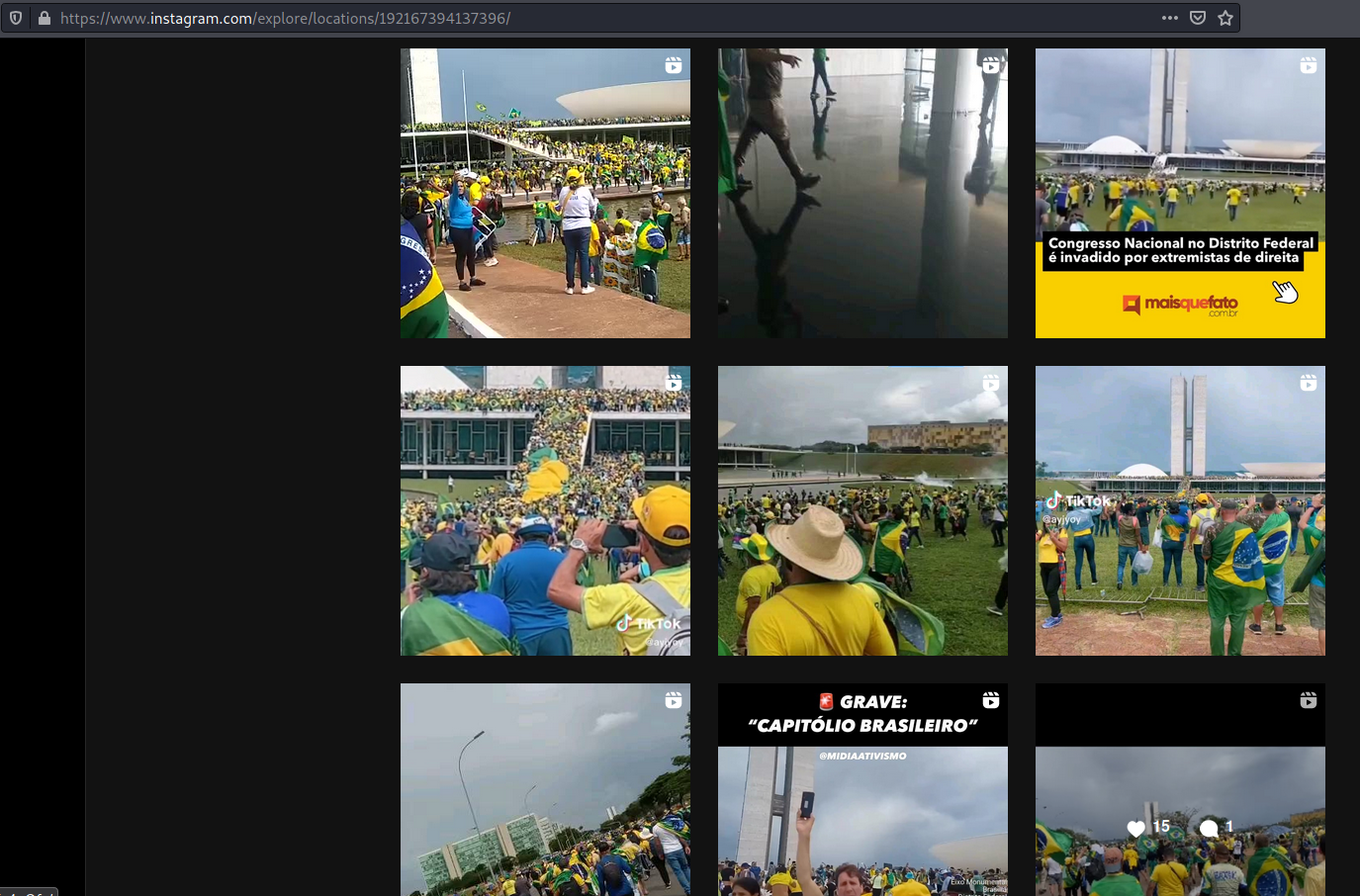
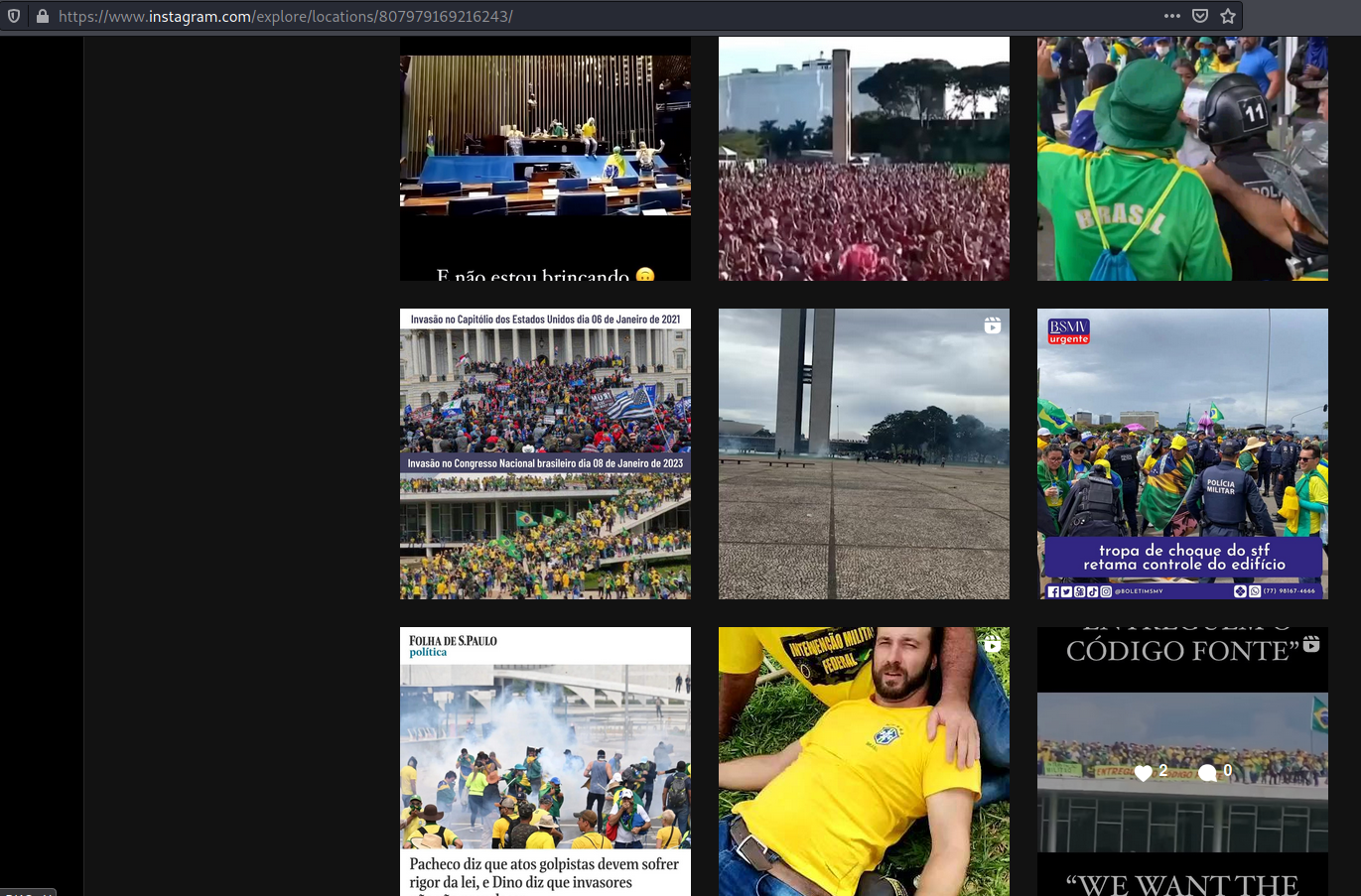
Instagram places from protest in Brazil
Moreover, Flickr gives you all available photos, even ones from couple years ago. In this case, it was useful for me to compare damage that rioters done with normal photos of Presidential Palace.
Only these three services were available during this event, but Snapchat, cameras or hackable devices are still accessible when needed. To collect deeper intelligence about some events or city in general, one needs days if not months of preparation, but with couple clicks it's easy to gather enough evidence to proof misbehaviour of individuals and establish timeline of events based on timestamp and geolocation.
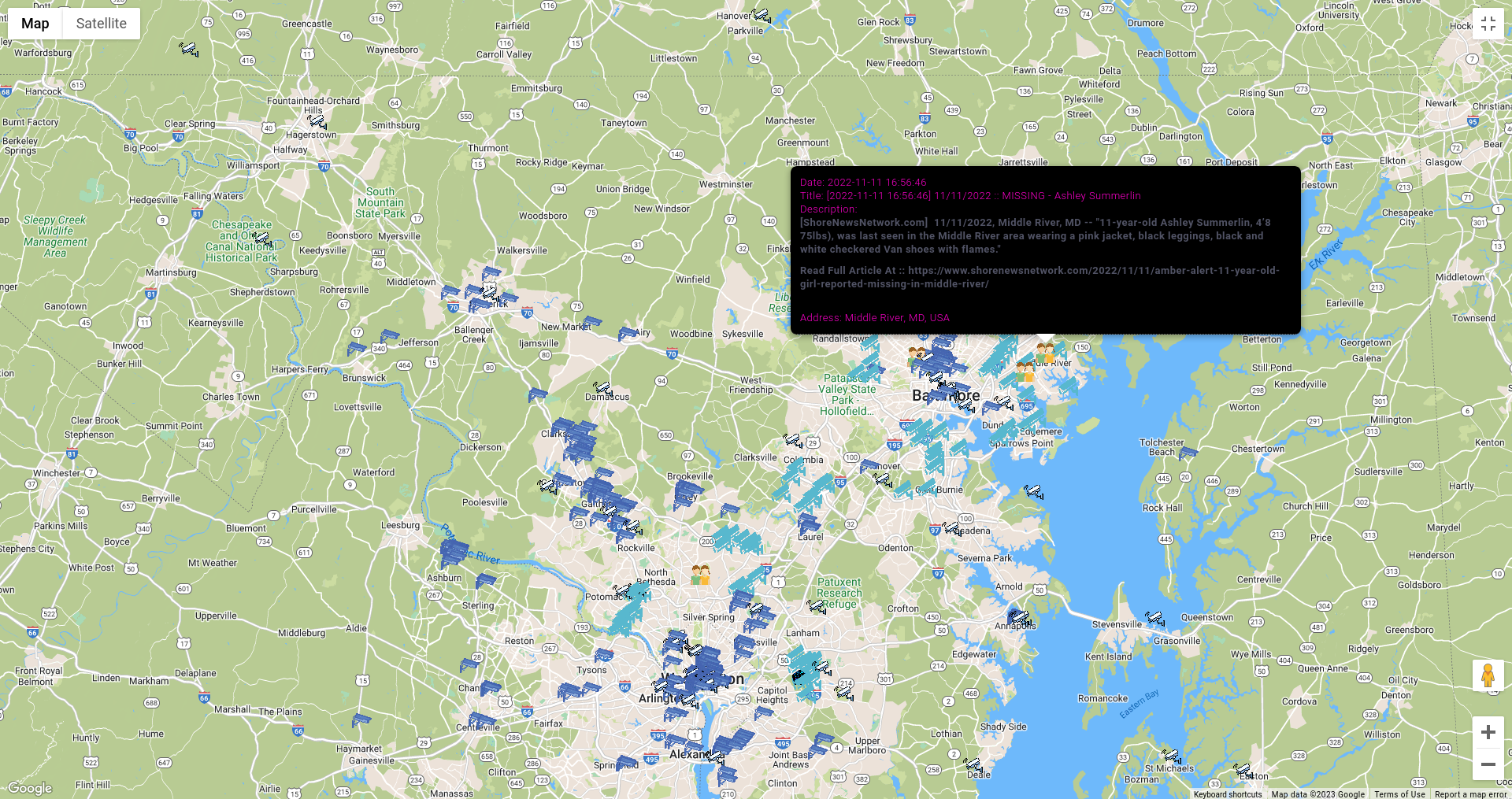
In addition, you can display latest Amber Alerts in United States. You never know how many online and physical leads bad actors left behind, and with help of OSS and additional manual research you can help in variety of cases like human trafficking or Amber Alerts.
#OSINTForEspionage
Offensive OSINT blog is about using Open Source Intelligence in offensive way, and creating OSS I had couple ideas how to use it this way. As many of such tools, this can be abused as well, for stalking, getting unauthorized access to networks and devices, spreading disinformation or espionage.
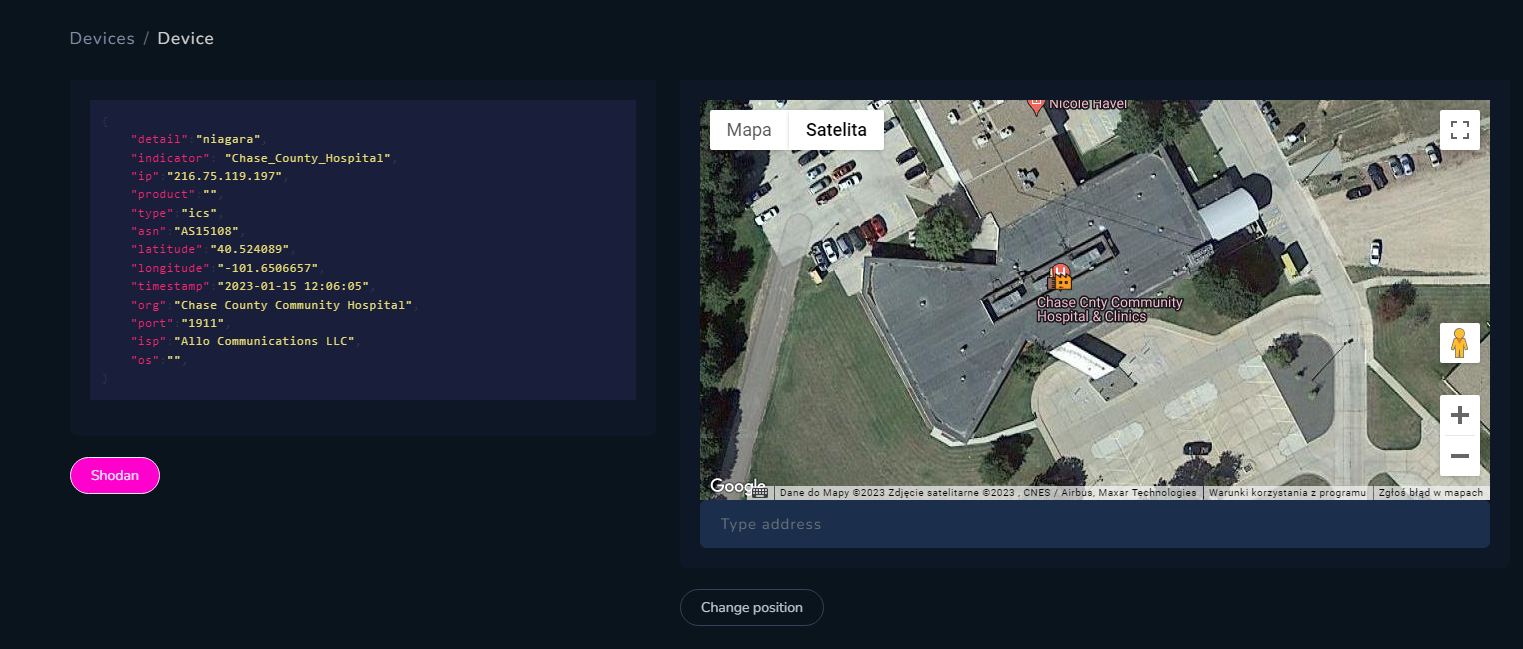
In the past, I did research about Internet exposed IoT and ICS and how one can abuse it and easily gain access to the device, via exploit or password guessing. In addition, it's not hard to find variety of devices operating in different facilities and infrastructures. Let's take a look on example.
Screenshot feature gives you photo straight from the device indexed by Shodan, it might be camera, VNC and other, excluding RDP due too many results. Also with help of ICS module you can search for Modbus, Bacnet or Niagara servers, which shouldn't be exposed directly to the Internet.
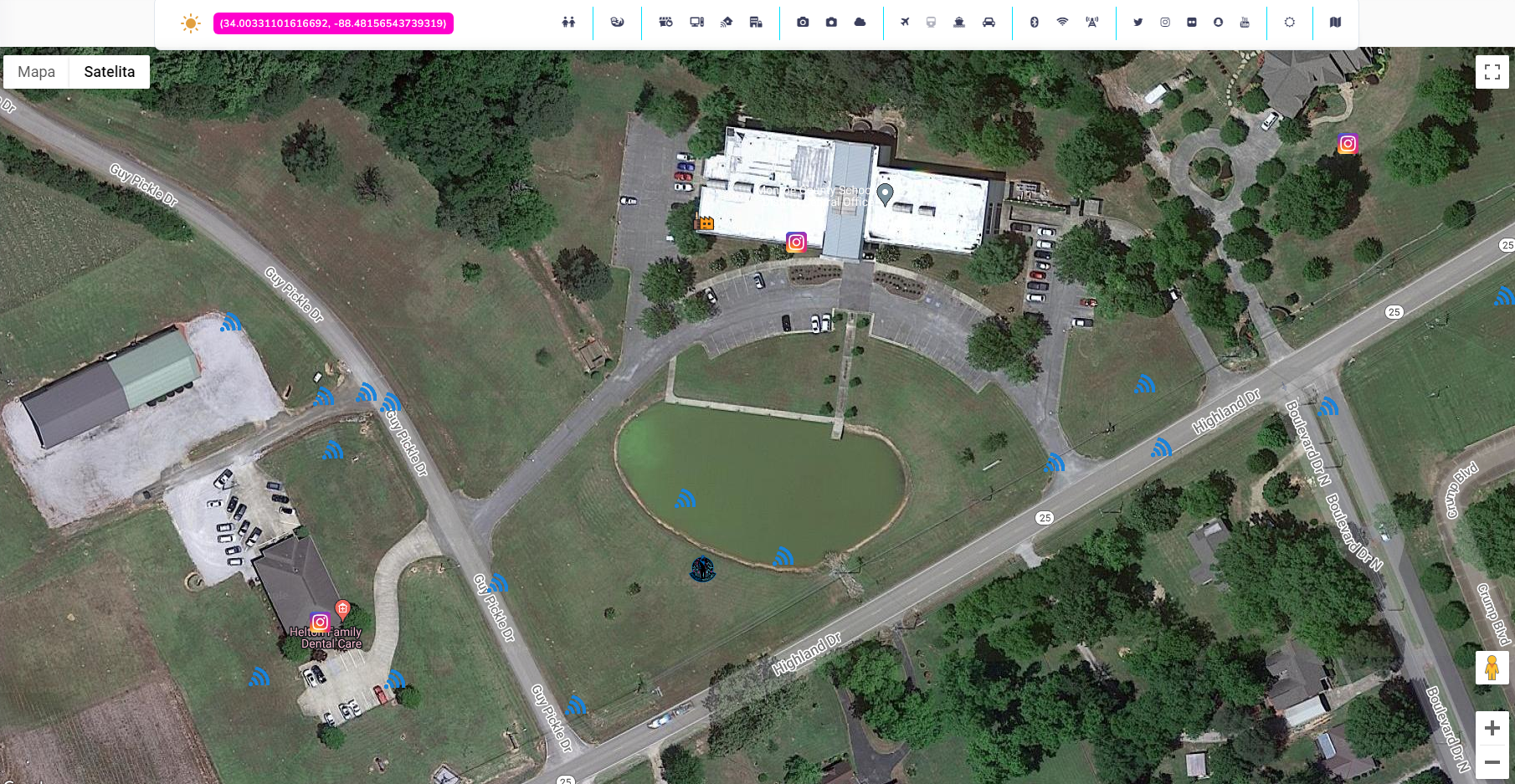
I came across picture from one of Internet connected camera that presents something what looks like part of wastewater treatment plant or hydroelectric power plant infrastructure.
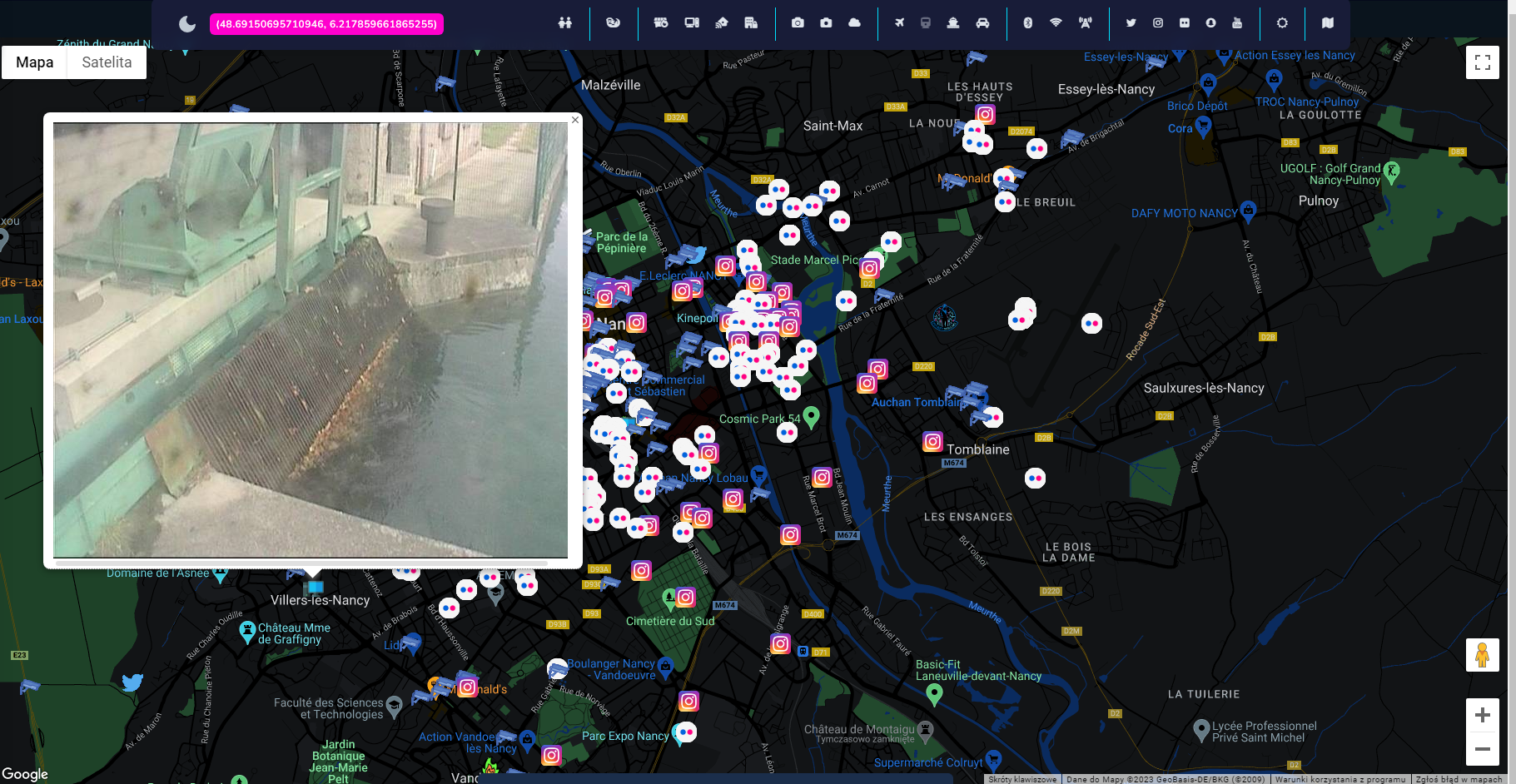
OSS contains links to Shodan for each search results, so we can quickly check what is operating on this host except the camera.
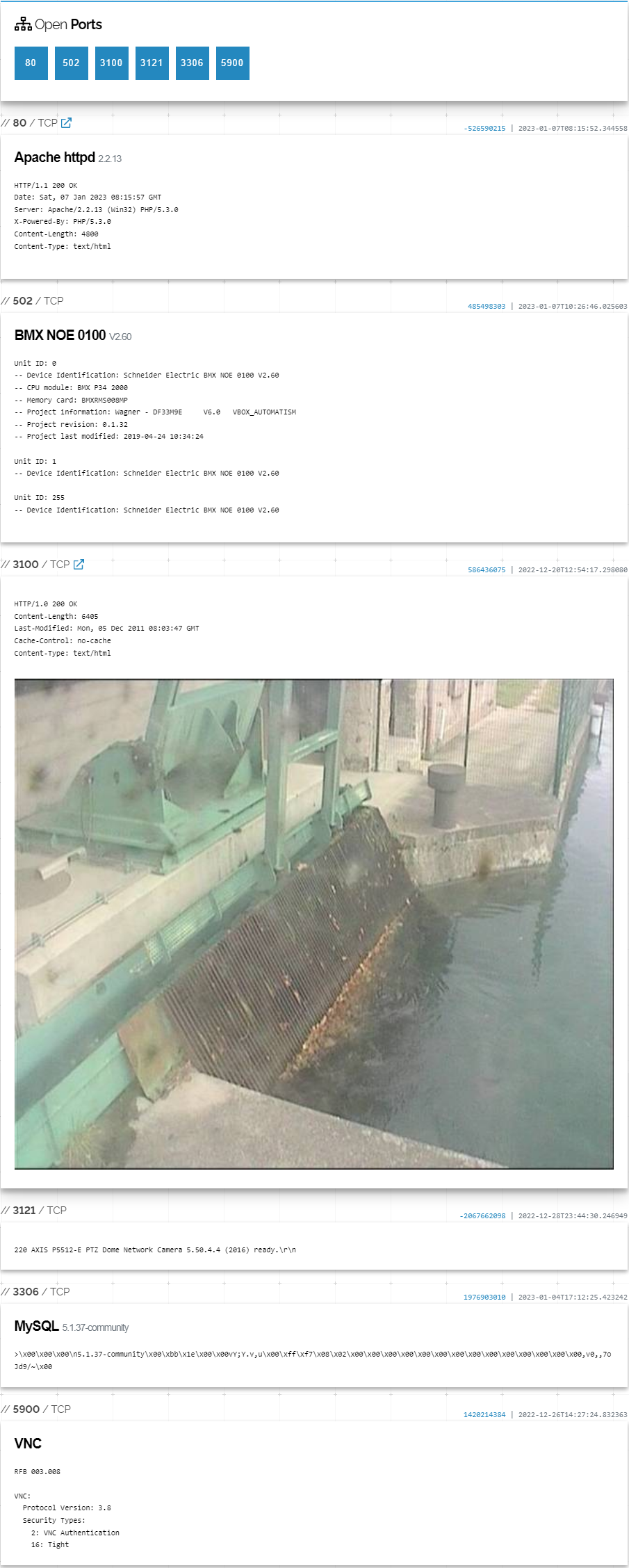
It's perfect example how to not administrate network and critical infrastructure. VNC, MySQL, Axis Camera, Modbus on port 502 and HTTP server on port 80.
The last one is quite important because it resolves the mystery of what nature infrastructure it is.

Trophy for the one who bet on hydroelectric power plant. Unfortunately, I wasn't able to pinpoint it to exact location.
Don't get me wrong, such misconfiguration does not mean that device is vulnerable and even after somehow getting access, most probably you won't be able to do much damage, however it is a bad practice and security issue to connect such machines directly to the Internet.
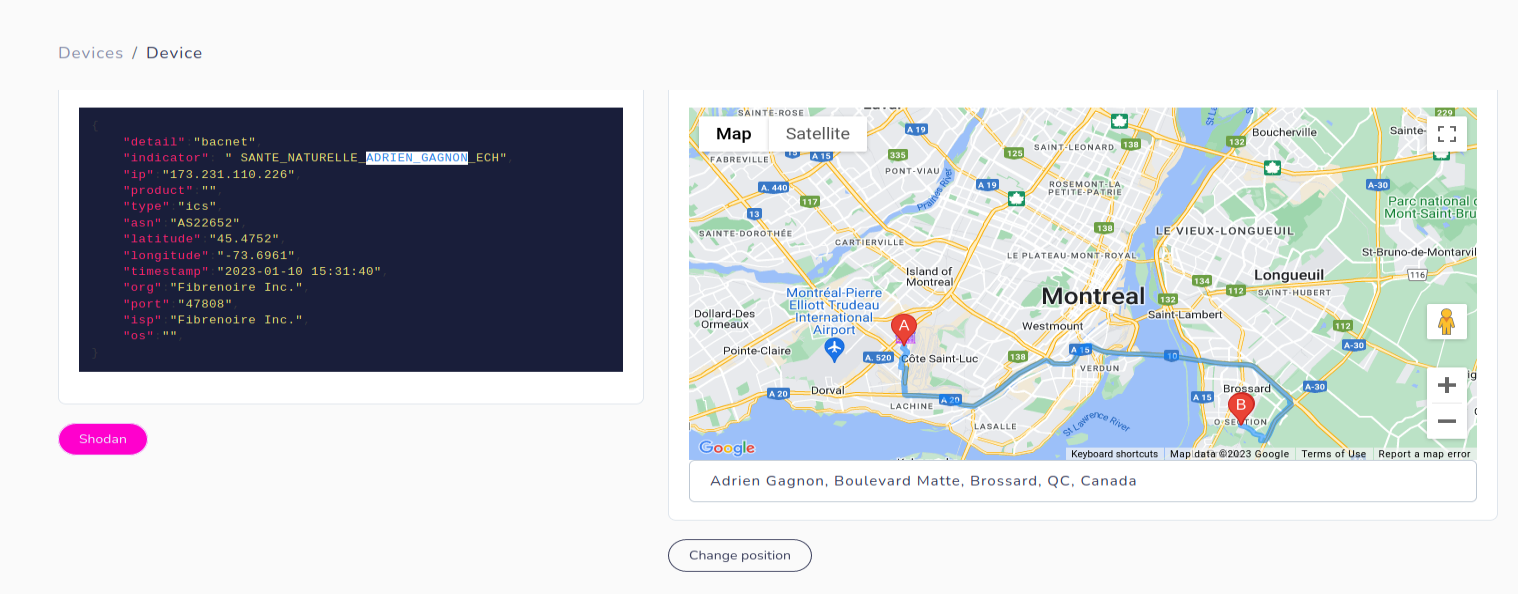
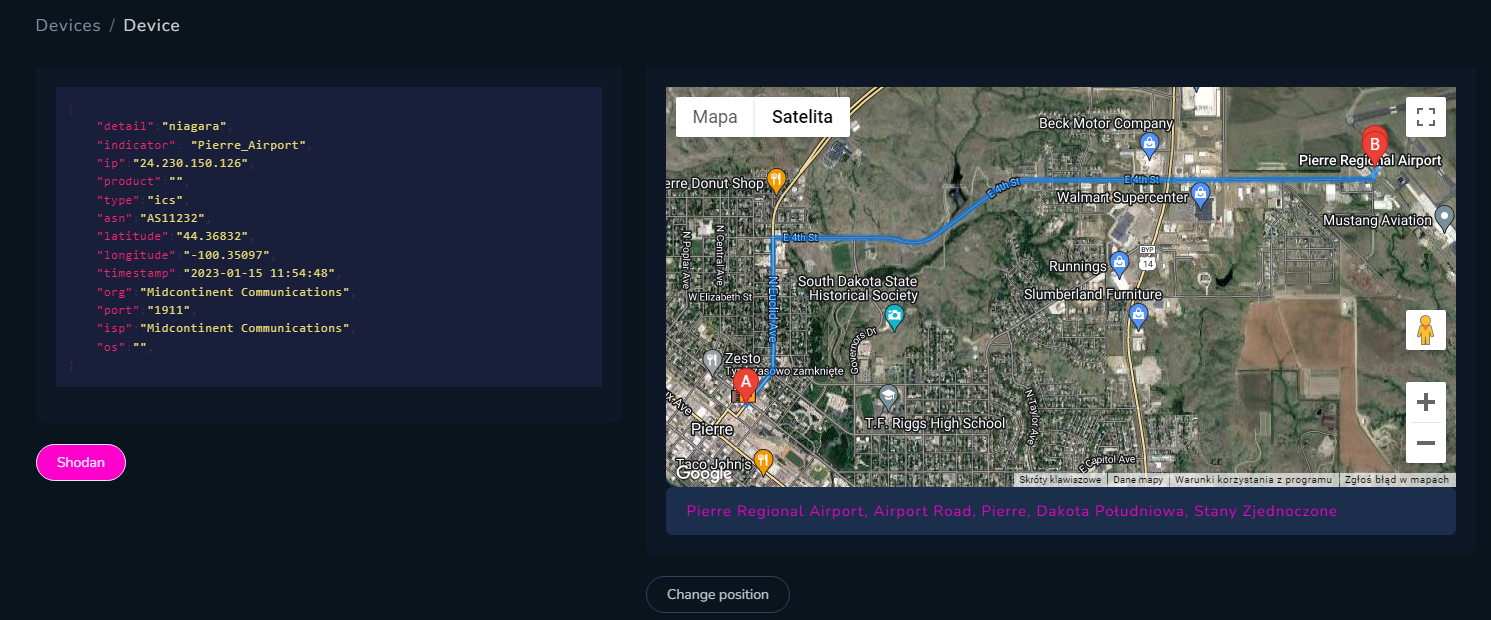
In most cases, it's easier to find facility where device is running, for example Tridium Niagara includes "station name" in the response, which sometimes contains name of specific building. Such devices work everywhere - in government complexes and offices, airports, hospitals, water treatment plants, schools, churches and more.
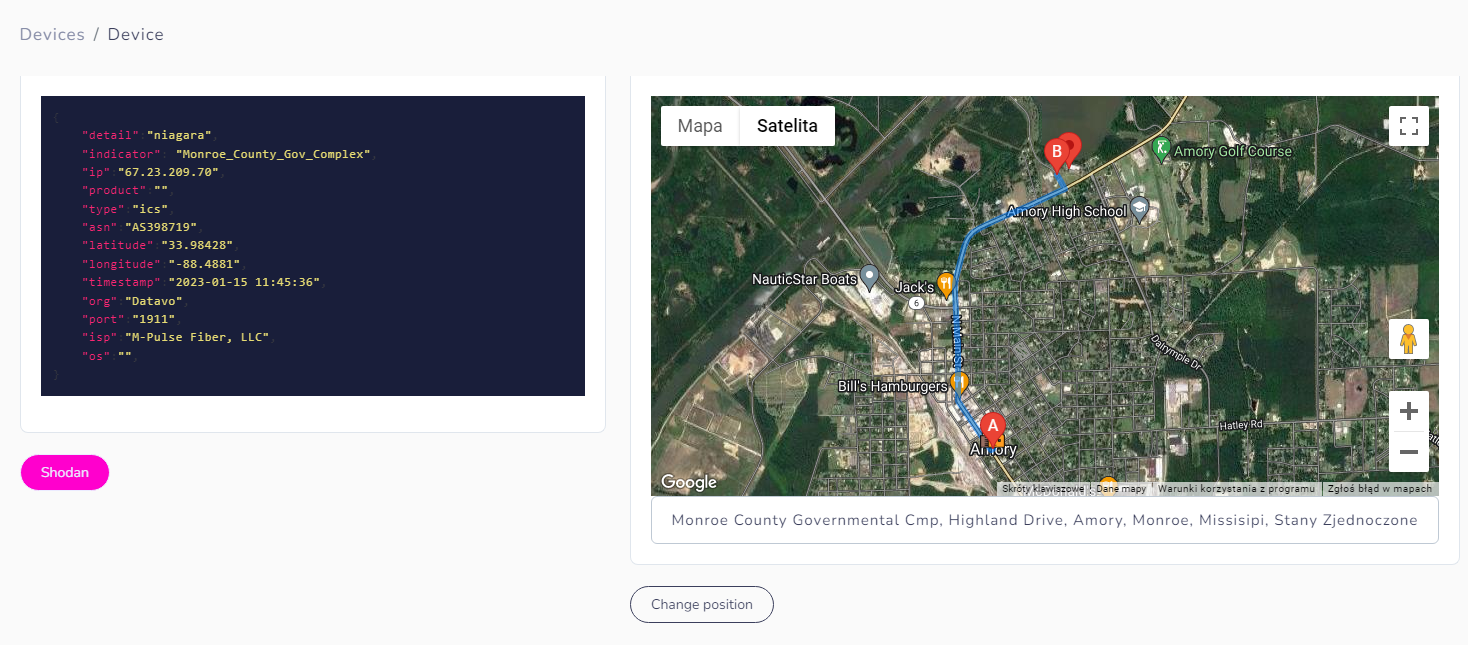
Indicator from device points to Monroe Country Gov Complex and it's located very closely to the location from IP geolocation database.
We changed position of the icon and now it's displayed on the complex where device is operating. From there, we can scan for WIFI networks, looking for photos from Flickr or Instagram and also search for cameras.
Another example can be field "Project information" from Bacnet devices. It shows path to the project, which includes the name. Knowing that IP points to Australia and indicator points to "Eromanga WTP" (Eromanga, yes it's real village in Queensland)
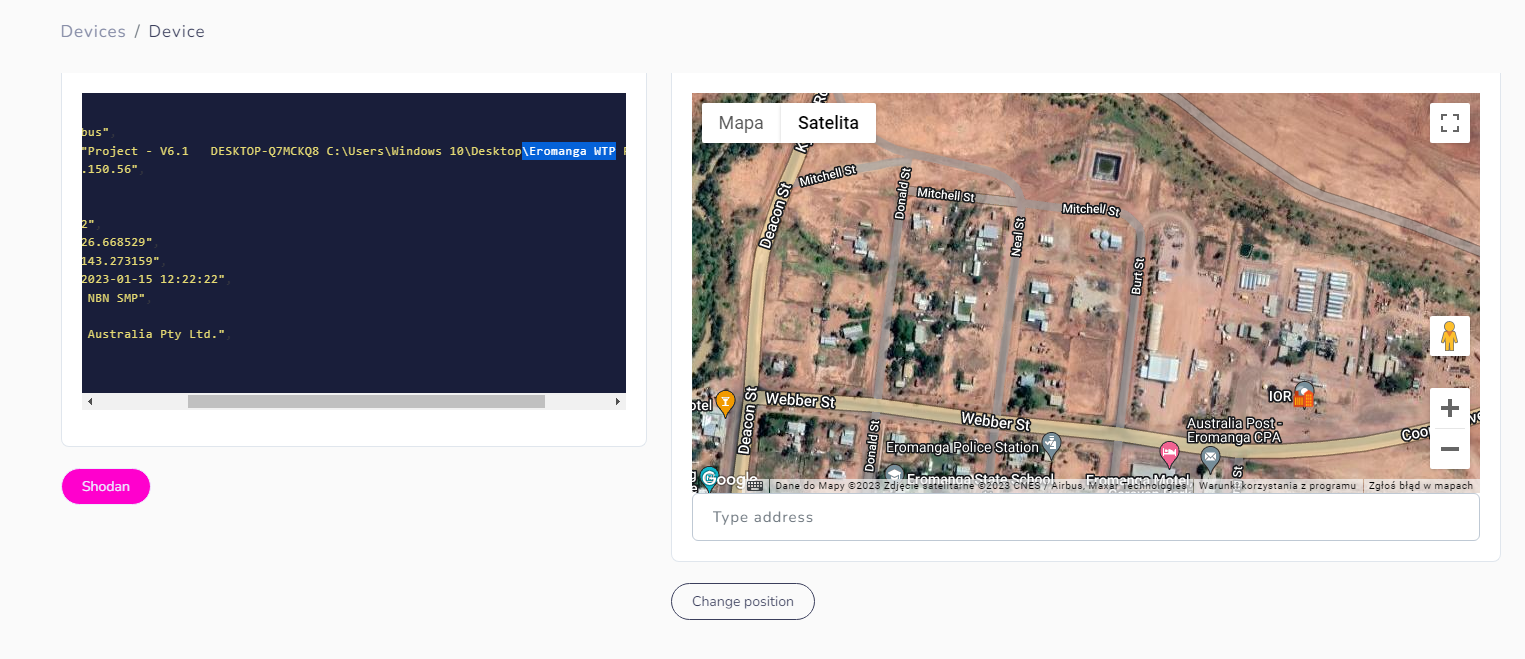
It's quite remote place and even google doesn't know about the Water Treatment Plant there, so I had to look for some official documents to find the facility.
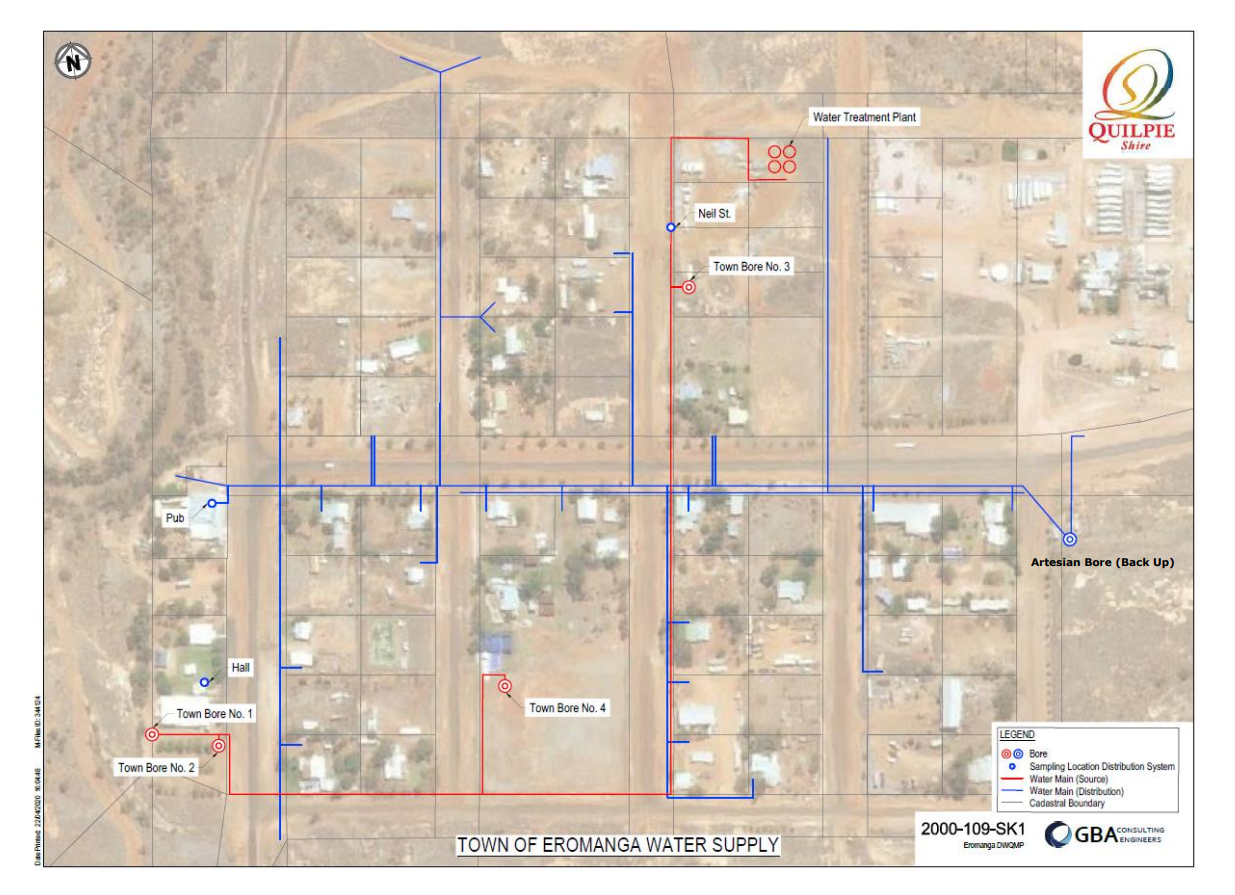
To know more, we can proceed with further search for networks, photos or cameras.
Some more geolocated facilities
In most of bigger cities there are more that 100 Tridium devices to geolocate and potentially compromise by password bruteforcing/guessing. To make your intel gathering as successful as possible, you have to dig deeper and check other services running on machine, WHOIS information or scan the netblock IP is located in. In majority, it's enough to collect info that will allow to find exact location.
Except ICS, you can also scan for IoT devices, which some of them are very vulnerable. Amcrest allows for unauthorized audio streaming and Netwave discloses password for everyone.


More about exploiting IoT you can find here

There are literally hundreds of exposed IoT devices like routers, smart homes, cars, doors, intercoms, printers as well as ICS - Programmable logic controllers, Human to Machine Interface, Wind Turbines, Building Management Workstations and many many more, which I will present in next articles.
At the end, Open Source Surveillance supports searching for very well known exploits like Bluekeep, ProxyShell or for vSphere. Based on additional reconnaissance, you can specify if vulnerable IP belongs to company or organization at your target location. Vulnerable hosts are marked as fire icon in different colours on the map.
#OSINTForFun
Another example how to be creative with the tool might be WIFI network correlation of some companies or buildings. From leaked, by Wikileaks, documents dubbed Project Atlas, we can get acquainted with "secret" Amazon warehouses and data centers. I choose one of such facility in Broadman and scanned it with WIFI module. One SSID brought my attention "a2z_employee".

So I decided to look for the same network name in whole United States hoping to find more building and warehouses associated with them.
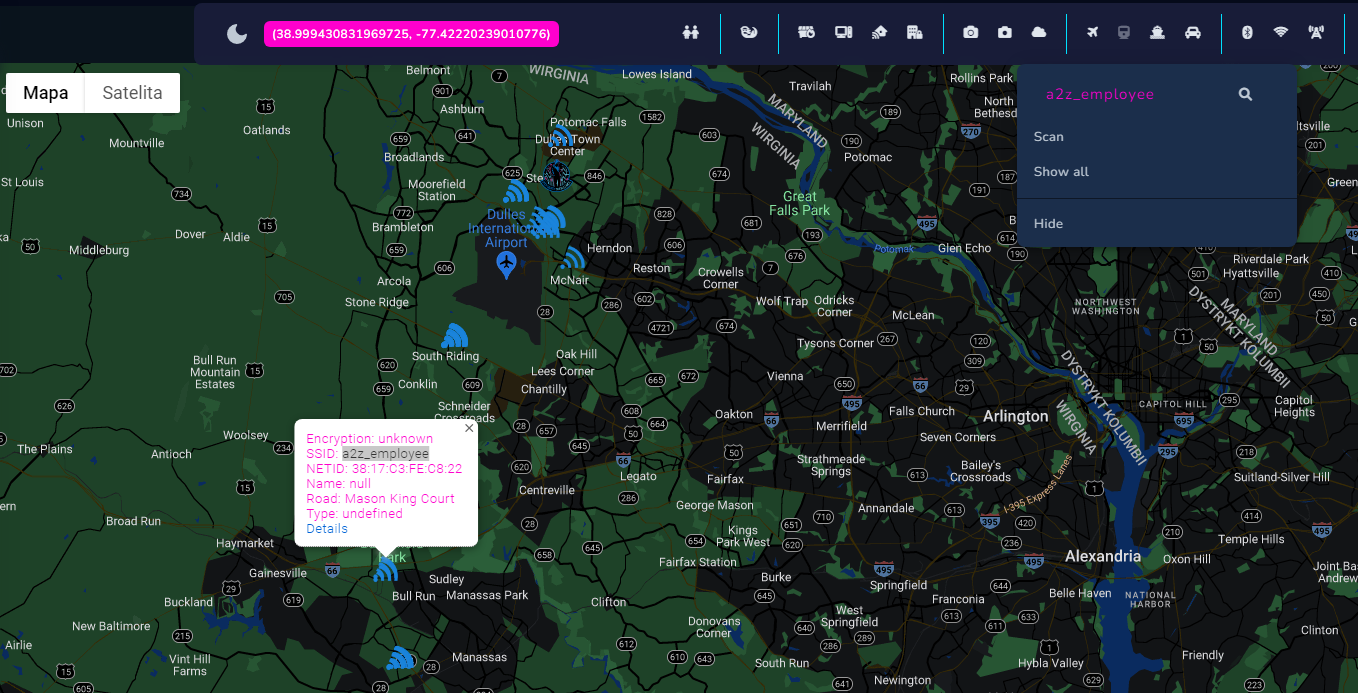
To remind you, when you click magnifying glass, it searches by SSID with given input. Scan button makes app scan for the network on map bounds, and Show All displays all already found networks.
In this case, around 150 networks have been discovered, some of them point to the same location, however there are couple on unspecified buildings that looks very similar to known Amazon data centers and even one on hotel nearby these buildings.
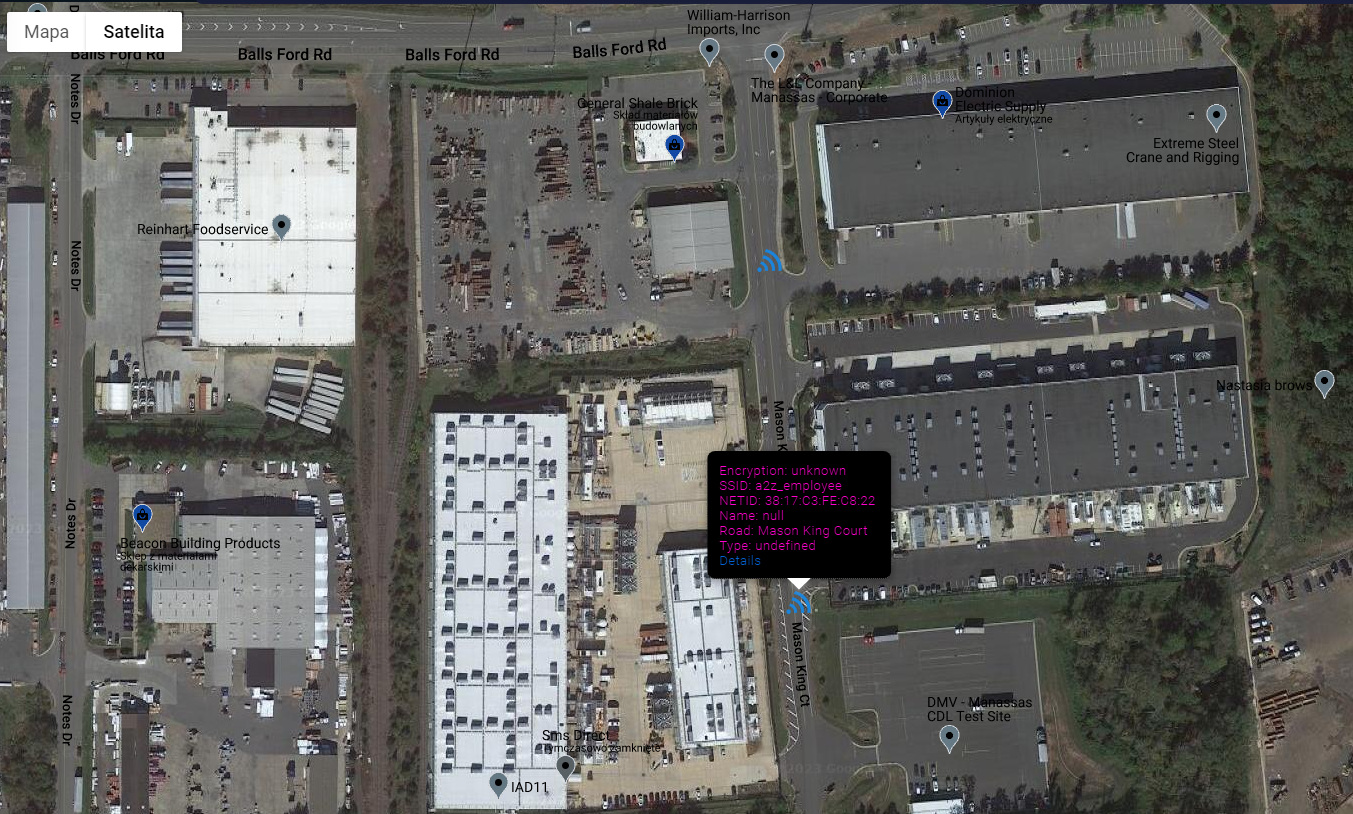
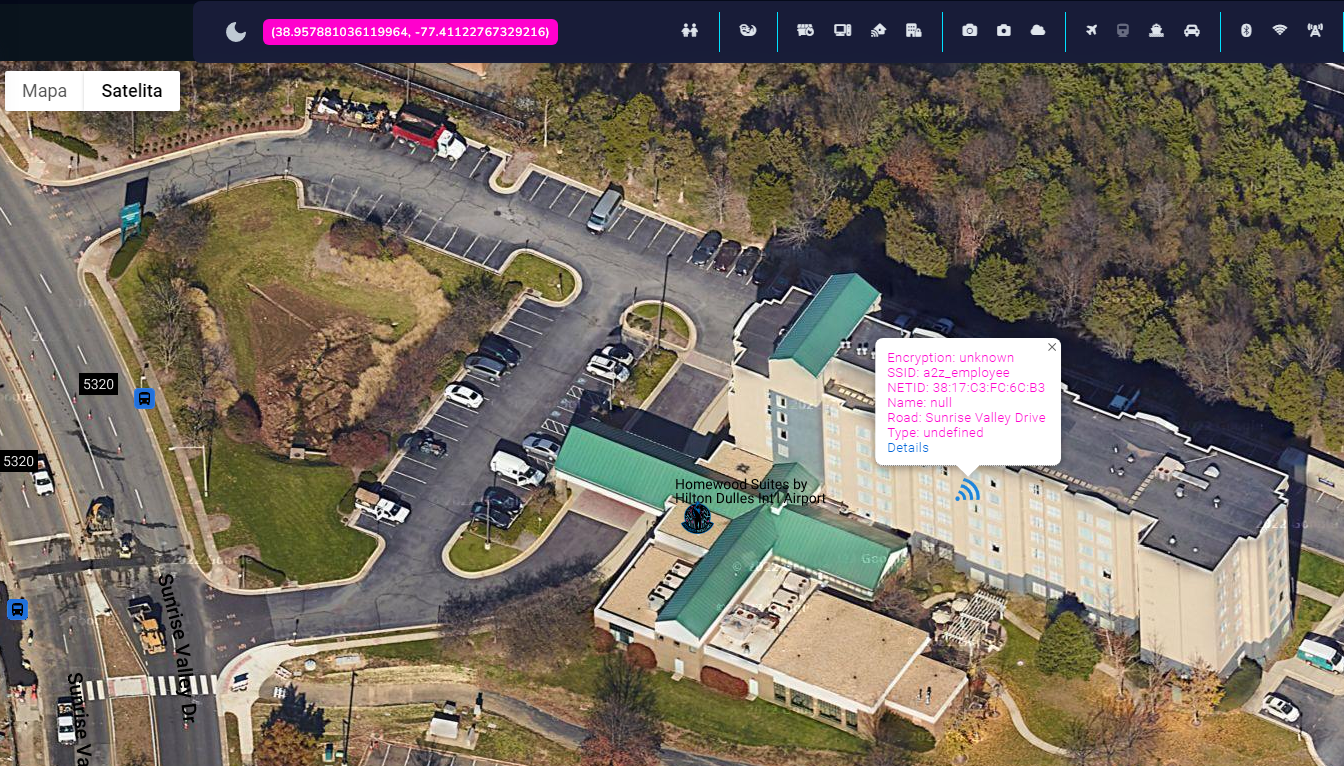
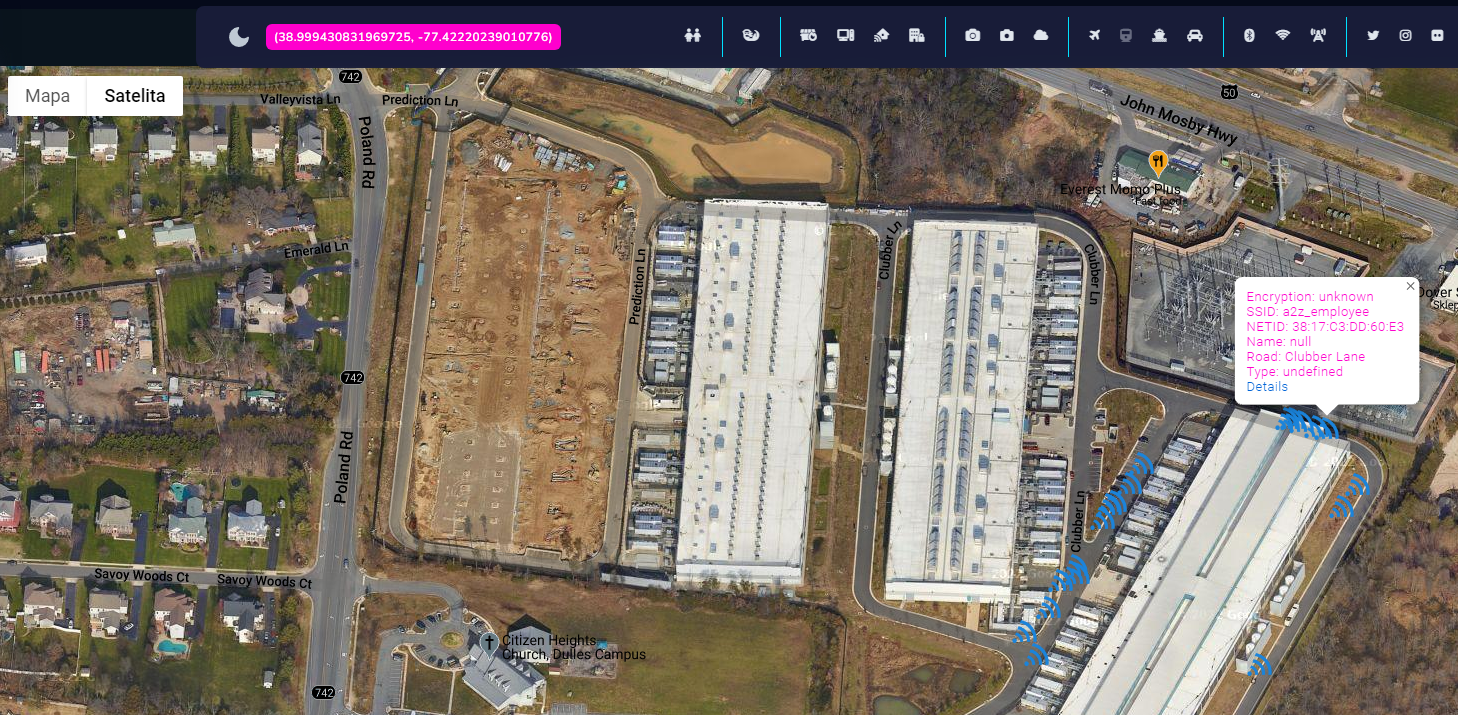
This technique allows to track people and organizations based on WiFi correlation and it is a next step in geolocation based investigations.
Rules
I composed couple must-know rules when using Open Source Surveillance, it might apply to different OSINT investigations as well
- Use multiple sources
- Ex. Check IP against BinaryEdge to confirm Shodan finding or scan it actively
2. Geolocation is not always accurate
3. Scan multiple times
- To get every finding, scan your location and nearby territory
4. Get as much intel
- Collect intelligence from every available source
5. Save everything
6. Do not rely only on one tool
- Add manual research or other tools to your investigation
7. Be creative
- Actively scan all ports on the host
- Correlate WIFI SSID to find company headquarters
- Check person Strava activity and find cameras on his favourite track
Technical stack
Whole application has been written in Python/Django, HTML, CSS and JavaScript. Celery is used as a task queue and Redis as a broker. Everything is hosted on Heroku on Premium 0 (Redis) and Basic (Postgres) plans with domain purchased on Namecheap and authorization done with Auth0 with free plan. For some features, proxy is needed as well as keys and account management to make it work without any user input. Monthly costs are estimated around $50, so if you want project running you can subscribe and donate via Paypal, Stripe or Crypto.
Mobile version
Application works on mobile same as on desktop and has the same features. Next update will introduce live geolocation on mobile devices, to track current position and cross reference it with other findings like cameras, devices or photos. At the end of the day, it's about hacking and researching 'on the ground' so I will present how to use mobile version during reconnaissance.
Summary
I can imagine a lot of cases where Open Source Surveillance can help - military activities, law enforcement investigations, espionage, photos geolocation, events & people tracking, securing exposed Internet of Things or protect Industrial Control Systems in critical infrastructure.
I spent some time designing, building and coding the tool but at the end it gives a lot of joy when using it and especially knowing it might help in real world cases.
Next steps
Testing, testing, testing and in the meantime development of infrastructure, writing articles how to get best out of the tool and cooperating with anyone who wants to contribute, also lot of new features and data sources are on the roadmap.



