Today I want to present additional big feature to my long time project - Kamerka. From now on you can access statistics about Internet exposed Industrial Control System and Internet of Things devices via comfortable GUI
Kamerka Lite

Website related to the project

Introduction
First version of the tool has been created in 2018 and allowed only to map exposed cameras. The functionality was very limited and it was more like a script rather than intelligence gathering tool, which I can say about it now.
It's fully functional intelligence gathering tool for exposed Internet of Things and Industrial Control Systems devices with many features, which some of them were added couple weeks ago, and if more ideas will come to my mind I absolutely improve the tool.
From latest updates, the most important one was to completely change the design and give it more 'Offensive OSINT' branding and generally refresh the look.
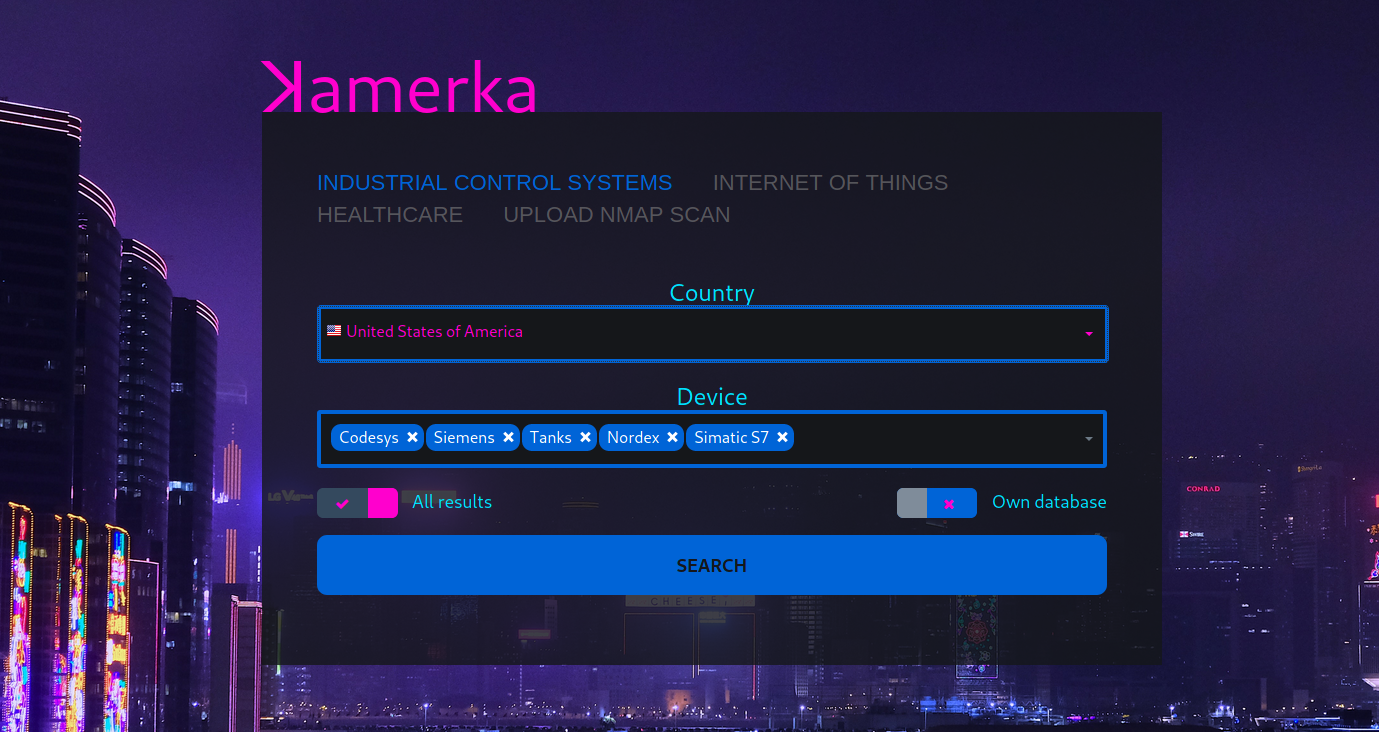
Like with every update, many devices have been also added. From standard IoT like sprinklers or doors, to Human-Machine Interfaces, wind turbines or satellite receivers. Right now it supports more than 100 different devices.
In addition, thanks to Christiaan Beek, who suggested to add attackers infrastructure, i.e. command and control servers like Metasploit or Cobalt Strike, to the tool. So, basically you can have a lot of fun looking for Internet facing devices and infrastructure and trying to figure out whom it belongs to.
I wrote many articles how to pinpoint such exposed devices to specific facility and gather geo data or additional details that might be useful for phishing campaigns, but with this update we focus more on statistics.
Kamerka.io
Since GUI version I had some questions about how to install it, how it works and who actually can benefit from the tool. This questions and more have been addressed on the official website of the project -


Among description of the most important features you can read security best practices, to secure ICS devices, straight from Cybersecurity & Infrastructure Security Agency.

I hope you will get all the answers you need about the project on kamerka.io. If not you can contact me directly or via email.
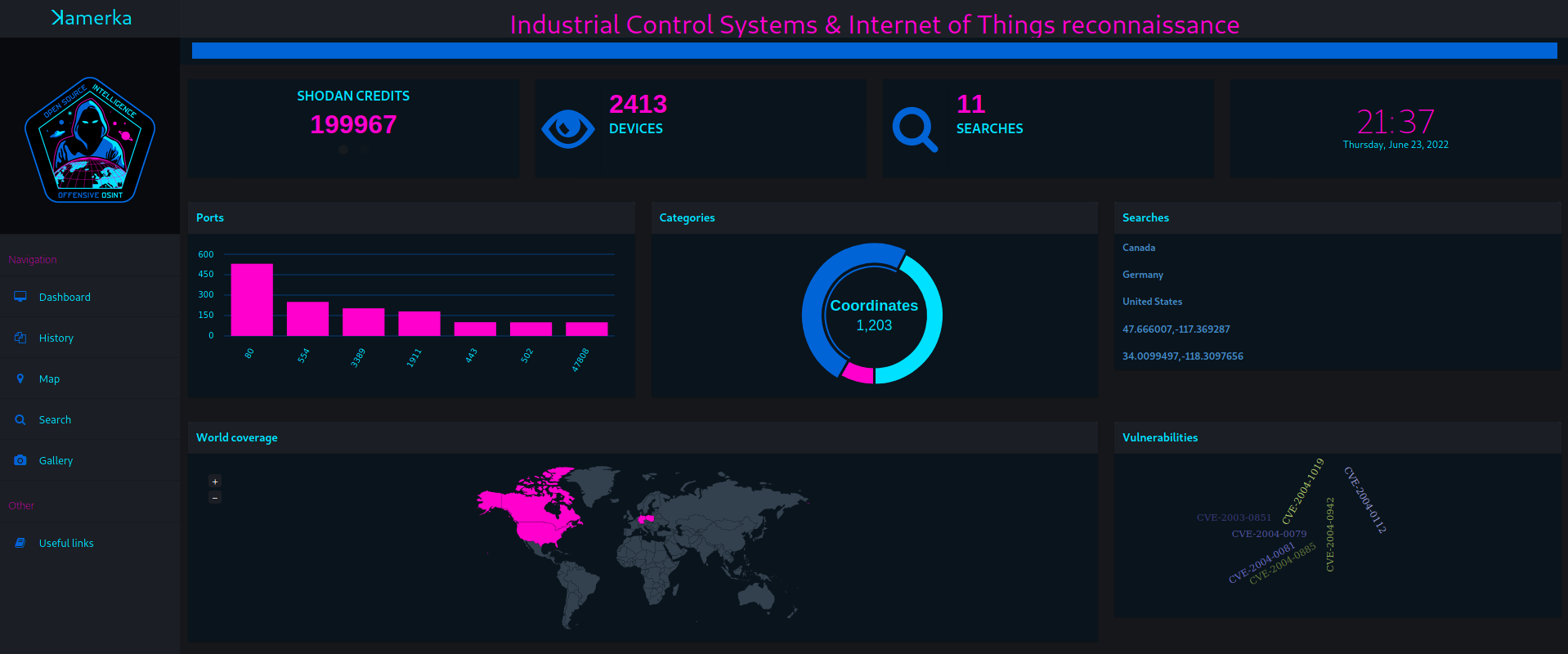
All of this sounds very fun but the biggest feature that has been implemented is completely new website with interesting statistics collected every day.
Kamerka Lite
Kamerka Lite version has very limited functionalities but plays also important role for everyone who is interested in tracking and geolocating such devices or is just curious how exposure looks like for specific countries.
Application is statistics based for most important Shodan ICS queries for particular countries.
It can be accessed at

On main site you can lookup total number of devices, most affected organization, city or device.
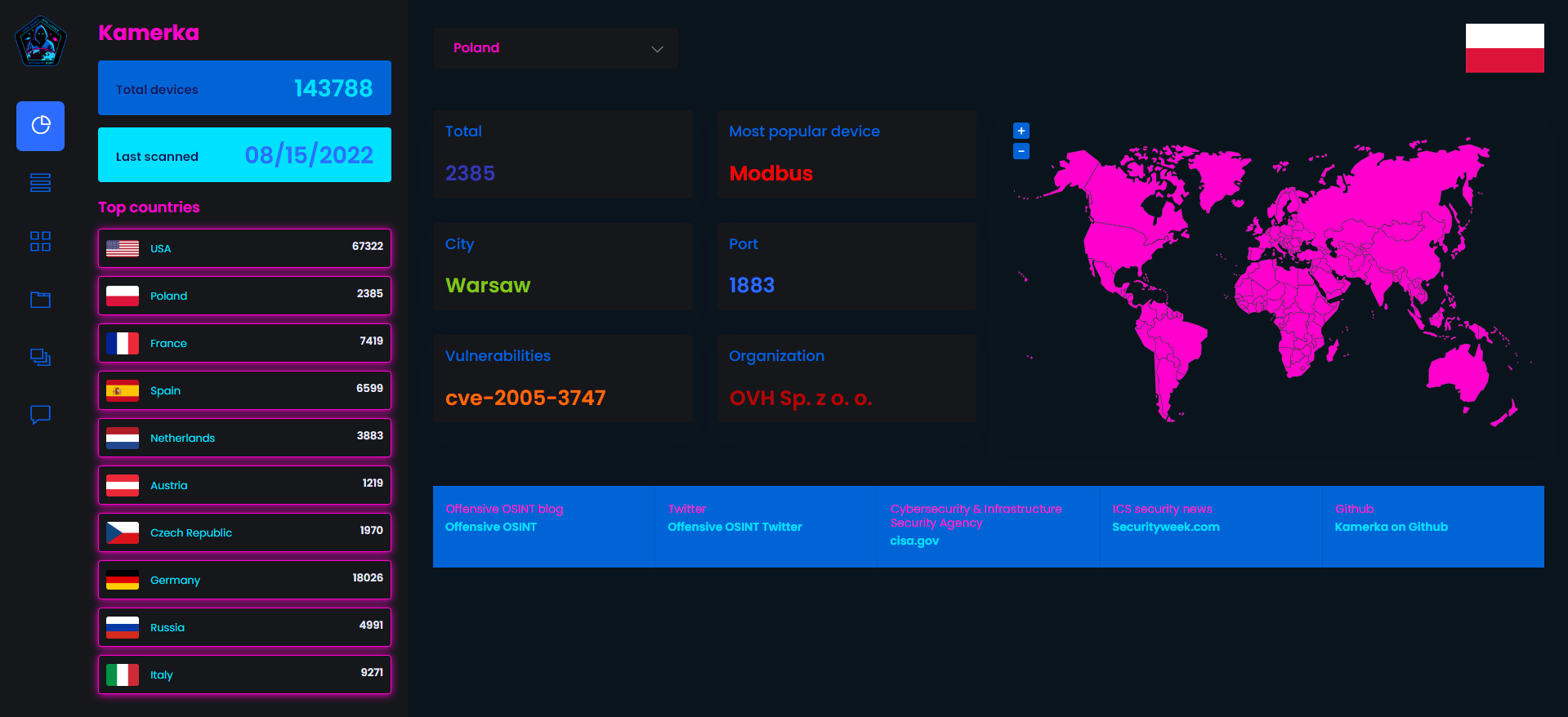
If you click on the map you, popup will appear giving you also some information, there are no charts yet but will be after couple weeks of monitoring exposure.
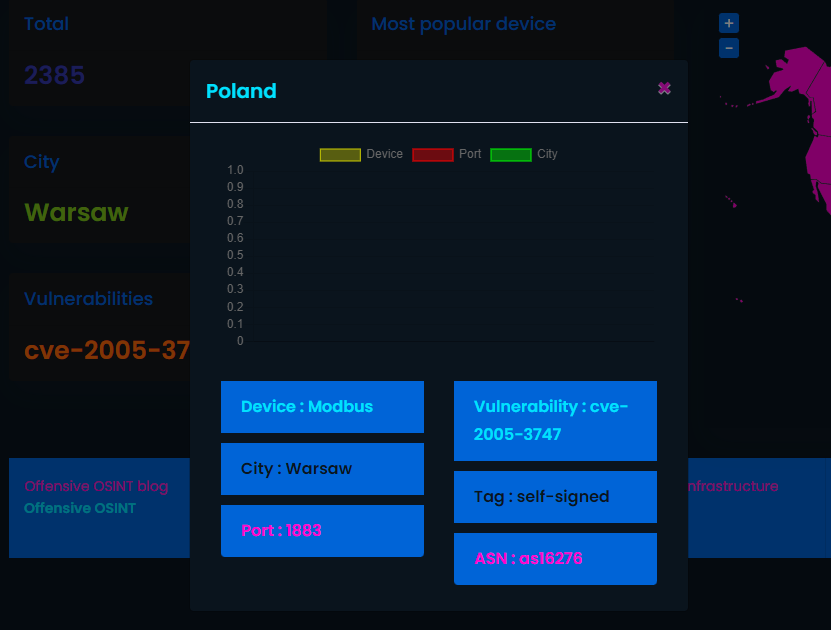
Except some broad statistics, Kamerka Lite also shows you what devices have been searched for and their amount. This way you can look for devices in Shodan knowing how many hits you will get.
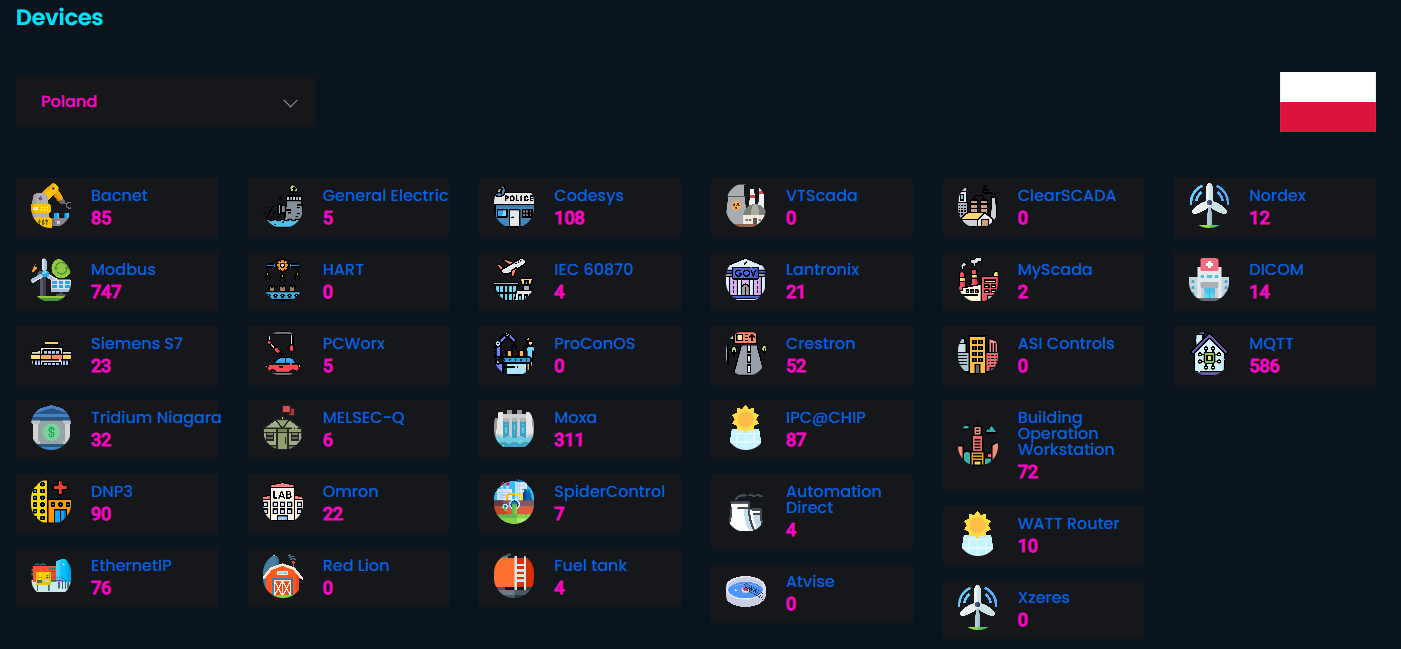
Kamerka Lite was created to show size of exposure that is often talked about by researchers and CERTs. In addition, it's worth to keep an eye on advisories and vulnerabilities by vendor on official CISA site

Website is updated daily with new data for each country and after couple months more statistics will be presented about how exposure changed over time for specific devices or countries.
For the record, to create statistics Shodan facets were used with following parameters
- City
- Port
- Tag
- Vulnerability
- Organization
- ASN
and below queries
{
'Bacnet': '"Instance ID:" "Object Name:"',
'Modbus': "Unit ID: 0",
'Siemens S7': 'Original Siemens Equipment Basic Firmware:',
"Tridium Niagara":"port:1911,4911 product:Niagara",
'DNP3': "port:20000 source address",
"EthernetIP": '"Product name:" "Vendor ID:"',
"General Electric":'port:18245,18246 product:"general electric"',
"HART":"port:5094 hart-ip",
"PCWorx":"port:1962 PLC",
"MELSEC-Q":"port:5006,5007 product:mitsubishi",
"Omron":"port:9600 response code",
"Red Lion":'port:789 product:"Red Lion Controls"',
"Codesys":"port:2455 operating system",
"IEC 60870": "port:2404 asdu address",
"ProConOS":"port:20547 PLC",
"Moxa": "Moxa",
"SpiderControl": "powered by SpiderControl TM",
"Fuel tank": "port:10001 tank",
"VTScada": "Server: VTScada",
"Lantronix":"lantronix",
"Crestron":"crestron model",
"IPC@CHIP":"IPC@CHIP",
"Automation Direct":"Server: EA-HTTP/1.0",
"Atvise":"Server: atvise",
"ClearSCADA":"ClearSCADA",
"MyScada":"title:myscada",
"ASI Controls": "title:'ASI Controls'",
"Building Operation Workstation":"title:'building operation'",
"WATT Router": "SOLAR controls product server",
"Xzeres": 'title:"XZERES Wind"',
"Nordex":"html:nordex",
"DICOM":"DICOM",
'MQTT': 'product:MQTT'
}Summary
First version of Kamerka was released couple years ago and since then I was tracking, to a greater or lesser extent, different kind of devices that were wrongly configured and connected directly to the Internet. There are literally everything what you can think of, from most popular ones like cameras, security systems, intercoms, smart homes to more critical ones like wind turbines, HMIs or building operation workstations.
New vulnerabilities are being released every week, it also applies to the ICS and variety of web applications that supports operating of industrial devices. When they are allow remote access, attackers can also take advantage of that, so that's why it's important to limit the exposure of such devices.
Follow me on Twitter




