From now on ꓘamerka has a mobile version. You can geolocate specific buildings or facilities in web interface and all the results will be available on your phone. It allows you to go to particular place and examine it’s physical security. Cameras, building operation systems, parking spots, UPS units, bunch of scada devices could be located and exploited supporting physical intrusion. Everything is displayed in clear way in ꓘamerka mobile application.
Disclaimer
During the research no system has been breached, hacked or compromised.
Unfortunately, code for mobile application probably never will be shared.
Introduction
There are still hundreds of thousands Internet exposed devices that are operating in various types of buildings and infrastructures. They are responsible for keeping everything in order in the facility, from doors, cameras, temperature to lights and power - exposing it without proper security measures might be easy target for hackers.
It also applies to critical infrastructure that is mainly in the circle of interest to nation state actors or terrorists. Exposing it means giving opportunity to hack into these systems and make damage to workers and society.
ꓘamerka mobile has been created to share awareness about possible attack vectors on any building that exposes it’s vulnerable devices or control panels directly to the Internet without authentication or with week credentials. It’s also shows how physical security and Internet connected devices should be secured in order to keep whole facility safe. If you can control building remotely, it’s so much easier to break in, you can turn off cameras, sensors, lights or open doors remotely. Moreover, it’s possible to track water or electricity consumption to know when place is the most attended and carry the attack out when no one will be present.

The most important factor in this game is to locate actual device/facility behind exposed interface. ꓘamerka web interface can extract indicators that precisely points to the place that device is running. Technicians and service workers usually leave the names to manage easier their infrastructure and connect to the correct device. It may be abused by hackers to pinpoint it’s to specific location, what I will show in this article.
ꓘamerka project and it’s mobile version reminds me of a game Watchdog when you could hack device that is in front of you like turning off cameras to pass unnoticeable or remotely open locked doors.
These types of hacks were also one of the main topic in TV show Leverage, when hacker Hardison gained access to the whole building to help his teammates enter and move safely inside the facility.
I decided to use this same approach — ideally, team should consist of two people, hacker behind ꓘamerka web interface locating and hacking devices and person trying to get into the building. I call it Operator and Field Agent.
Public announcement
ꓘamerka will be presented on X33fcon conference in Gdynia, Poland in May. I will be talking about OSINT, targeting IoT, ICS, critical infrastructure, ꓘamerka mobile version and more.

Operator & Field Agent
Couple steps are needed for mission to be successful, first one belongs to Operator, he needs to scan devices in ꓘamerka Web. It’s worth to mention that scan takes place in OSINT way via Shodan, so it means that no packet is transmitted to the target, information are gathered from open sources and no one is alerted about any potential active scan attempt. Operator can choose to scan whole country or only on specific territory based on coordinates. He has a choice among more than 100 different devices that are now implemented. New devices have came out with this update as well, more about it a bit later.
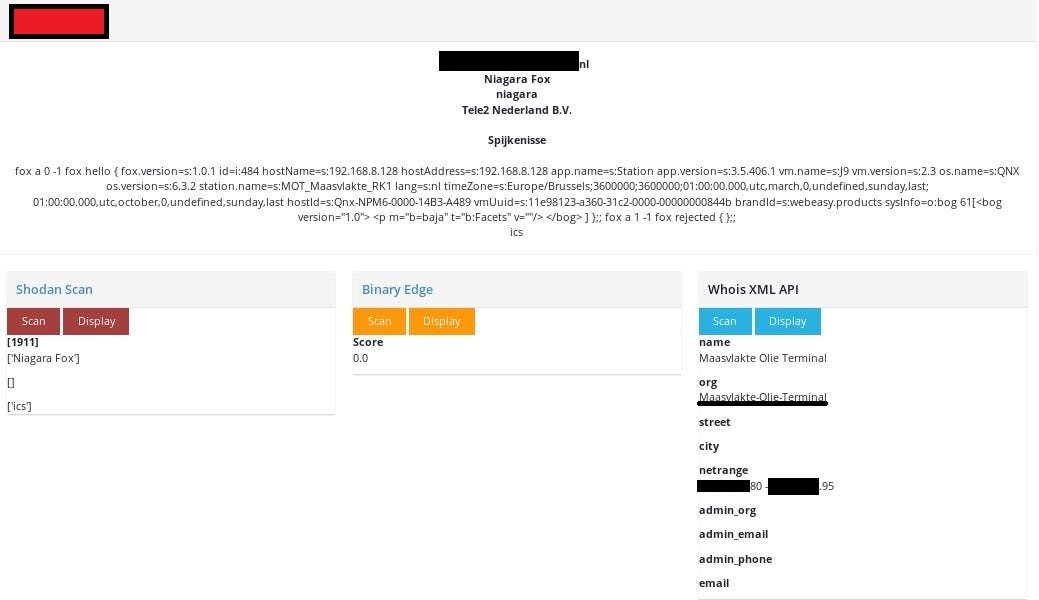
After that, he has to locate them, IP geolocation is not a best source, but other methods can be more precise. It depends of Operator’s creativity, he can check for Whois information, certificates or other ports running on these host that may reveal useful info. In some cases there are RDP running which shows usernames with name and surname, so it’s possible to search for this person in social media and check where he works. He can also scan (actively or passively) neighborhood IPs what also is helpful for recon, but the most important factor is in device itself. Niagara Fox reveals facility name in response and being precise in station_name field that I will mainly focus on. Of course place indicator can be found for different devices from various vendors, in many places. You could see examples of the geolocating in my tweets.
It’s also important to scan device in Web interface to gather all details about hosts — other ports and vulnerabilities.
Third step consists of updating location in web interface and send it to Field Agent together with additional notes from Operator like street number or special safety measures during reconnaissance.
Example and technical details
Let’s look on one example, how to send device with location to the mobile app.
Operator has found an exposed device in critical infrastructure, based on the indicator MOT_Maasvlakte_RK1. Further search reveals that it’s Oil Terminal in Maasvlakte and Whois information confirms this assumption, showing that IP belongs to the same organization.
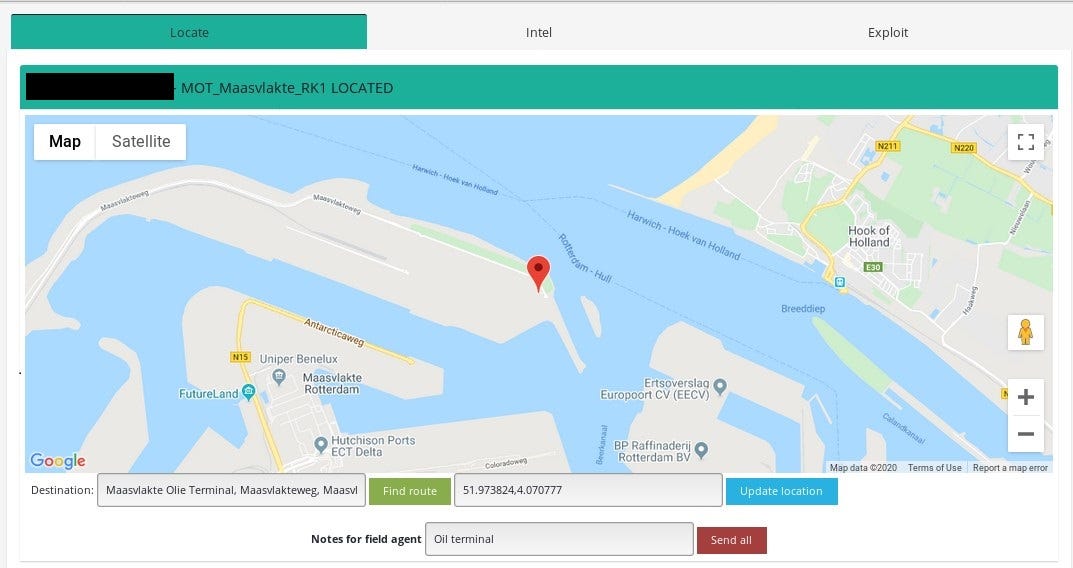
As already mentioned, Operator updates location, add notes and send everything to Field Agent by clicking “Send all”.
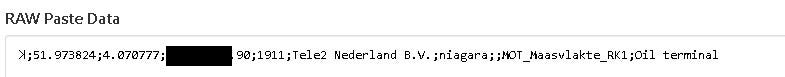
Since ꓘamerka is not hosted anywhere and everyone can setup his instance, information is saved in private pastes on Pastebin. Android application scans your pastes and if it title starts with ꓘamerka_IPADDRESS it retrieves the content.

Content includes all information from Web interface, updated location and notes from the Operator in CSV format.
After that, Field Agent gets notification or scan for devices again in his mobile app getting all the details that have been sent by Operator.

After clicking on the marker, details will be presented.

Example above is in remote place couple kilometers from nearest city. Mobile version has been created for big cities in mind.
Real journey over exposed devices
Since I am one man army, I located and then went on a trip in South Holland province to check for buildings with exposed devices and their physical security, I cannot reveal it here in this article but it will be part of the presentation on X33fcon conference.

But to show you capabilities of the application, I located couple places in different US cities.
It’s obvious that it tracks your location like in Google Maps and markers point to the buildings with exposed device. With this method you can get notification or your phone can vibrate when you are nearby one of the devices.
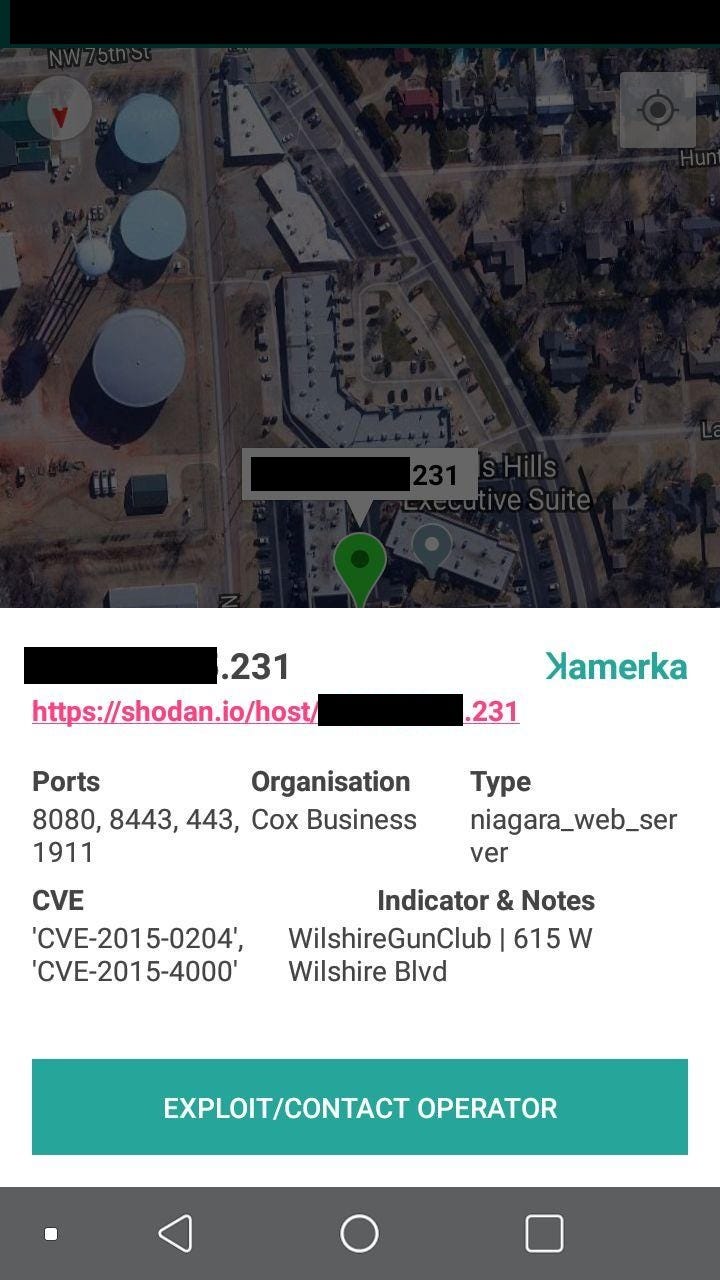
#1 Gun Club Wilshire in Oklahoma City
#2 Emerald Queen Casino in Tacoma with many vulnerabilities

#3 PNC Bank in Center of Rocky Mountain with additional ports open (RDP inluded)

#4 Fire department in Scotia, NY

#5 Town Hall in Somerset, MA
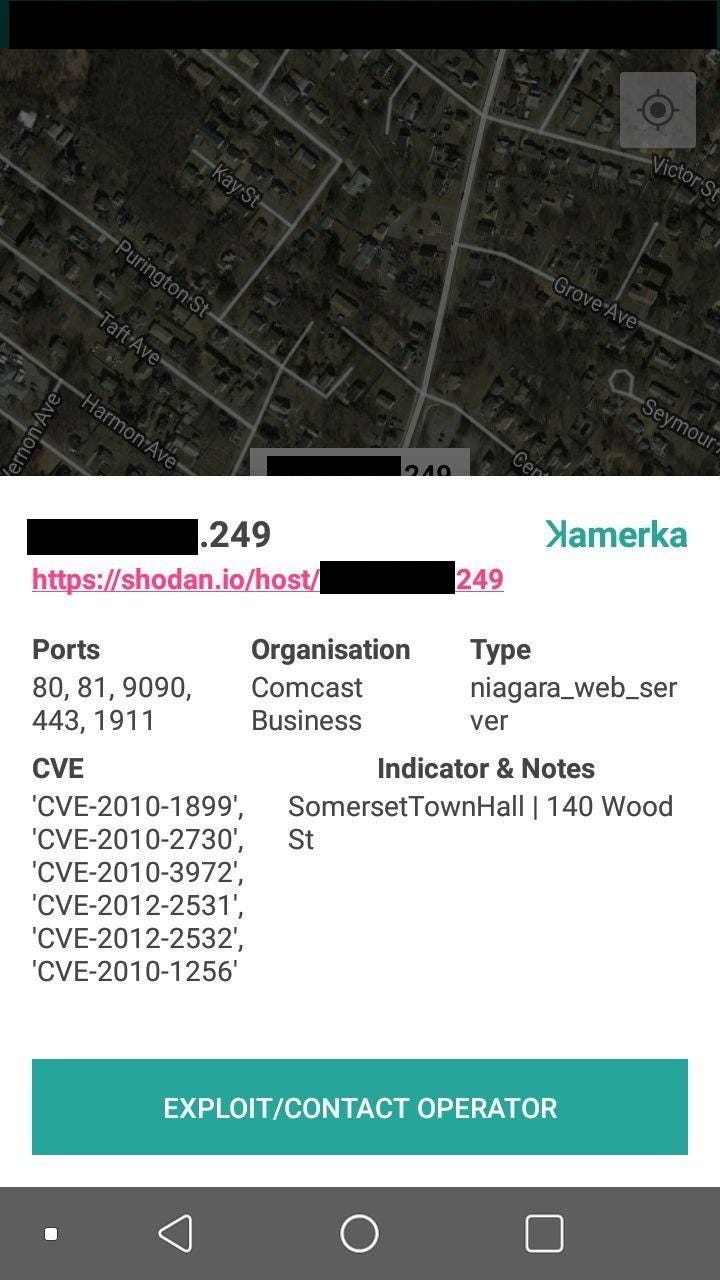
It’s possible to do this same with exposed cameras although you need to have strong geolocation skills to pinpoint it based on the live stream.
You can find different exposed devices in almost any city and in big ones you can targets hundreds of them and put in on map, which is really cool to know weaknesses of the city infrastructure.
However, not only Niagara Fox can be precisely pinpointed to particular place. I gave examples earlier and devices list is getting bigger and bigger. With new update you can also search for UPS units, Buildings Operations System and many more.
At the end it’s worth to mention article below with quote that suits to my post:
“This default port discloses system information without authenticating, allowing cyber attackers to identify devices and systems that are not patched against known exploits,” the FBI alert says. “Successful exploitation could lead to data leakage and possible privilege escalation.”
FBI warns industry that hackers could probe vulnerable connections in building systems
New devices, new indicators
With every new update new types of devices are added. This time I deliver queries for UPS power devices, Siemens Sm@rtClient VNC, ClearScada, Intellislot, temperature monitors, Intuitive Controllers, MyScada, Building Operation WebStation and lot more.
You can check full list of devices on my github.
#1 University in Poland

Little bit of creativity and luck and you can find exact place of the device. Whois information pointed to one of the University in Poland and location from device showed department (redacted) and room 601, in this case.
#2 ConnectUPS
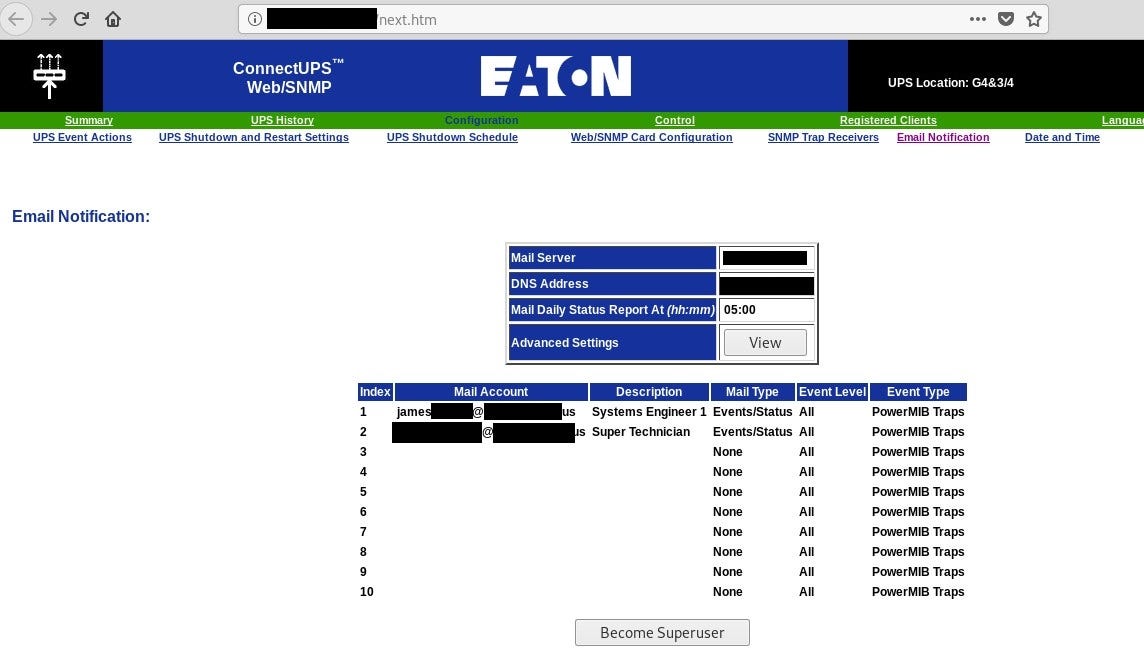
It reveals couple details about location in right top corner but there are also email accounts for Super Technician and Systems Engineer. Also Mail Server might be useful to connect device with organization and the building at the end.
#3 Parking spots
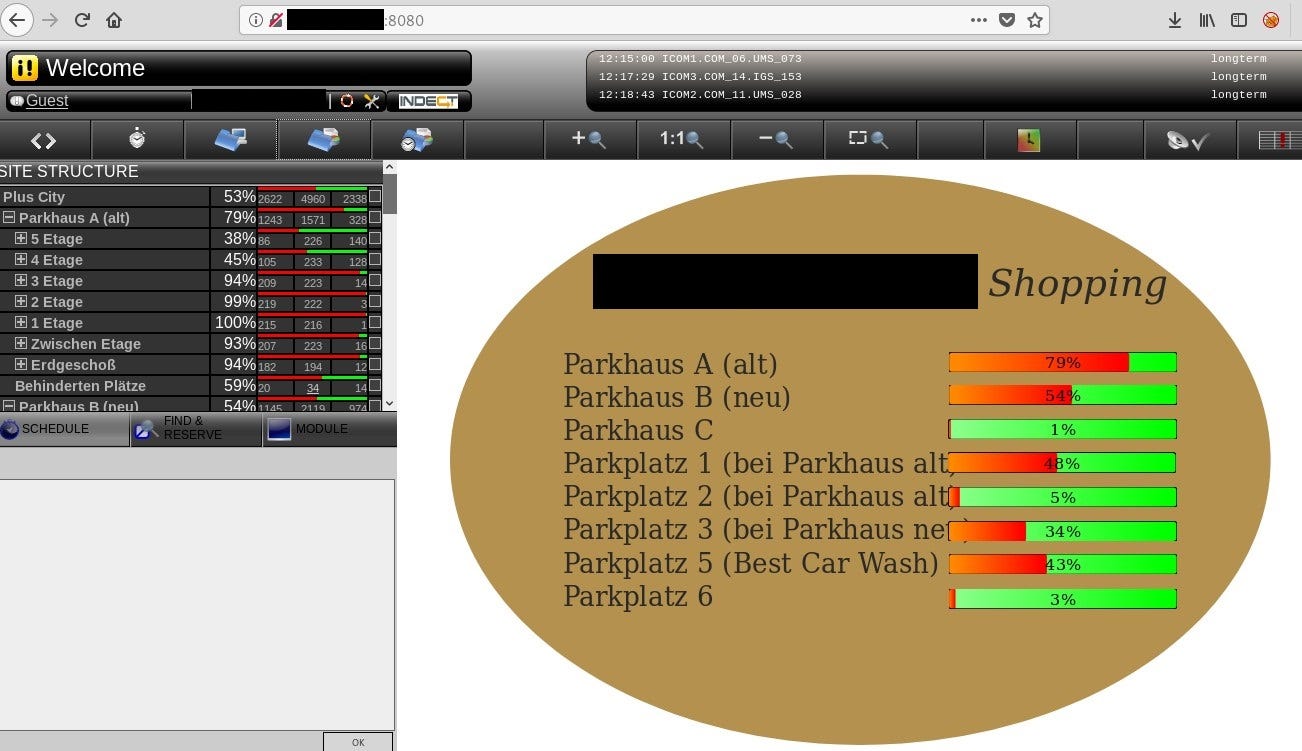
Query title:indect allows to search for Parking Guidance Systems by Indect. Even with guest privileges you can gain useful information.
#4 MyScada

According official website of MyScada
mySCADA Technologies is a technical leader in the visualisation and SCADA fields. We are constantly improving our system solutions with an emphasis on customer needs, ease of use and a high level of reliability. We believe in sustainable partnership that brings together excellent cooperation and minimizes expences. mySCADA is also an integral part of Industry 4.0 and IoT. Form the new age of Industrial Automation with us.
#5 StruxureWare Building Operation WebStation

StruxureWare Building Operation WebStation is a web-based user interface for day-to-day operation in a SmartStruxure solution. WebStation comes built in with every Automation Server and Enterprise Server, and provides easy access to the software from anywhere in the world.
Another system that exposes it’s precise location. It’s also a part of critical infrastructure.
Conclusion
There is no central ctOS like in Watchdog game yet, which controls whole city and all connected devices but everything is going into centralization so in a couple years smart cities will be a real thing. The idea presented here might sound too futuristic but it shows that with some effort you can map lots of devices in one city or country and then use it for your profit. Mobile application is an additional feature to go to the building, examine physical security and getting live updates from Operator and then hack it with different method, including social engineering, to takeover the building.
Originally published on 20th of January, 2020
Please subscribe for early access, new awesome things and more.



