ꓘamerka is going after hospitals and health clinics. I’m publishing tons of queries related to healthcare industry and medical sciences including variety of devices, EMR (Electronic Medical Records) or PACS (Picture Archiving and Communication System). As always, I will also show how to geolocate certain devices and attribute different leaks. In addition, I prepared new ICS devices to track in ꓘamerka.
Tool and list with all queries is available on Github:
Disclaimer
During the research no system has been breached, hacked or compromised. Critical findings has been reported to proper organization.
Table of Contents
- Introduction
- Responsible disclosure and attribution of open radiology servers in Australia
- How to penetrate healthcare industry without medical knowledge
- Geolocation of devices and EMRs —ꓘamerka style
- Other Interesting findings
- Additional ICS update including open Human Machine Interface and RCE vulnerable Bosch Security DVR Systems.

Introduction
You all heard about hospitals across the world being infected with ransomware, these incidents occur every month or even weeks. The healthcare industry is more fragile than any other because it’s about people’s lives and most sensitive information about theirs medical conditions. Ransomware attacks are only oriented to make profits and hospitals should act quickly to save patient’s lives, even quick outage of medical records or equipment can cause lost of credibility, money and of course bad reputation for hospital, not mention about patients that lives are in danger.
Ransomware Attacks Leave U.S. Hospitals Turning Away Patients
There are not much information about possible attack vectors but I can assume that cyber criminals gain access through phishing or some vulnerabilities, my bet would be Bluekeep, which I see often in RDP open to the Internet. Usually a lot of devices run RDP such as DICOM viewers or PACS.

Beside monetary profits of encrypting data, these systems keep trove of confidential information about people, their personal details, x-ray scans, payments and medical records that can be used for espionage purposes or blackmail.

Responsible disclosure and attribution of open radiology servers in Australia
Sometimes to get the confidential data, threat actors does not even need to exploit any vulnerabilities. Due to misconfiguration or lack of basic security knowledge some private systems are exposed to the Internet with no authentication.
The example of this can be two radiology servers in Australia. From one hand Australia is afraid of Chinese espionage techniques like Cloudhopper but from other they leave two unprotected Cynetics (http://www.cynetics.com.au/) servers. It’s web based Medical Imaging Systems for Clinical reporting & practice management.
Australian Cyber Security Centre has been informed about the leak and servers have been closed. Hovewer, they were accessible for almost a month what allowed to download all of the data by state actors or cyber criminals.
In this case leak contained 4,5 TB of data including radiology photos of pregnancies with diagnosis (almost 2M images!), invoices or personal patient’s data.

It’s worth to mention that servers was so unprotected that gave total admin rights with possibly to hijack logs and even delete patient’s payments and clinical results.
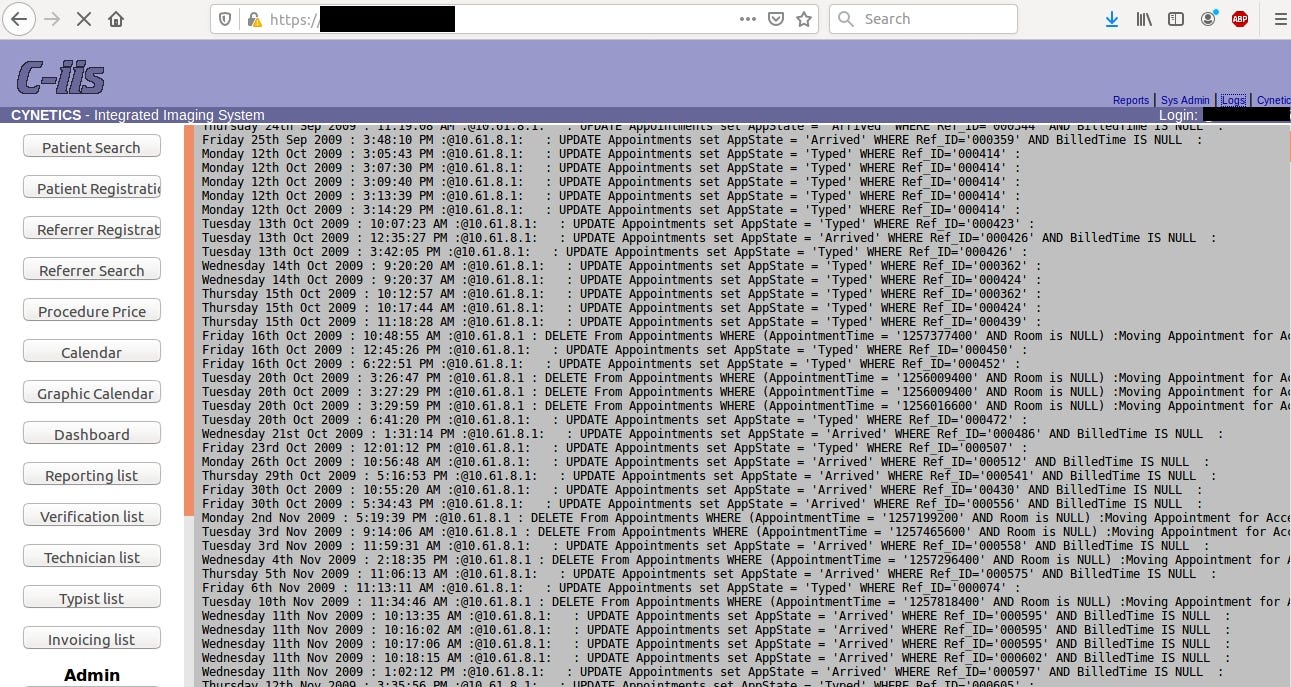
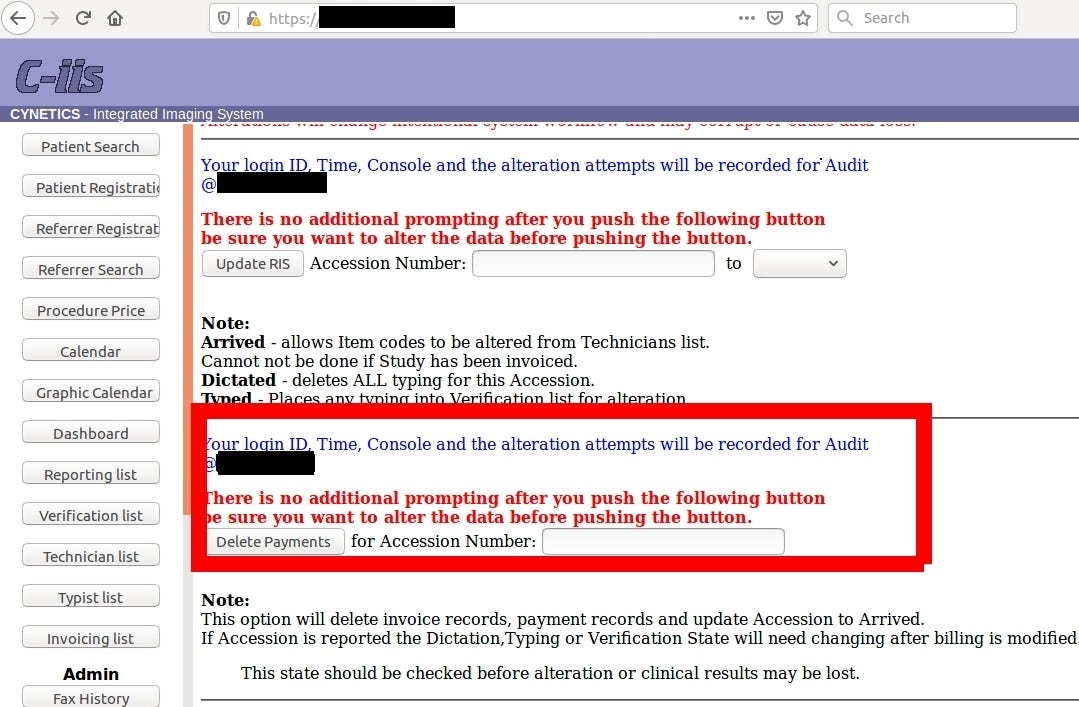
One could wreak total havoc in the server, tamper client’s data, delete payments of all patient’s or find vulnerability in Cynetics web management and penetrate the network deeper.

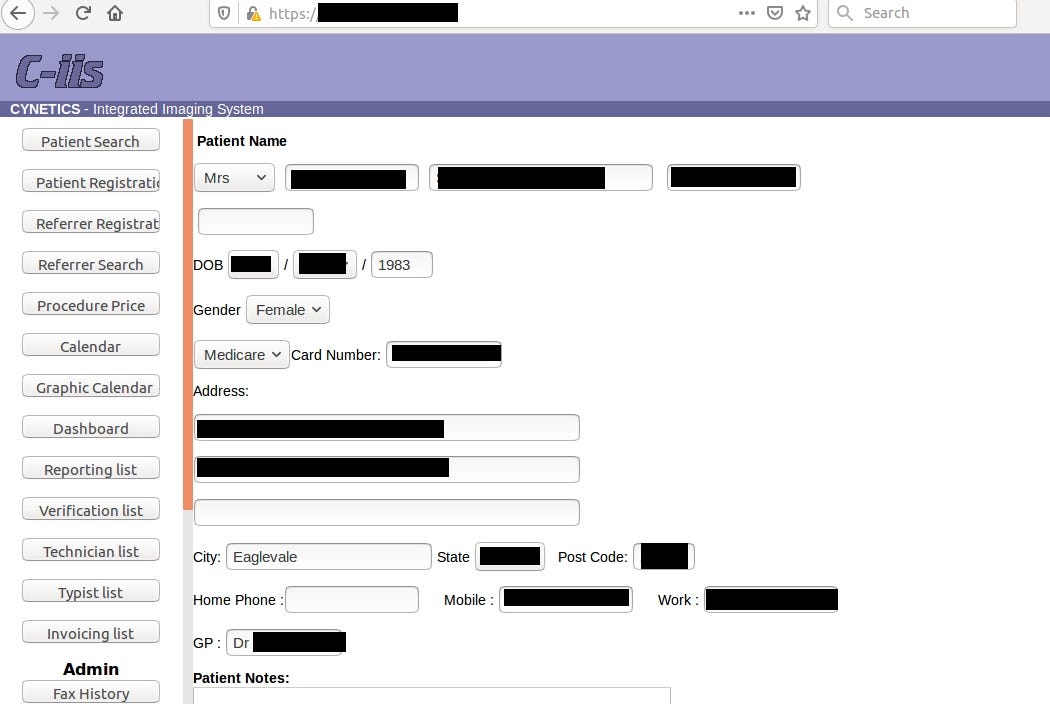
Payments and debtors details go back even to 2009 and photos to 2016. Probably there are some rules that require to keep medical data for specific period of time.

Going back to the main topic and the most important data in the leak, each patient has from 10 up to 40 radiology photos with description.

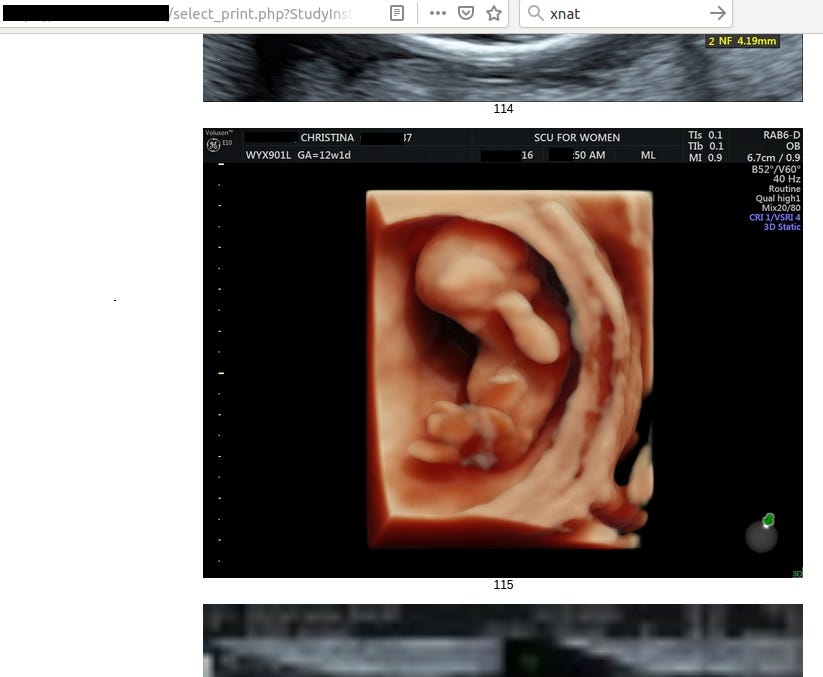

Frankly speaking, it says nothing for me but for someone acquainted with the topic it’s trove of information about health of patient and her fetus.
Attribution is sometimes very though even when you have total access to the server. I approach one of the Australian journalist to help me identify the owner and inform the potential victims. It was completely mistake and useless decision and conversation I have ever had. No contact with the victims have been established by her in order to try find responsible clinic and no information have been released due to „sensitive nature of the leak”.
Let’s then name the clinics that don’t have proper security measures in place.
First of the exposed server belongs to Tara Imaging for Women (http://www.taraimaging.com.au/)
To confirm the assumption, I downloaded one invoice:
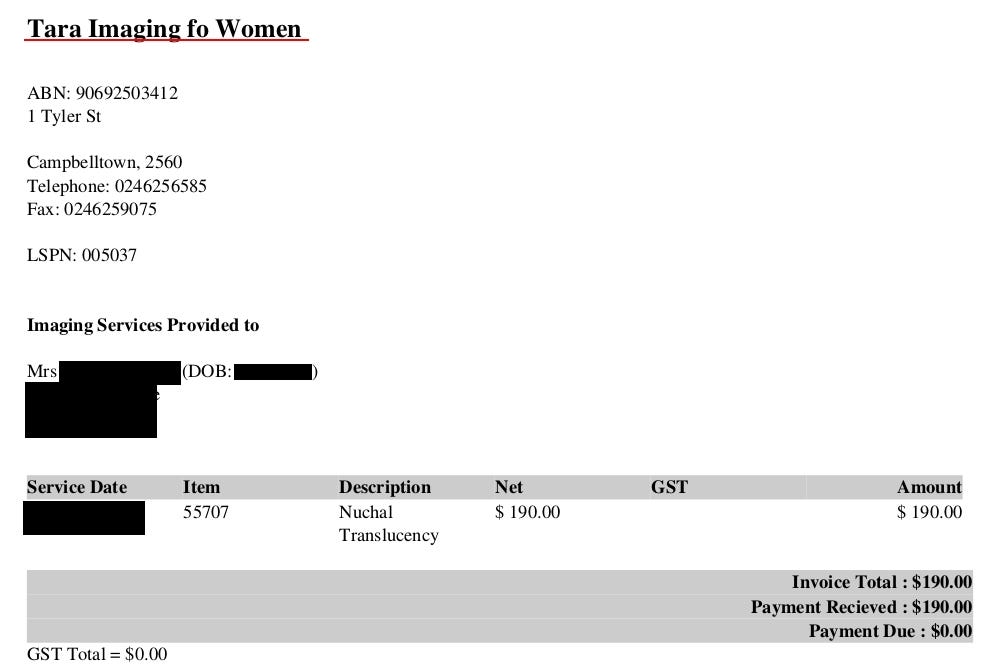
Second attribution was trickier and name of the facility was revealed in admin panel, it belongs to Western Imaging Group located on Campbell Street.

If someone is reading this article and used their service, she should be aware that her medical and personal data might have been compromised.
How to penetrate healthcare industry without medical knowledge
It was one of the most extensive research that I have ever done because of completely lack of medical and healthcare insider knowledge. I’m not a doctor and never done anything related to medical clinics or hospitals. I learned a lot about medical equipment, how hospitals are connected and managed and what services they provide.
To target devices I split research into three parts:
Depending on other people research and going blind with general terms like „Radiology, Oncology, PET, CT” etc
Researches that I came across were mostly useless, people gave only statistics and fancy presentations without sharing any Shodan queries that can be used to repeat their research. Don’t get me wrong, it’s interesting and meaningful content but everyone keeps it private therefore you can’t replicate the research on your own.
Only one paper I found help me to gather couple of devices, it was written by Christodoulos Tziampazis from University of Twente — „Exposure Assessment on Medical Devices in the Netherlands”. On his Github page, he shared keywords, vendors or identified responses from various medical devices.
Whole paper is piece of great job and you can read it here
From other talks or presentations I wasn’t able to retrieve anything what can help.
Next step was to target specific medical fields based on keywords like „Radiology”, „Oncology”, „Ophthalmology”,”Otorhinolaryngology”, „Neurology”, „Veterinary” and similar.
Also I tried this same technique with devices like „PET” (positron emission tomography), “CT” (computed tomography), „OCT” (Optical coherence tomography) and others.
This technique allowed me to collect more devices or login panels to them.
Machines with DICOM and healthcare organizations
DICOM stands for Digital Imaging and Communications in Medicine and is the most popular standard „to transmit, store, retrieve, print, process, and display medical imaging information”. DICOM was already implemented in ꓘamerka but if you want to learn consequences of exposing it to the Internet, you should read paper from Greenbone
I targeted devices running DICOM to check for other open ports and services on these machines. It turns out that it’s so unsecure that in most cases additional ports were open including 3389 (RDP), 80 (HTTP) 8080 (HTTP) and other products useful in further research.
Next phase was about searching through all hospitals, healthcare clinics, medical universities or laboratories based on Shodan queries „org:hospital”, „org:medical” and different variations of this including various language, for example in Dutch it’s „org:Ziekenhuis” or in German „org:Krankenhaus“. It allowed to do extensive reconnaissance in order to gather as much medical devices as possible. It was partially useful because I learned that also a lot of equipment are hosted in the cloud or in private network ranges outside of healthcare organization.
Targeting vendors
The last part was example of thinking completely out of box and it consisted of gathering all possible models, vendors or manufacturers of medical devices and cross-referenced it against Shodan database. The most useful query in this method was „http.html“ and „http.title“ of course I also run free text search.
The website https://www.medicalexpo.com/ helped me a lot, I scraped every vendor and every model from each category and passed in to Shodan. Knowing that some login panels of devices has footer like „Powered by … „ I was able to catch a lot of devices and check what additional services are listening on the machine.
By accident I also found other Industrial Contol Systems devices but I will describe in last part of the article.
At the end, when I found all of the devices, I had to find a common point or indicator to specify query and fine more devices of this same type. I was done by looking for HTML titles, favicon hash, content of HTML website or just free text search.
So I’m delivering about 90 queries to search for variety of medical devices — from defibrillators, operating rooms, optical coherence tomography, digital pathological solutions to HeartStart Intrepid, Microscopes, Nursecall Message Service, BrainScope neurology platforms, asthma monitors, a lot of EMR and PACS and many many more. Full list of supported devices in ꓘamerka is published on GitHub. https://github.com/woj-ciech/Kamerka-GUI#full-list-of-supported-devices-with-corresponding-queries
Geolocation of devices and EMRs —ꓘamerka style
With every update, I show various techniques to geolocate devices — cameras, Remote Desktop Protocols or Industrial Control Systems. It’s not different this time, some devices are hosted in the cloud without any potential indicator to pinpoint it to specific location. In other cases you can narrow your search to concrete place.
You can find previous examples of geolocation in my tweets
ꓘamerka on board! With new update you can track real location of vessels that expose theirs Sailor 900 VSAT.
— Wojciech (@the_wojciech) November 15, 2019
Quick #OSINT #maritime THREAD#shodan #CyberSecurity #infosec
Tracking devices and strategic places via NMEA sentences#osint #hacking #maritime #ics #scada #cybersecurity #shodan #shodansafari
— Wojciech (@the_wojciech) November 24, 2019
[THREAD]
Geolocating camera devices #osint #cybersecurity #ics #scada #shodan #shodansafari #geolocation
— Wojciech (@the_wojciech) December 1, 2019
[THREAD]
ꓘamerka supports new devices and screenshots! You can collect screenshots from open devices in specific location. I will show how to pinpoint device to precise place.
ꓘamerka does not stop. This update provides 45 new devices! Now it’s most extensive @Shodan dork database ever.#OSINT #scada #ics #shodan #shodansafari #iot #cybersecurity
— Wojciech (@the_wojciech) December 11, 2019
[THREAD] about what you can find and how to geolocate these devices.
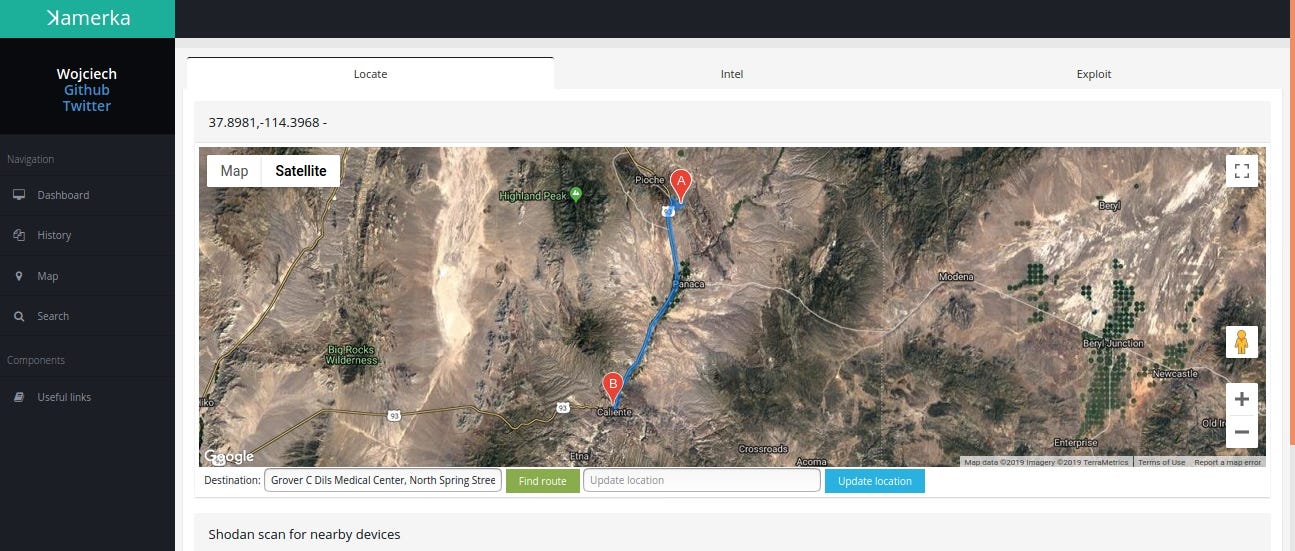
Case #1 Grover C. Dils Medical Center, Caliente, Nevada, United States
Medweb’s web based RIS/PACS offers improved scheduling and workflow solutions including online eligibility-confirmation tools to enable faster patient registration and revenue reimbursement.
Query: “html:’DBA Medweb. All rights reserved.’”
Facility name is exposed in HTML title and content

It’s worth to notice that SSL certificate is issued to Common Name: Development and Organization: Medweb

Geolocation is quite easy in this case, IP based location points to the nearest city but with ꓘamerka you can draw a route to the Medical Center

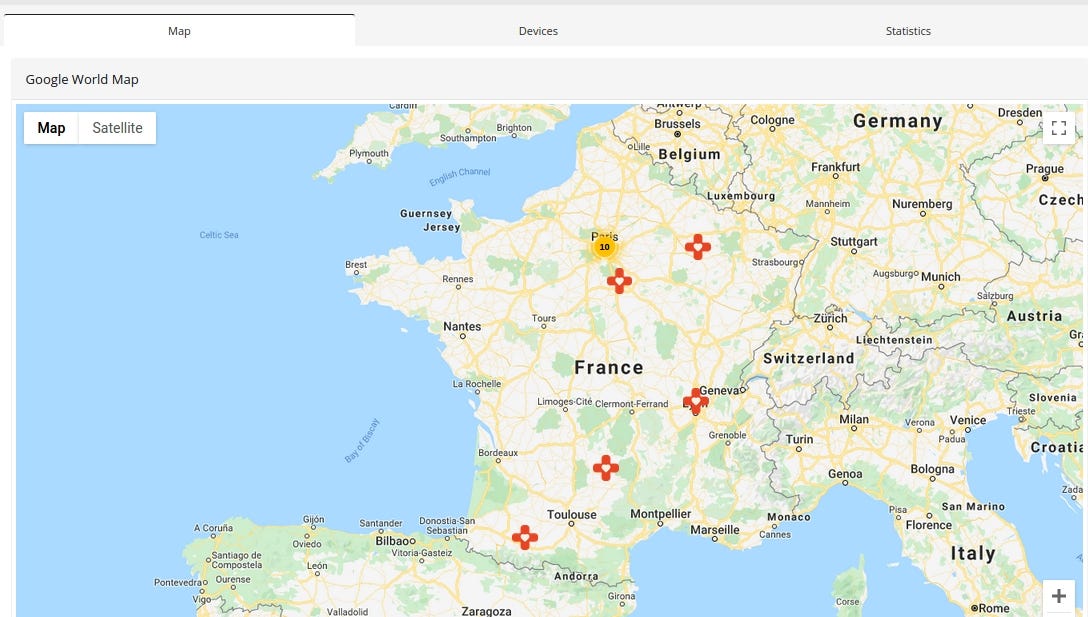
Case #2 IRM CHARENTON ST MAURICE, 22 rue Victor HUGO 94220, CHARENTON LE PONT
Medecon Clipper is web server designed to make images and reports available for the general practitioners or the specialists.
Query: http.favicon.hash:-897903496
Some devices/EMRs/software are used only in specific countries. Medecom (http://www.medecom.fr/) is a French based company and most of it are exposed in France.
Medcon Clipper reveals precise location in HTML content

IP location points to Montmorency but the actual clinic is located in suburbs of France
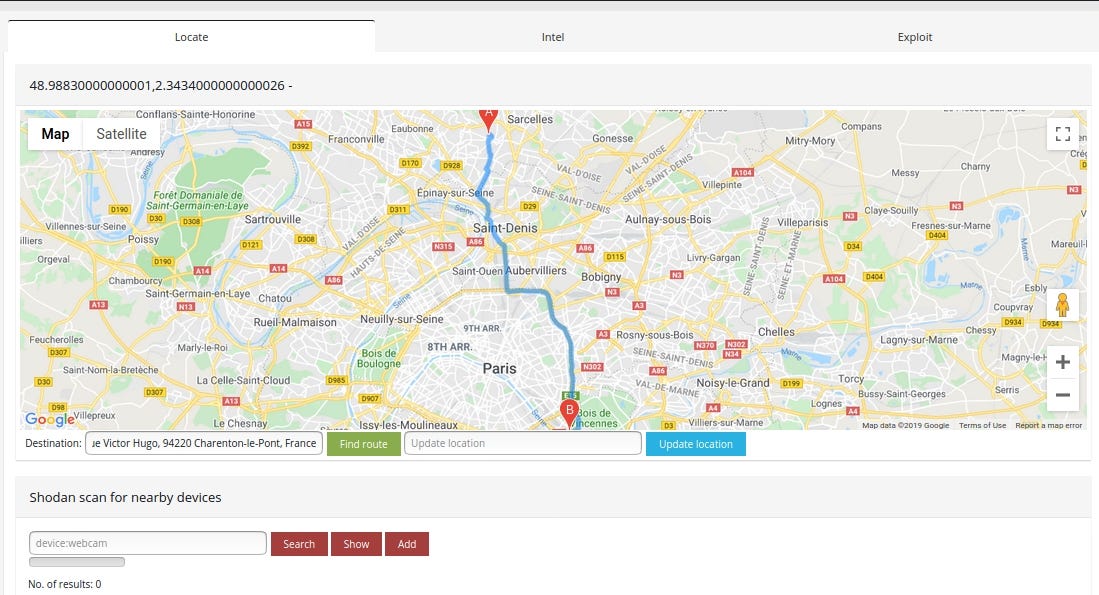
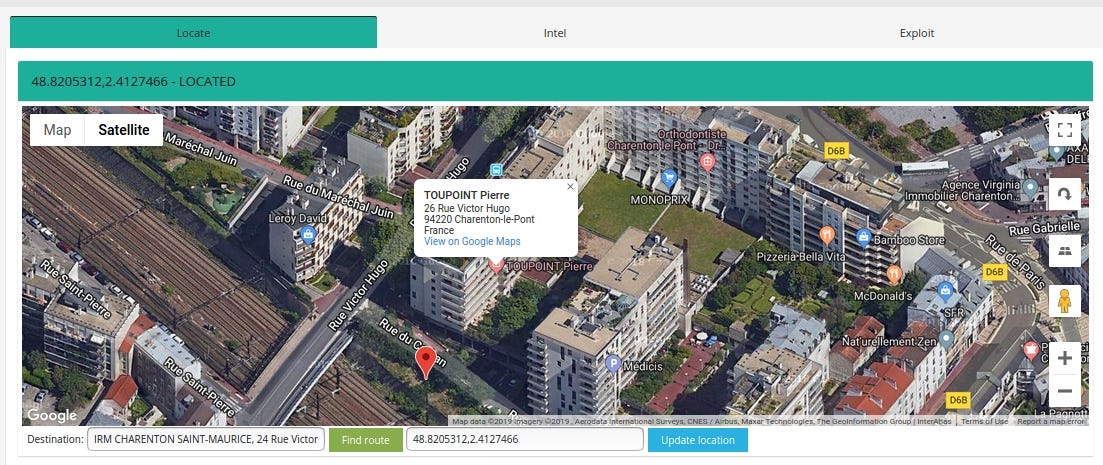
In addition, it shows the current version of software — 4.4. The newest one is 4.10, so it hasn’t been updated for a while.
Case #3 Maternity Sainte-Elisabeth — Chu Uclouvain Namur, Place Louise Godin 15, 5000 Namur, Belgium
Brainlab Transforms Healthcare with Software-Based Technology
To improve critical surgeries, radiosurgery treatments and operating room efficiency, Brainlab software and hardware devices create and enhance data.
Telemis
Telemis is a fast growing company active in the field of medical equipment, and specialized in PACS solutions.
Query: title:’Brainlab Origin Server’
Query for Telemis: http.favicon.hash:220883165
It’s example how other services running on the machine help to find a facility. Originally, I was looking for Brainlab hosts but on the same server Telemis web interface was running.
Brainlab revels domain — montgodinne.ad, which is a site Mont-Godinne

Telemis instance confirm this assumption, exposing name of facility CHU UCL Namur. It was running on the same machine but on different port.

Joining it together we have full name and location of hospital — CHU UCL Namur — Site Godinne
IP points to Waterloo but location of hospital is around 80km away.


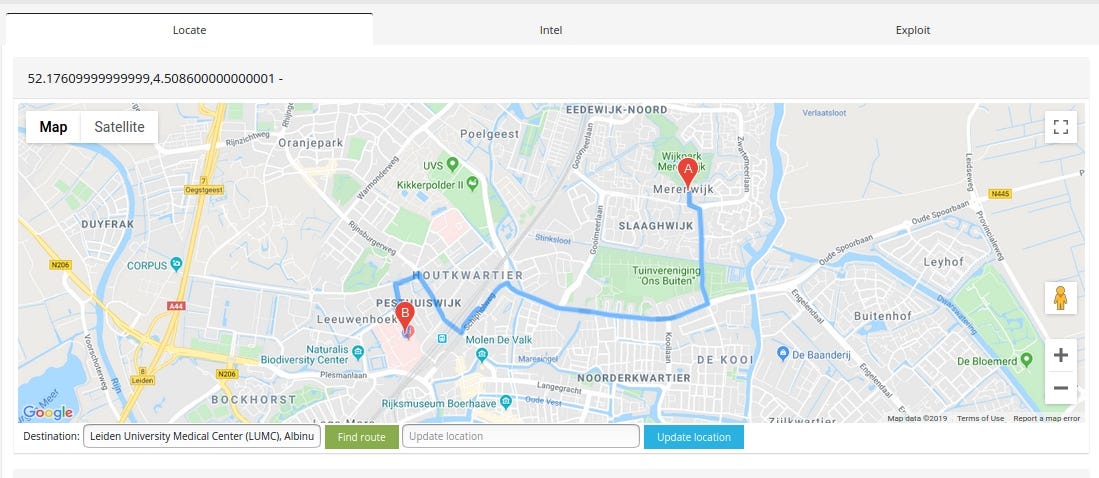
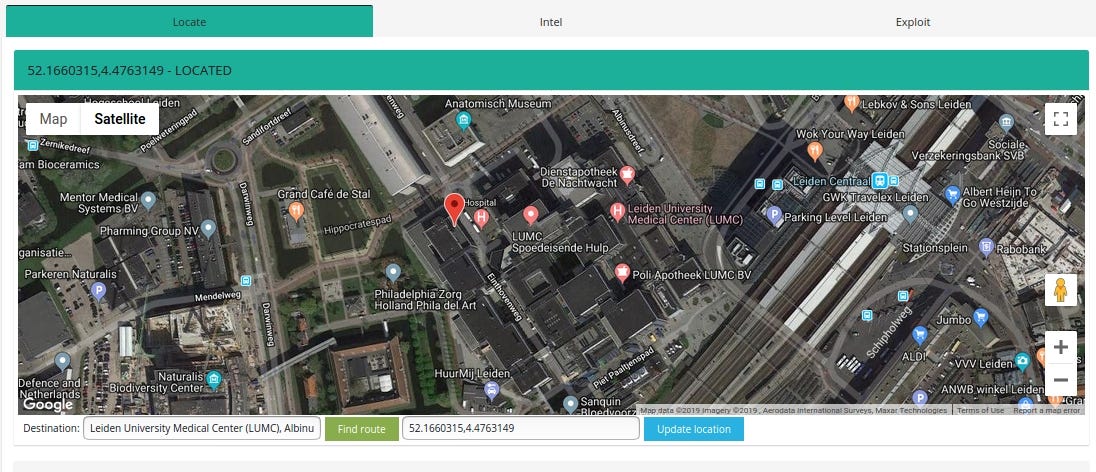
Case #4 Leiden University Medical Center (LUMC), Albinusdreef 2, 2333 ZA Leiden, The Netherlands
BrainScope® is a medical neurotechnology company that is pioneering the assessment of brain injury, including concussion. The company’s innovative BrainScope One system is an easy-to-use, non-invasive, hand-held platform that empowers physicians to quickly make accurate head injury assessments at the point-of-care. https://brainscope.com/
Query: title:BrainScope
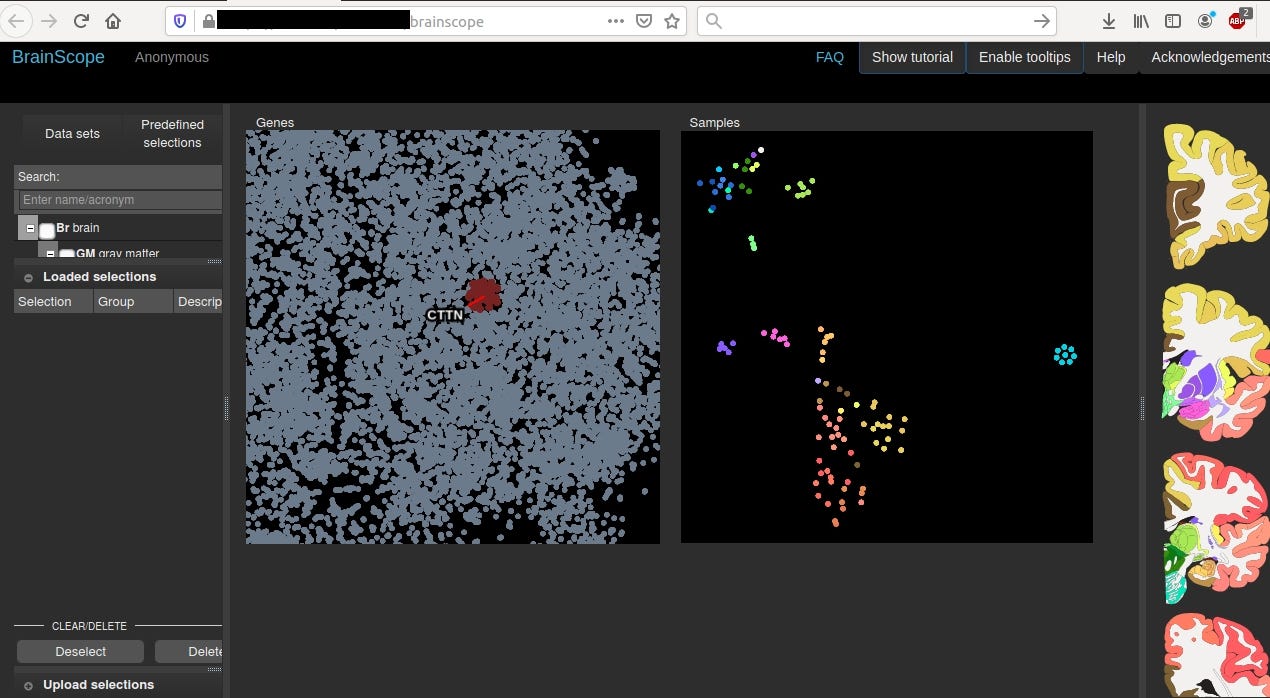
This machine is located in net range of “Leiden University Medical Centre”

which is very close to location obtained from geolocation database that Shodan uses.
Bonus
Why hospitals are victim of ransomware?
Screenshots via Shodan


So, you can see that you are just one step to obtain critical information about patients, personnel or hospital infrastructure.
Password guessing, credential stuffing or phishing is typical entry point for attacker to start infection and deploy ransomware or steal medical data. Also medical equipment is so sensitive that it’s dangerous to make any updates therefore a lot of systems are vulnerable not only to the newest exploits like Bluekeep but also to really old ones.
You can make a list of hospitals or medical clinics in your town/country that could be next target due to lack of basic security measures.
Other Interesting findings
I had to exclude couple of devices due to difficulty of getting common indicator (suitable Shodan query) or small amount of them. You can review it manually, they are attached to ꓘamerka however are not implemented. I monitor these devices and will add more if I see there is a peak in exposing them.
Beside mentioned findings that could be geolocate, I found more that I want to share.
Wall of Analytics
It’s solution from General Electric, which works as command center to process real-time data across hospital using AI.
This Wall of #Analytics processes real-time #data from multiple sources and systems across the hospital https://t.co/66NEzi440I pic.twitter.com/VlVhRgFVkN
— Hard at work for those on the frontlines (@GEHealthcare) January 24, 2018
The Digital Hospital: Mission-Control-Like Command Center At This Hospital Is Taking Healthcare Into The Future

Microscopes
I don’t see any point of connecting microscopes to the Internet but it happens.
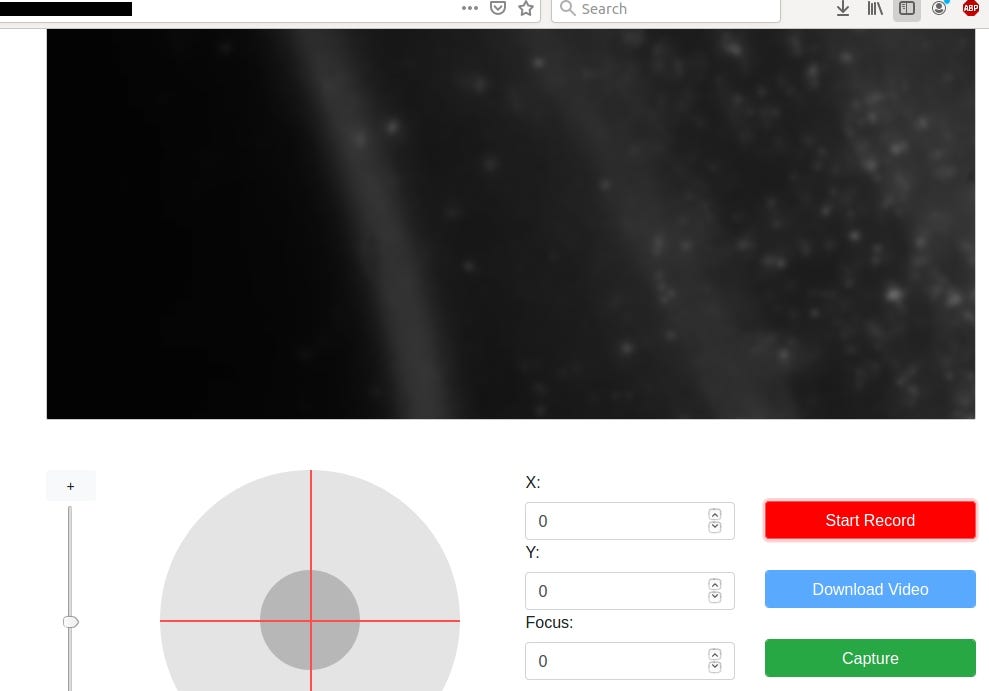
It allows you to record what is going on, calibrate it and download video.
Nurse Call Messaging System
There are platforms that I had no idea even exist. One of them is messaging call service for nurses. Again, it should be isolated from external network, even if it’s in the cloud.

This solution allows to monitor each room, it’s temperature and when patient needs help.
HoF Perioperative
Another product from General Electric Healthcare — Health of Future Perioperative is used to manage operating rooms. It’s hard to find any information about this software like default passwords or actual version.

Orthanc Explorer
It’s yet another DICOM viewer software. It allows to check patient’s X-Ray scans and other medical info. A lot of Orthanc instances are open without any authentication.
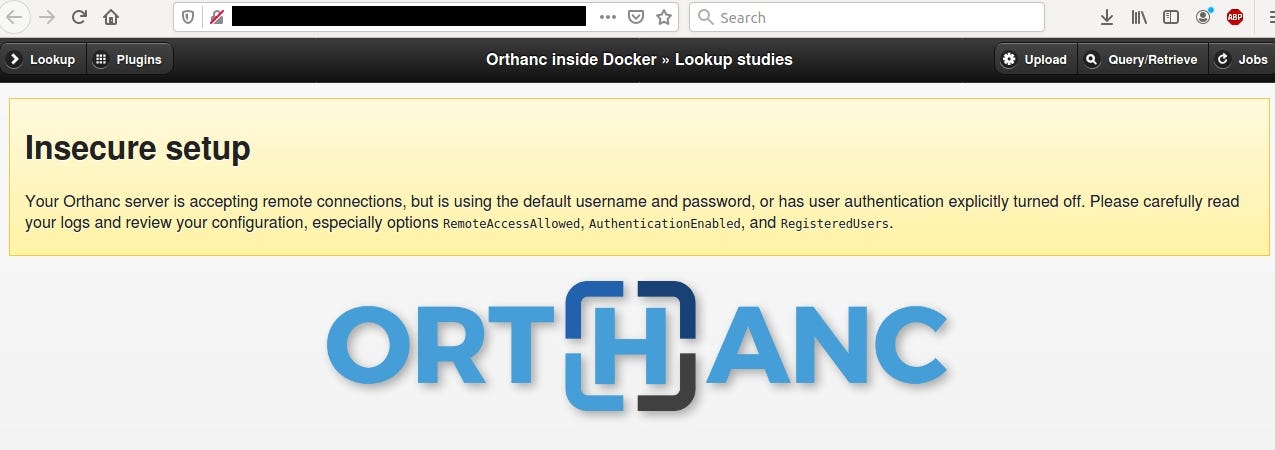
It’s all fun and games until some script kiddies start to test it without proper authorization.

If you want to test functionality and GUI of this software, you can check out demo that’s publicly accessible.
https://demo.orthanc-server.com/app/explorer.html
Don’t test device/software you don’t own
Information disclosure
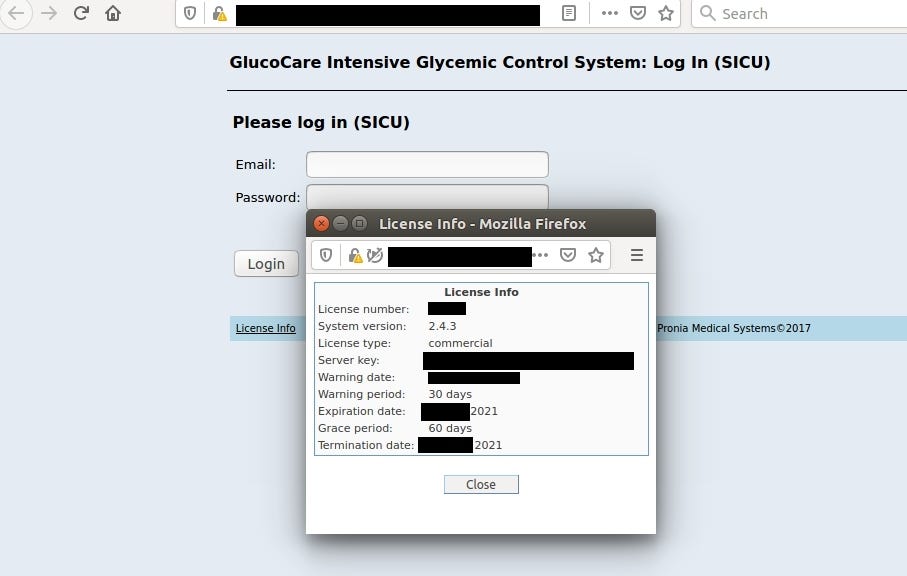
GlucoCare Glycemic Control System
Insulin dose calculation software developed and marketed by Pronia Medical Systems https://proniamed.com
It reveals server key and license info in login panel
KbPort
Leverage the full power of your simulation lab…
Whether building a new simulation center or expanding or renovating an existing center, KbPort Simplicity™, an end-to-end solution that begins with designing the ideal environment, meets the needs of any facility setup. https://kbport.com/
Internal infrastructure is exposed in login panel

Bonus — Optical Coherence Tomography
Open Source Intelligence is not about knowing everything but about finding proper information and acquainted it as fast as possible to use it for specific purpose.
When you have no idea about device/software or any other finding, you should always depend on documentation that can be easily found from different sources.
It’s machine for optical coherence tomography and according to official site: Provides High-speed Scan, High-quality Image by using Huvitz’s outstanding optical technology and innovative image software. Shows extensive information, such as 3D structure of Retina, Macula’s thickness and separation, in a vivid image.
http://www.huvitz.com/oph_eng/product/HOCT-1.html
If you don’t know how to use this device or what kind of information it may contain, you need to find a manual guide.
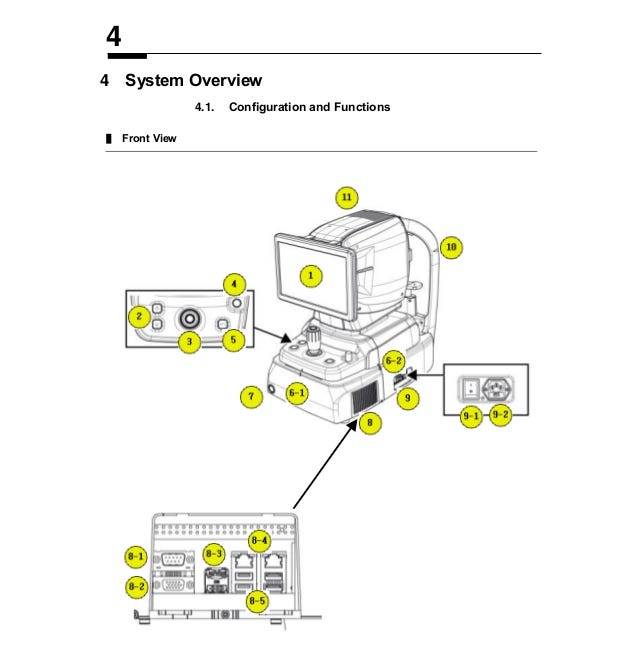
It includes everything that you need to know about the device — from safety precautions, system overview or troubleshooting. Some of the manuals contains default password and installation guide as well.
Additional ICS update including open Human Machine Interface and RCE vulnerable Bosch Security DVR Systems.
During third phase of the research (targeting vendors), I have discovered not only medical devices but also Industrial Control Systems. Some manufacturers does not equip only hospitals but produce and support different industries as well.
One example of this type of company is Bosch. It provides blood pressure monitors or capsule checkweighers for healthcare. From the other hand Bosch manufactures security systems and many many more IoT and ICS products that are broadly used all over the world. Trying to find medical devices I came across Bosch Security Systems DVR 630/650/670 Series with query: http.html:’Bosch Security ‘.
There are around 600 of these devices exposed to the Internet. In HTML source code I found multiple cgi paths that can be abused. Big thanks to @ChristiaanBeek who confirmed the vulnerability and found an exploit for this device. The exploit is public and it’s from 2014, according researcher, Bosch hasn’t responded so he published his discovery.

It allows to completely takeover device — including shell access, sensitive information disclosure or retrieve usernames and passwords.
I mainly focused on last part — usernames often indicates name of the facility that device operates in. It’s base64 encoded so it’s not hard to retrieve actual username.

One of the exposed username is UE9MSVRJ which means POLITI after decoding. You can see that devices are running even in sensitive places like Police and it seems that Bosch won’t fix the vulnerability and clients hasn’t been informed about it.
I constantly observe new Shodan queries that are shared from various sources. This small ICS update contains 11 new devices like: Miele@home, InFusion System Robust Lighting Control, FloTrac, Innotech Control Systems, Sensoteq or AutomationDirect. Full list you can find here → https://github.com/woj-ciech/Kamerka-GUI#full-list-of-supported-devices-with-corresponding-queries
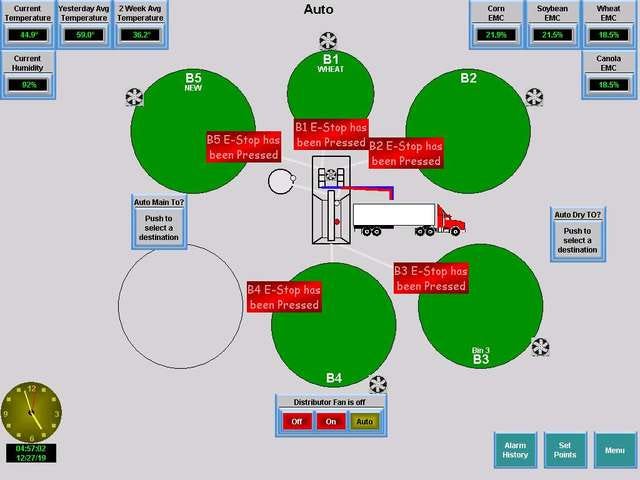
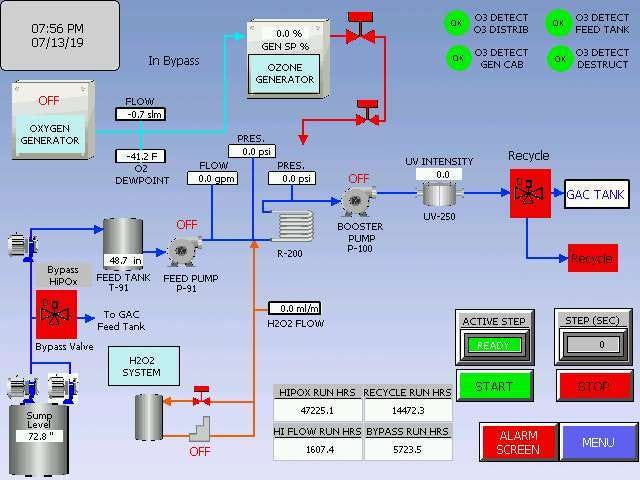
The case of AutomationDirect is quite interesting because there are many open HMI in many places which count as critical infrastructure. Shodan retrieves screenshots so we can sneak a peak what’s inside and whom it belongs to.
query: Server: EA-HTTP/1.0
Screens via Shodan
Conclusion
Healthcare industry is very fragile and should be treated with additional security in mind. It’s not only about personal information like in other industries but it’s also about people lives that are in danger in case of cyber attack or unauthorized access to the hospital systems. A lot of devices are exposed to the Internet what makes them easier to target and compromise, in addition there are plenty of vulnerabilities that should be patched and mitigated. The hospital is as secure as it’s weakest point, attackers can gain initial access through open Remote Desktop Protocol and escalate his privileges to whole network making live supporting devices inaccessible. That’s why it is so important to carry out security tests in healthcare clinics and hospital to mitigate potential security holes that may danger hospital infrastructure and patient’s lives.
Originally published on 27th of December, 2019
Please subscribe for early access, new awesome things and more.





