With LeakLooker you can find publicly open MongoDB, CouchDB and Elasticsearch database, it also includes Kibana instances. Script parses results from Shodan, excluding empty and compromised databases. Everything is sorted and presented in clickable way.
You can find script here
Introduction
We have seen a lot of leaks from different sources — Amazon buckets, Firebase, Gitlab, Rsync protocol and lot lot more. The most common mistake leading to leak is lack of basic security knowledge, untrained people and in some cases laziness. Due to small mistakes, whole company can be compromised and if we take GDPR into account, penalties can be devastating.
Manually searching in Shodan is tedious because it shows everything which listens on specific port — empty and already hacked database. LeakLooker takes the results and shows only instances bigger than 217 MBs and accelerates your hunt. In some cases it was hard to exclude hacked databases, because when hacker left ransom note, data are still present, it applies to Elasticsearch and MongoDB. Among found information by script, there were a lot of personal identification information (PII), medical data, casinos transactions, credit card owners data, GPS tracking information, archived data of accounts of specific groups in social media, API tokens, sensitive logs and documents and lot more. To make it more interesting, you can specify page from which results will be displayed, makes it easier to find things that no one was looking for before. Additionally, origin country and names of databases (MongoDB, CouchDB) or indices (Elasticsearch) are showed.
CouchDB
CouchDB is document-oriented NoSQL database, using JSON and JavaScript as a query language. To be honest, I haven’t heard about any serious leak from CouchDB however it contains fragile data like every other type of database. Usually it uses port 5984. Additionally, for clarity you can review CouchDB via administration interface called Fauxton. Script gives you direct link to ‘_utils’ path where Fauxton is located. It happens sometimes that is password protected but it’s still possible to access data directly querying db and use commands like ‘_all_dbs’ and ‘_all_docs’. Following this, documents and attachments can be retrieved and then downloaded. I’m not even saying about possibility to tamper data, because in most cases it allows you to write and delete whole database.

Useful commands:
/_all_dbs
<db>/_all_docs?include_docs=true&limit=50
/<db>/doc?rev=<nr>
<db>/doc
<db>/doc/<name>
/<db>/<docid>
/<db>/<id>/<attachment_id>
Shodan query:
product: CouchDB
MongoDB
MongoDB is another cloud NoSQL database which uses JSON structure. A lot was said about leaks from MongoDB and I found a lot of compromised DBs in the wild. Response from open MongoDB contains all collections in database and diagnostic or debugging information. Script focuses only on size, databases and collections. This is the only case when web interface is not accessible except of administration website which listens on port 28017, thousand higher than standard MongoDB port (27017). Connection to the database is made by command mongo — host <host> — port 27017 and next command ‘show databases’ is used for showing all databases.
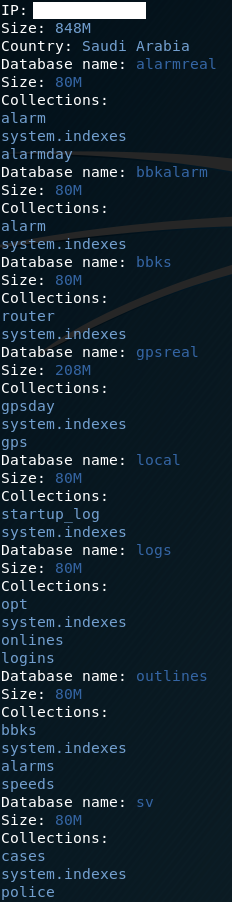
Useful commands:
show databases
use ‘db’
show collections
db.’collection’.stats()
db.’collection’.findOne()
db.’collection’.find().prettyPrint()
db.’collection’.find()
Shodan query:
product: MongoDB
Kibana
Kibana lets you visualize data from Elasticsearch, in most cases it’s used for monitoring devices and presenting it as a graphs or charts. However Kibana is also known for revealing sensitive data, one of the most infamous cases was mobile spyware company. It cannot be determined if instance is open or not, like it is in other databases, so I had to use special query to retrieve only these instances that can be accessed without authentication. I found out that there is a difference in response when login is required and when it’s not. To be precise, header Content-Length has value around 68407 bytes when Kibana returns login panel and exactly 217 bytes when it is publicly open and returns dashboard. Armored with this knowledge, Shodan query looks following: ‘kibana content-length: 217’ and since it has no filter, it does not use your Shodan credit. It is exact query so you will have 100 results per page. As mentioned earlier, it’s clickable and link leads you directly to discover panel where you can explore contained data.
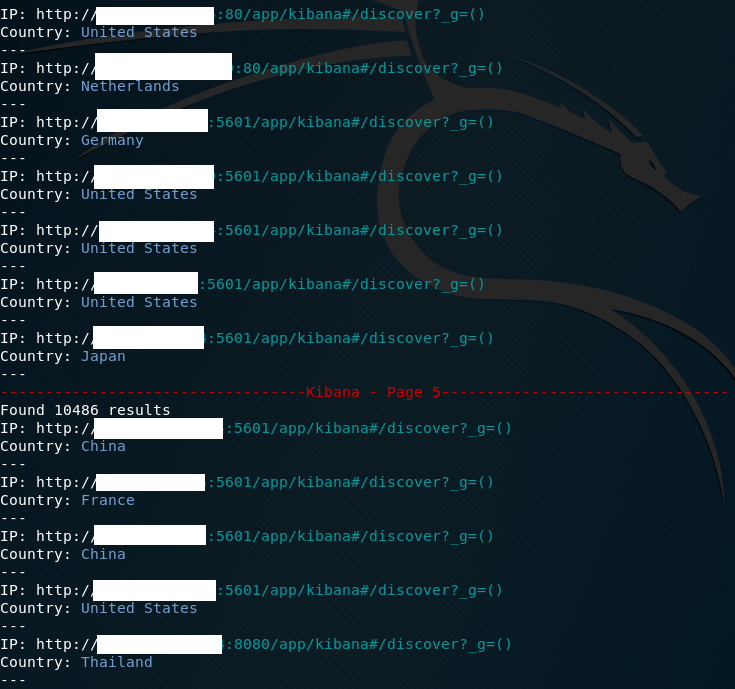
Shodan query:
kibana content-length: 217
Elasticsearch
Another cloud database known for infamous leaks is Elasticsearch. Actually, according Wikipedia it is search-engine, which can be deployed in the cloud and provides you web interface on port 9200. What is interesting here, Elasticsearch has no authentication at all and owner should care about not exposing his instance without proper login mechanism. That’s why it happens so often that it’s easy target for cybercriminals. Each Elasticsearch cluster has an indices or indexes, it may be compared to the database in typical MySQL.
Official documentation explains it in following way:
MySQL => Databases => Tables => Columns/Rows
Elasticsearch => Indices => Types => Documents with Properties
Script shows links to ‘_cat/indices?v’, which next presents all indices in database including theirs size. You can access each index with command ‘<indice>/_search?size=50’

Useful commands:
_cat/nodes?v
_cat/count?v
<indices>/_search?size=50
Shodan query:
product:elastic port:9200
Conclusion
Script has been made as a proof of concept to share awareness how companies and institutes handle your data. I’m sure that Chinese, American or Russian hackers have something more sophisticated to scan the Internet and look for free information, which then can be used for espionage. Cybercriminals also takes advantage of insecure database to force ransom from companies. Moreover, researcher companies like UpGuard also takes advantage of different open databases, so why independent cyber-researchers cannot check what is going on in intelligence gathering world? And remember, act responsible and if you see something, report it.
Originally published on 8th of January, 2019
Please subscribe for early access, new awesome things and more.



