New update for Kamerka allows to map Industrial Control Systems of whole country. As in previous version, interactive map is created but this time Google Street View has been added in order to take you for a virtual walk near found ICS devices.
I will present final map and some statistics on the example of Poland and Switzerland.
Code is still here
Introduction
Industrial Control Systems (ICS) are systems/devices that are responsible for managing factories, power plants, hospitals or even traffic lights. Everyone knows how fragile these systems are and how outages may disrupt normal functioning of a city or country. The most famous cyberattack against ICS (except Stuxnet) had place in Ukraine in 2015 with BlackEnergy malware, however it’s not only strain of malicious software attacking ICS. Next example can be Industroyer or Triton, which code has been leaked and was analyzed, I recommend you to read the analysis to know how complex it is what damage it can cause.
In general, ICS shouldn’t be connected to the Internet but in order to save money, companies allow technicians remote access to this systems and create additional risk. Moreover, ports like HTTP, FTP, SSH, SNMP are accessible which potentially makes machine more vulnerable to different attacks. I even came across machines with VNC or SMB open. It confirms bad security practices and lack of network segregation.
Knowing history, i.e. attack on Ukraine, one should pay more attention to things that are exposed to the internet with other services that might help attackers to compromise machine or exfiltrate data in other way. Current Kamerka update gives you possibility to enumerate ICS device in specific country including localization and Google Street View photos.
Now it is fully functional recognize-intelligence gathering platform for specific location or Industrial Control Systems. It can be used in two parts, first enumerates localization of ICS and second part looks for cameras and social media photos nearby previously found industrial systems. This way you can gather full geo-intelligence (localization, cameras in neighborhood, google street view and social media photos) and also data intelligence (IP address, hostnames, services or open ports).
How it works?
First version of Kamerka included only exposed cameras, then social media photos have been added and now you have possibility to visualize Industrial Control Systems of any country. The data source is still Shodan and following filter are used:
- port:502,102,47808,44818
- port:1911,4911 product:“Niagara Fox”
- port:20000 source address
- product:”general electric”
- port:20547,1962 PLC
- product:“Mitsubishi”
- port:9600 response code
- port:789 product:”Red Lion Controls”
- port:2404 asdu address
- port:2455 operating system
(with additional filter „country” with two letter short code of country as a value.)
Which means that following devices and products are checked:
- Modbus
- Siemens S7
- Tridium
- General Electric
- BACnet
- HART IP
- Omron
- Mitsubishi Electric
- DNP3
- EtherNet/IP
- PCWorx
- Red Lion
- Codesys
- IEC 60870–5–104
- ProConOS
It checks whether specific port is open or if device is a product like „Niagara Fox” or „Mitsubishi”. To be perfectly sure that this is ICS, script looks for „ics” tag in Shodan’s response. Then, with help of Folium library, map is created with photos from Google Street View.
You need additional API key for Google with Street View with billing activated.
Most of the location points to unspecified buildings, but in some cases I was able to find hospitals or power plants. Additional link to Shodan has been added to get more knowledge about particular host. It’s worth to mention that every host requires additional research, you can check what exactly belongs to this network with filter „net:IP” or what other devices are located in this place with „geo:LAT,LONG,RADIUS” filter.
Limitations
I had to connect couple filters into one in order to save API credits. From this same reason, only first page is checked, sometimes is enough knowing there are only 40 Niagara Fox devices in Poland. Each of the filter can be substituted with one „tag:ics” but it’s only available in enterprise version. If you need to adjust the script to enterprise version, let me know.
Following research is based on aforementioned limitations.

Research
Poland is very specific country because of it’s localization, which is in the middle of the Europe and creates sort of bridge between East and West. It is also interesting study case to show whether Poland can be second, after Ukraine, industrial cyber-battlefield.
Based on previously mentioned filters I enumerated 253 machines running different Industrial Control Systems, then I took geolocation and visualize it in form of map with clusters. Based on this, you can gather info where systems are located, if not exact location at least city is extracted.
I started this research with hope to find lot of power plants, factories and test their physical security with Google Street View and exposed cameras pointing this specific place. I found only couple places like factories or hospitals and rest of them are just completely other places, it’s also good study to show how geolocation data are precise, or not.
The map below presents industrial systems found on Shodan.
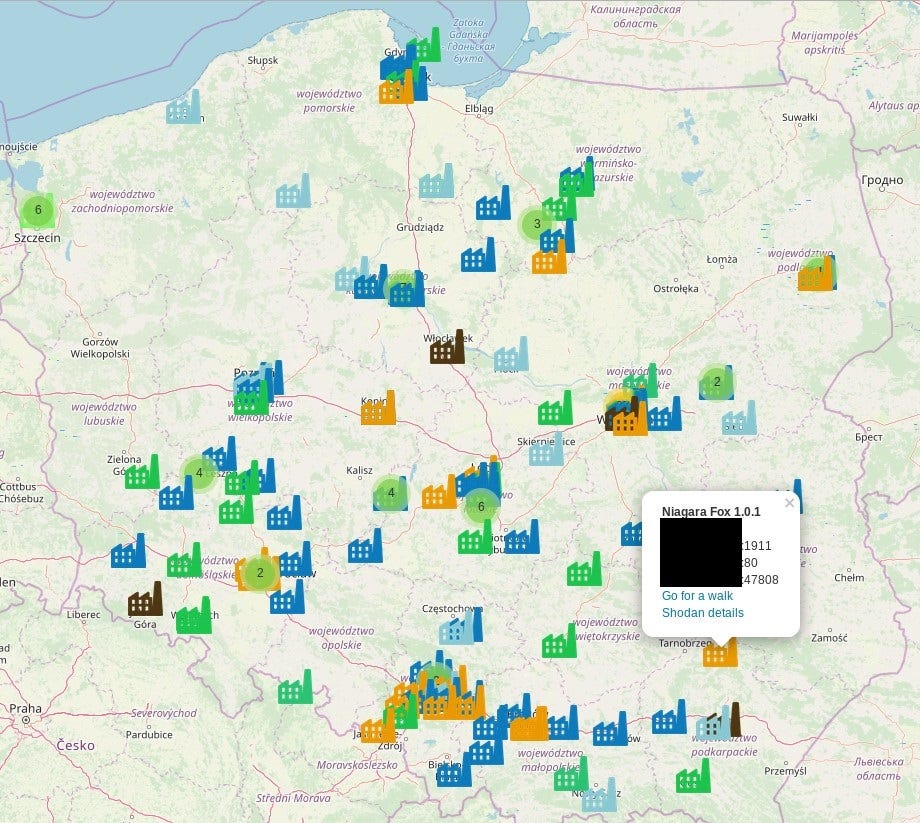
We can clearly see more „urbanized” places like Silesia (South part) and capitol Warsaw (central east). Each color means different systems, for instance orange is for Niagara Fox. If you have found actual plant or interesting place worth to visit, you can click „Go for a walk” which takes you to this specific location in Google Street View.

If you believe you have found place where industrial control systems are running, you can examine it’s physical security. By this I mean, entrances of the building, windows, security cameras or parking lots nearby. It’s good to have tool for red team assessments to plan operation.
Another security aspect of ICS security is the server itself. A lot of machines has additional ports open, mostly it is HTTP with login pages, which reveals manufacturer and version of the software. This presents another risk in form of default credential use and vulnerability check.


As presented most pages operates on ports 80,81,8080,8081 without HTTPS.
Kamerka gives you insight what other services and ports are open on the machine. Apart from above mentioned HTTP/S (80,443,8443,8080), devices in Poland expose SSH (22), FTP (21), VNC (5900) SNMP (161) and PPTP (1723).

Next chart presents use of each Industrial Control Systems manufactures, you can find full list of checked products and the beginning of article. We see that large part is covered by Codesys, second place is for Modbus and on third place Niagara Fox is located. It clearly shows that there is no sense to develop malware and attack BACnet systems since only 11 machines are located in Poland.

To compare the results I took small western country with lot of potential and allegedlly being neutral — Switzerland. Script was able to find 199 machines.
Geolocation of ICS is presented below
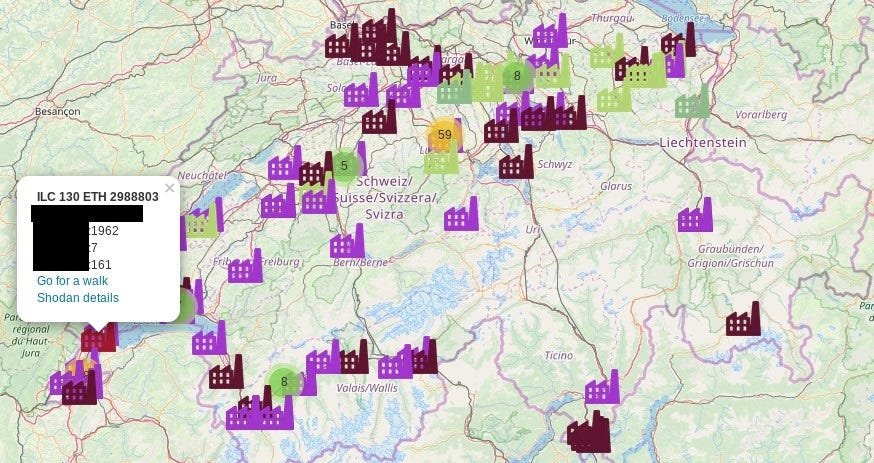
„Exposed ports” chart presents that telnet is still in use in 25 cases (in Poland it was 12) and also DNS runs on 16 machines (11 in PL). Still lot of HTTP ports are open, 31 FTP and 10 SSH.

Results of ICS products are very similar to the Polish ones. Leader is port 2455, which Codesys operates on. Modbus and Niagara Fox are on the next places. It happens that some of the machines has more that one ICS port running that why total number is higher than number of machines.
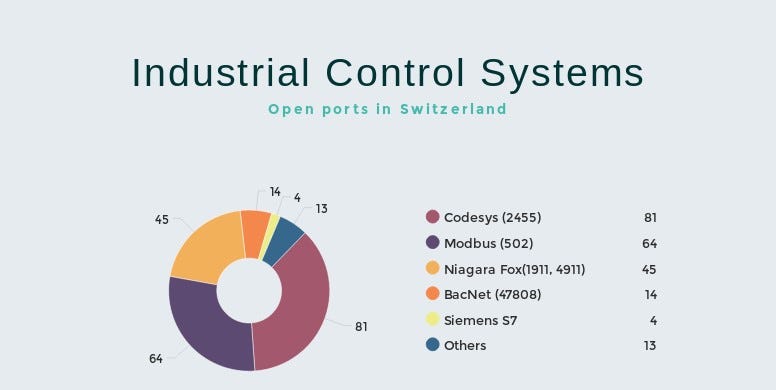
Even with the mentioned limitation, it was possible to enumerate the trends in products and manufacturers. If we add location of the servers, we can precise it to specific organizations and buildings. At the end we can finish with total intelligence report for specific country including the most interesting cities or places, with social media photos, Street View and cameras in neighborhood.
If someone need access to raw data or map from this research, please let me know.
Conclusion
Attack or defense, both sides need good intelligence especially when fragile and very sensitive systems like ICS are in play. Functioning of the city/country depends of these devices and lives may be in danger in case of outage or intentional cyber-destruction. That’s why it is important to monitor every device connected to the internet which might pose risk to the factories, plants, hospital, airplanes or other important structure of the country.
Originally published on 9th of June, 2019

Please subscribe for early access, new awesome things and more.



