The one and only situational awareness platform OS-Surveillance is evolving faster than ever, integrating powerful new data sources and innovative features designed to make real-time geospatial intelligence gathering super intuitive.
In today’s episode, I will walk you through the latest enhancements to the platform and share insights into the world of live geospatial OSINT.
We will explore why geospatial context is crucial for situational awareness, how to harness real-time data feeds effectively, and what tools and techniques can give you the advantage if you are in security, journalism, emergency response, or simply someone who wants to stay up to date with everything what is going on in the world.
Big changes to the situational awareness system: smarter anomaly detection, better filtering, and deeper context across air, sea, and ground data. It’s now easier to focus on what’s happening, where, and why. Try it on https://t.co/LzCES00cwK #osint #geospatial #intelligence… pic.twitter.com/fL6L7OKPNt
— Offensive OSINT (@the_wojciech) May 29, 2025
Try it for free and share your thoughts or feature requests

Introduction
For quite some time now, os-surveillance.io has evolved significantly and it's not just a tool or data aggregator anymore but a comprehensive, all-in-one system for geospatial and situational awareness investigations. With powerful features for correlating events, tracking individuals, and monitoring locations in real time, the platform supports even the most complex OSINT workflows, making research faster, smarter, and more efficient.
One of the latest updates brings even more value - the ability to detect contextually significant anomalies within your chosen area of interest. Whether you're scanning for aircraft or maritime activity, you no longer need to look through every single detection to spot something unusual. The system automatically flags aircraft or vessels used by military, law enforcement, or medical services, providing immediate hints that something operational or critical may be happening.
In this post, I will walk you through how this feature works under the hood, and share what to consider if you’re building a similar system. From anomaly detection to contextual enrichment, this is how modern geospatial intelligence should work.
Latest updates
It’s been a while since my last update, that’s because I’ve been deep in development and research to make the system better and better. While a few sneak peeks were shared on Twitter, it’s time to give a proper rundown of the latest features.
One major addition is the new Share button, which lets you generate a direct link to any event and send it to anyone, no account required. It’s perfect for quick collaboration or public sharing. Try to access this https://osint.os-surveillance.io/#/shared/events4/abd2c649-12b0-48f8-874b-f0242d79a9ed
But that’s just the beginning. You can now:
- Add custom markers directly on the map,
- Search for active fires in real time,
- Instantly gather description of critical infrastructure facilities,
- Access data on US missing persons
OS-Surveillance now provides access to US missing persons data. Search cases by location or access the latest ones in the dashboard. Use hashtag/username search, facial recognition or extract and correlate activities in nearby areas. Try it on https://t.co/LzCERZZEHc #OSINT… pic.twitter.com/W9DiqlIIBx
— Offensive OSINT (@the_wojciech) April 28, 2025
- Access latest crimes in UK
To all my UK followers, get free access to the latest crime data and stop-and-search events across the UK. Explore locations, analyse trends, and export data for deeper insights. Register and try on https://t.co/sXiTUvAUP1 #OSINT #geospatial #intelligence #geoint… pic.twitter.com/YIDjP5tox7
— Offensive OSINT (@the_wojciech) March 16, 2025
- View contextual info about the author of a post or the owner of a vessel or aircraft, right from the map tile.
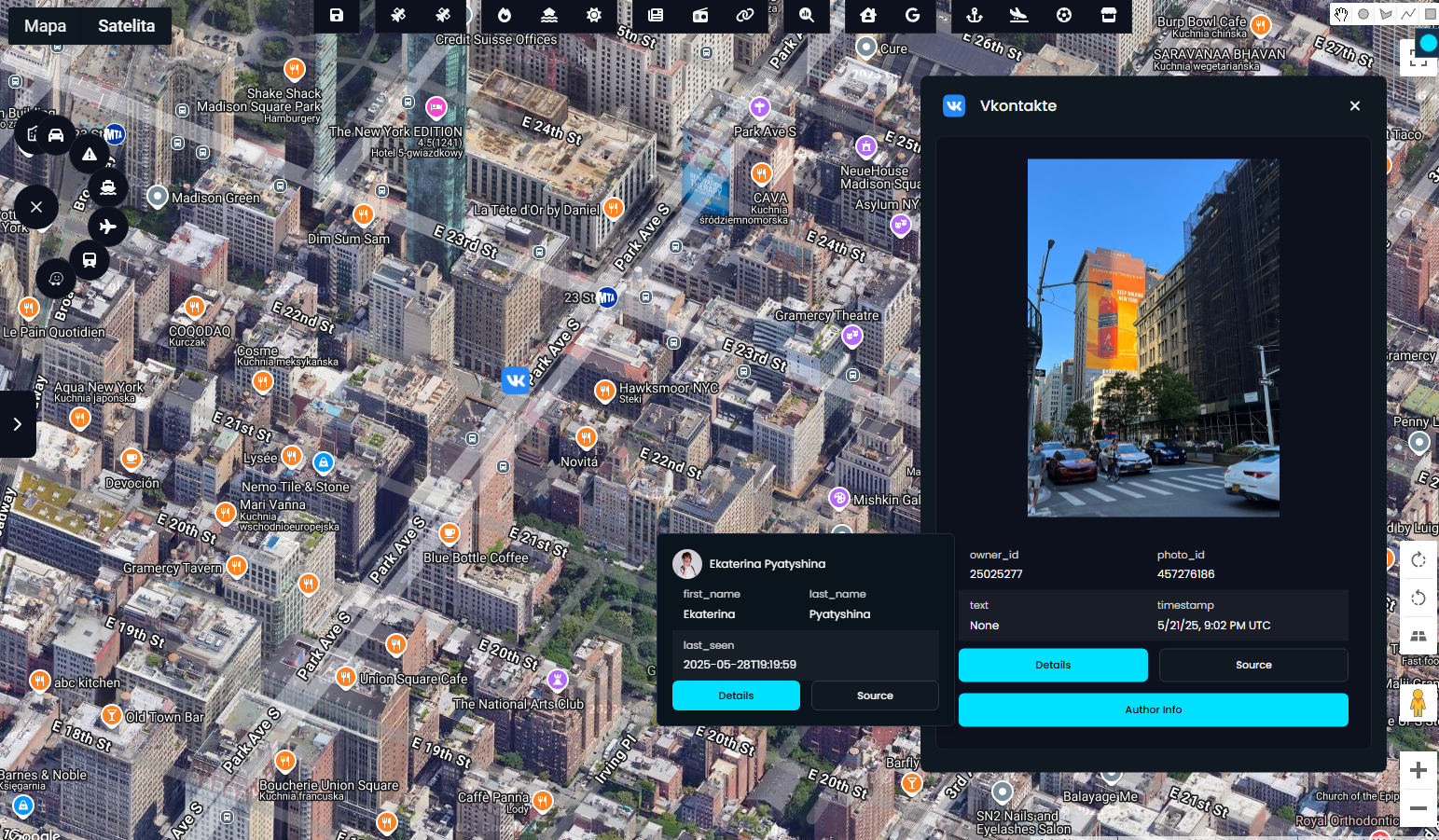
Each of these updates moves us closer to the vision of a truly interactive, real-time situational awareness system. And to achieve that vision, the system must do more than just display data. It needs to intelligently detect anomalies and extract suspicious or meaningful activity as it happens.
Anomaly & suspicious activities
Anomaly (noun) - a deviation from the normal or expected pattern.
When working with large volumes of variety geospatial data, one of the biggest challenges is real-time categorization and correlation. Surfacing meaningful signals from noise. right at the time of search is no easy task. That’s exactly what this latest update addresses.
I'm happy to introduce a text-based anomaly scanner that analyses indicators from multiple data sources to identify whether a vessel or aircraft should be flagged as potentially suspicious. It cross-references callsigns, aircraft types, and contextual patterns to surface anomalies automatically with no manual filtering required. Alongside that, the system presents the latest relevant social media activity and crime reports in the same area, enabling rapid situational awareness and recon.
Vessels & Planes
By analysing metadata like callsigns, registration numbers, and aircraft or vessel types, the system can infer their origin and intent. For example, aircraft used by military, law enforcement, or emergency services are immediately highlighted when they appear in a monitored zone.
On the interface, you’ll see a dedicated tile on the left-hand side displaying potentially suspicious air or maritime activity. In one instance, you can view details of a flagged aircraft idling on the tarmac, suggesting something operational may be underway.
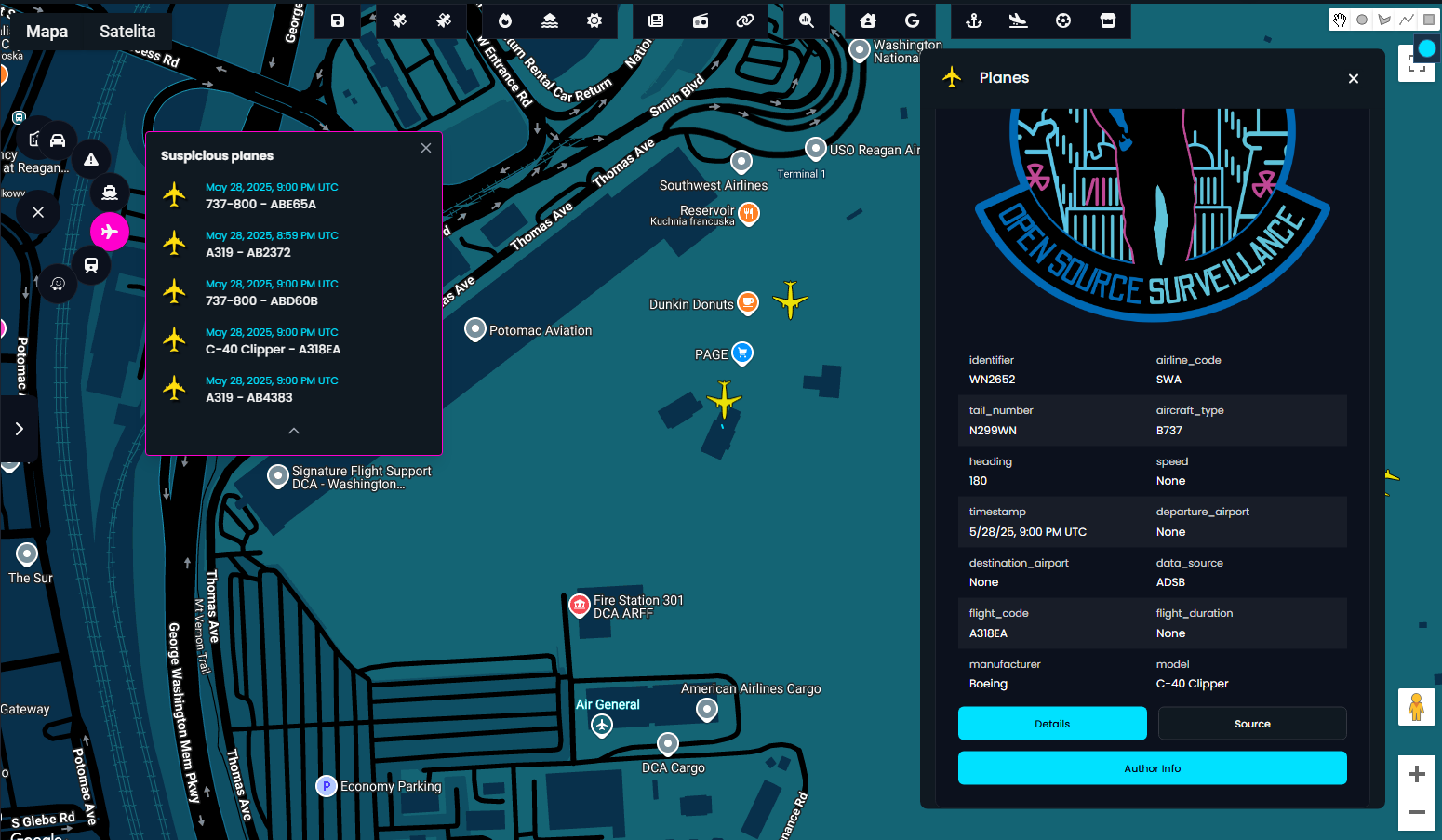
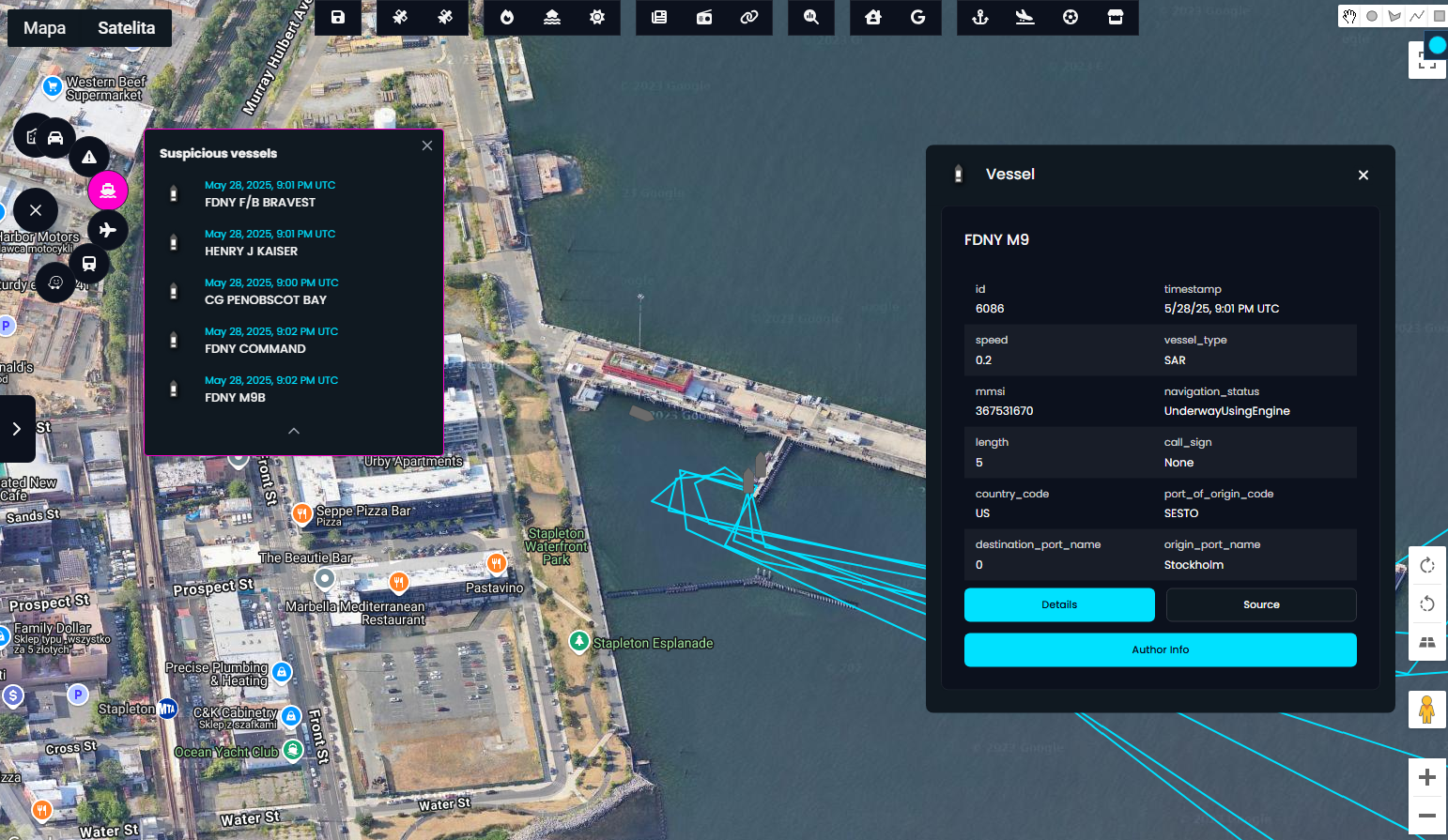
The second screen focuses specifically on Military, Law Enforcement, and Search and Rescue (SAR) vessels that are broadcasting their positions via AIS. These assets are automatically filtered and displayed in a dedicated tile immediately after a search is completed.
When scanning for aircraft or vessels of interest, the key identifiers are the callsign and the type or model. These details often reveal the aircraft’s function, whether it’s a civilian flight, surveillance aircraft, or a military asset.
The system uses a curated list of callsigns and aircraft types to automatically highlight potentially suspicious or operational planes currently in the air. This filtering mechanism helps focus your attention on what matters most without the noise.
Below, I'm sharing a list of callsigns and models used by the platform to identify and track these high-priority aerial assets in real time.
SUSPICIOUS_CALLSIGN_PREFIXES = [
# US Military & Government
"RCH", "SPAR", "FAME", "SAM", "MC", "PAT", "CNV", "VM", "VV", "RFF", "GNY",
"RDR", "AX", "DUKE", "EAGLE", "REACH", "BISON", "ROMA",
# VIP/Executive Support
"EXEC", "GOV", "USA", "USAF", "USN", "USCG", "USMC",
# NATO & Allies
"NAF", "GAF", "BAF", "CAF", "RCAF", "CFC", "TURAF", "RSD", "IAF", "AFR", "KAF",
"ASY", "NZDF", "HAF", "HUAF", "SIAF", "PLF", "MLU", "PAF", "RSAF", "JAF", "UAEAF",
# Surveillance, Recon, Intelligence
"JANET", "TEAL", "BRIO", "NIGHT",
# Medevac / SAR / Humanitarian
"MEDEVAC", "LIFEGUARD", "RESCUE", "MEDIC", "HEMS", "AMBULANCE", "NGO", "HOPE",
"REDCROSS", "RELIEF",
# Border Patrol / LEA
"CBP", "BP", "COBRA", "FRONTERA", "GUARDIAN", "LAW", "USCBP",
# Coast Guard / Maritime Surveillance
"COASTGUARD", "CG", "OCEAN", "SURV", "GUARD",
# Masked or suspicious
"BLOCKED"
]and aircraft types
SUSPICIOUS_AIRCRAFT_TYPES = [
# Strategic airlift / refuel
"C17", "C5", "C141", "K35R", "KC135", "KC10", "A330M", "A310M", "A400", "IL76", "IL78",
# Tactical airlift
"C130", "C30J", "CN35", "CN295", "AN26", "AN72", "AN12", "Y7", "Y8", "Y9",
# VIP / Govt Jets (also used by CIA, State Dept, etc.)
"GLF5", "GLF6", "GLF4", "CL60", "CL65", "CL30", "CL35", "FA7X", "F900", "E35L", "E145",
"B703", "B707", "B733", "B735", "B737", "B738", "B752", "B762", "B763", "A310", "A319",
"A320", "A321", "A330", "DC10", "MD11",
# ISR / Surveillance / Reconnaissance
"P8", "R135", "EP3", "E3CF", "E4", "E6", "E8C", "U2", "MC12", "RC26", "RC135", "S100",
"D328", "BE20", "B350", "DASH8", "AT72", "DA42", "DA62", "C560", "C25B", "C650", "LJ35",
"LJ45", "C500", "C501", "C550", "C680", "F406", "G159", "GIII", "GIV", "HDJT", "SABR",
# SAR / Medevac / NGO / Aid
"C208", "PC12", "BE20", "BE58", "PA31", "PA46", "P68", "PZL", "S92", "S76", "A109", "AW109",
"AW139", "BK17", "EC35", "EC45", "AS65", "UH60", "HH60", "MH60",
# Helicopters — Law Enforcement, SAR, Military
"UH60", "CH47", "MH60", "HH60", "AH64", "OH58", "SH60", "CH53", "EC35", "EC45", "MD50",
"MD52", "MD53", "MD60", "AS50", "AS55", "AW109", "AW139", "S61", "S92",
# Drones / UAV (if visible via ADS-B)
"RQ4", "MQ1", "MQ9", "RQ7", "RQ9", "WASP", "HERMES", "HERON", "PHANTOM", "PREDATOR",
# Masked Civilian or Contractor Bizjets
"C25B", "C56X", "C750", "CL35", "LJ35", "LJ45", "LJ60", "GLEX", "HDJT", "F2TH", "F900", "E50P"
]Vessels can be filtered by type
vessel_type = ['Military Ops', "SAR", 'Law Enforcement']Industrial Control System devices
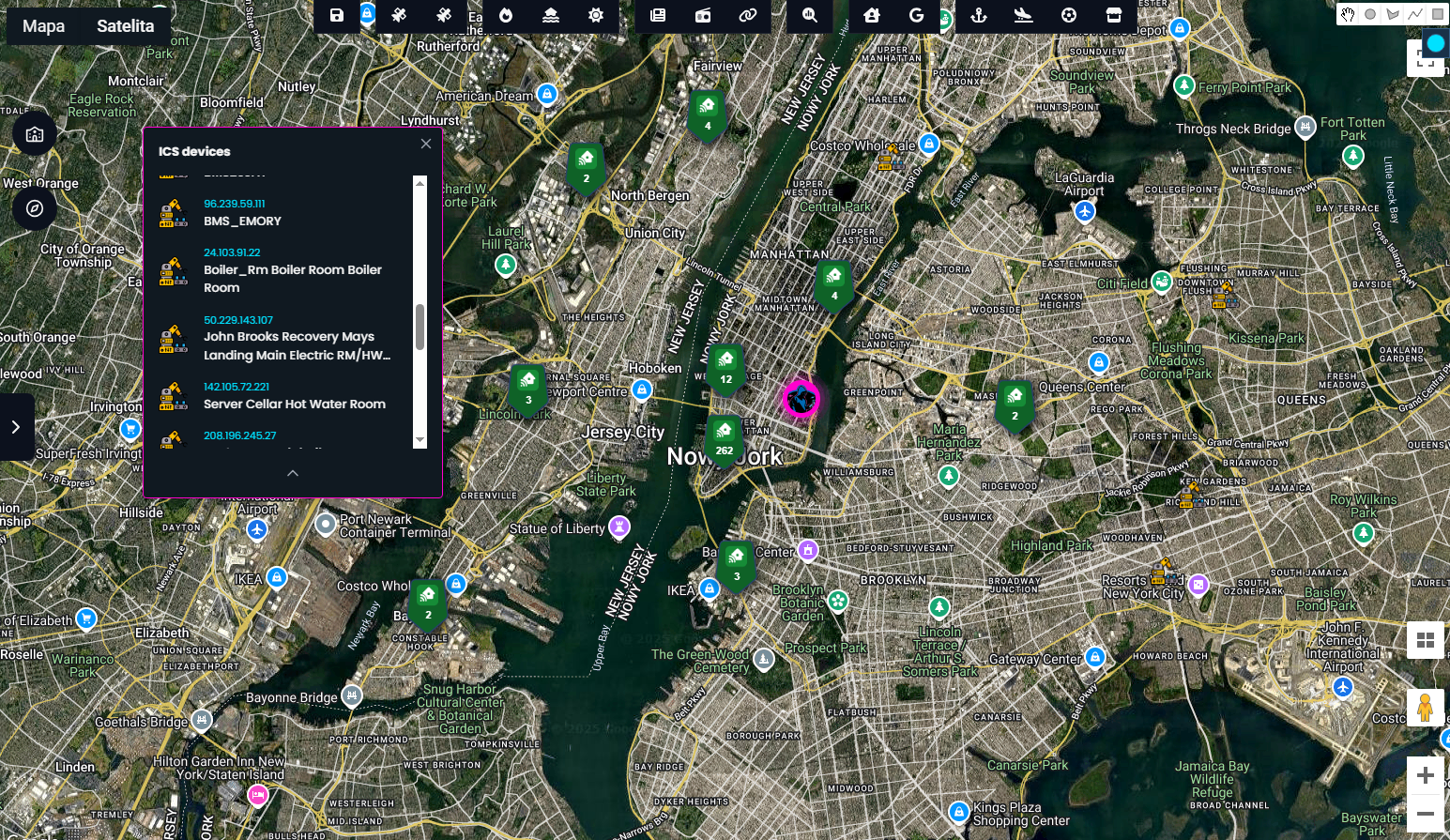
Another powerful and widely recognized data source integrated into the platform is Shodan - a search engine for internet-connected devices. It allows users to identify and analyse a wide range of systems, including ICS (Industrial Control Systems), IP cameras, IoT devices, and more.
In many cases, it's possible to geolocate where these devices are operating, offering valuable context for investigations involving critical infrastructure or exposed assets.
I’ve written a few articles exploring how to use Shodan effectively in OSINT and situational awareness workflows. You can check out one of them below

Suspicious devices are also text based, and following indicators are used
CRITICAL_INFRASTRUCTURE_KEYWORDS = [
# HVAC and building environmental systems
"hvac", "ahu", "airhandler", "air_handling_unit", "vav", "chiller", "cooling_tower",
"fan_coil", "fcu", "boiler", "duct", "damper", "temperature", "humidity", "thermostat", "server",
# Power and lighting
"generator", "ups", "breaker", "power", "control", "med"
# Water and plumbing
"pump", "valve", "water_meter", "flow_sensor", "sprinkler", "backflow", "leak_detected", "water",
# Elevators and access systems
"elevator", "escalator", "lift", "door", "plant", "court"
# Security and alarms
"alarm", "security", "motion"
# Energy monitoring and smart grid
"energy", "solar",
"building", "bems", "ems", "energy_dashboard",
# Infrastructure/system-wide
"bms", "bas", "scada", "ics", "rtu", "plc", "vfd", "controller", "io_module", "sensor",
"actuator", "system"
]If any of these words appear in the device's response, it's treated as a fragile one and potentially operating in critical infrastructure facility.
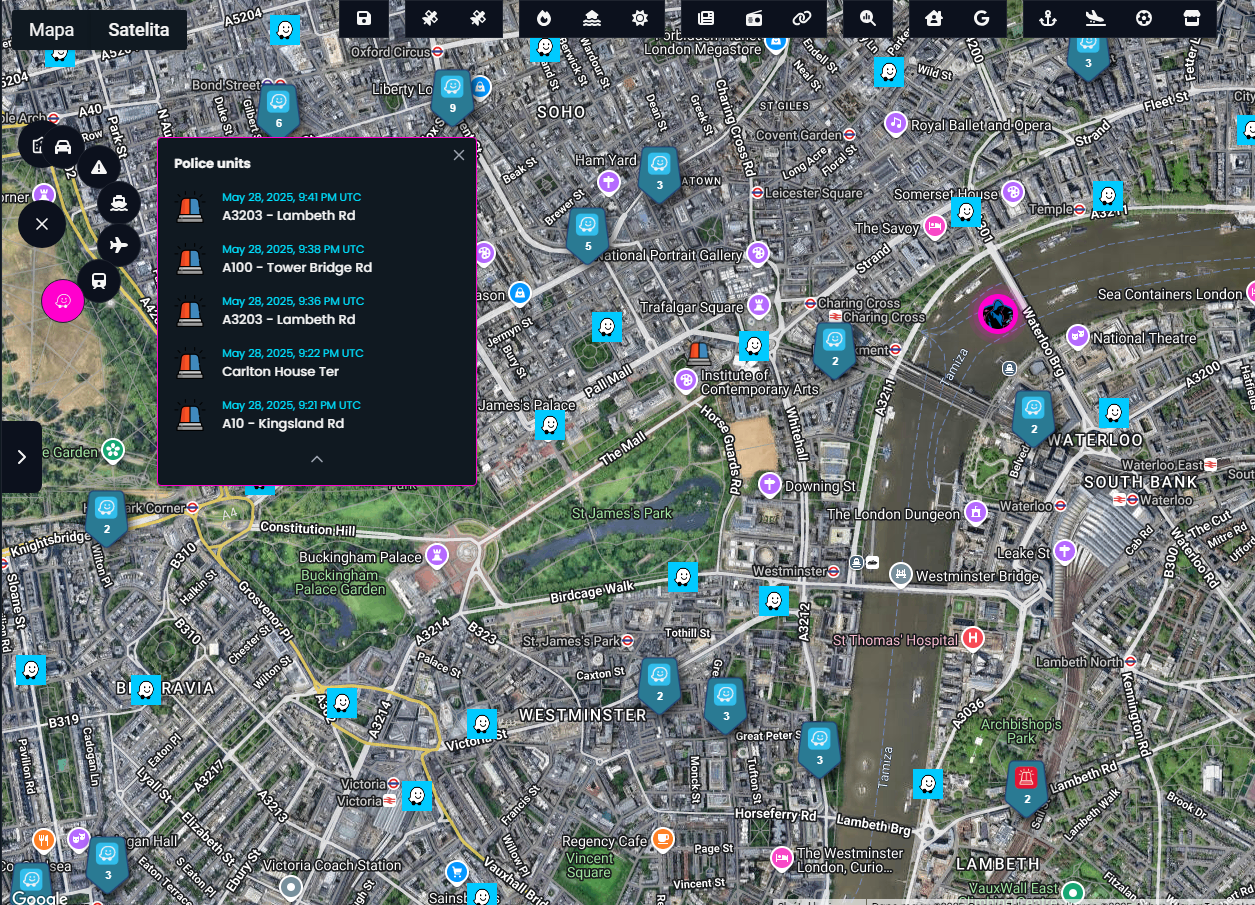
Police
To gain a deeper understanding of what’s happening in a city at any given moment, it’s essential to include data from emergency services and first responders. That’s where the Waze module comes in.
This module provides real-time information on road incidents, traffic disruptions, and sightings of police units reported by users. All incoming data is filtered, and the 10 most recent police units appearances are presented on the interface offering a quick, actionable snapshot of local activity.
By combining this with other geospatial layers, users can instantly detect emerging disruptions or patterns that require attention.
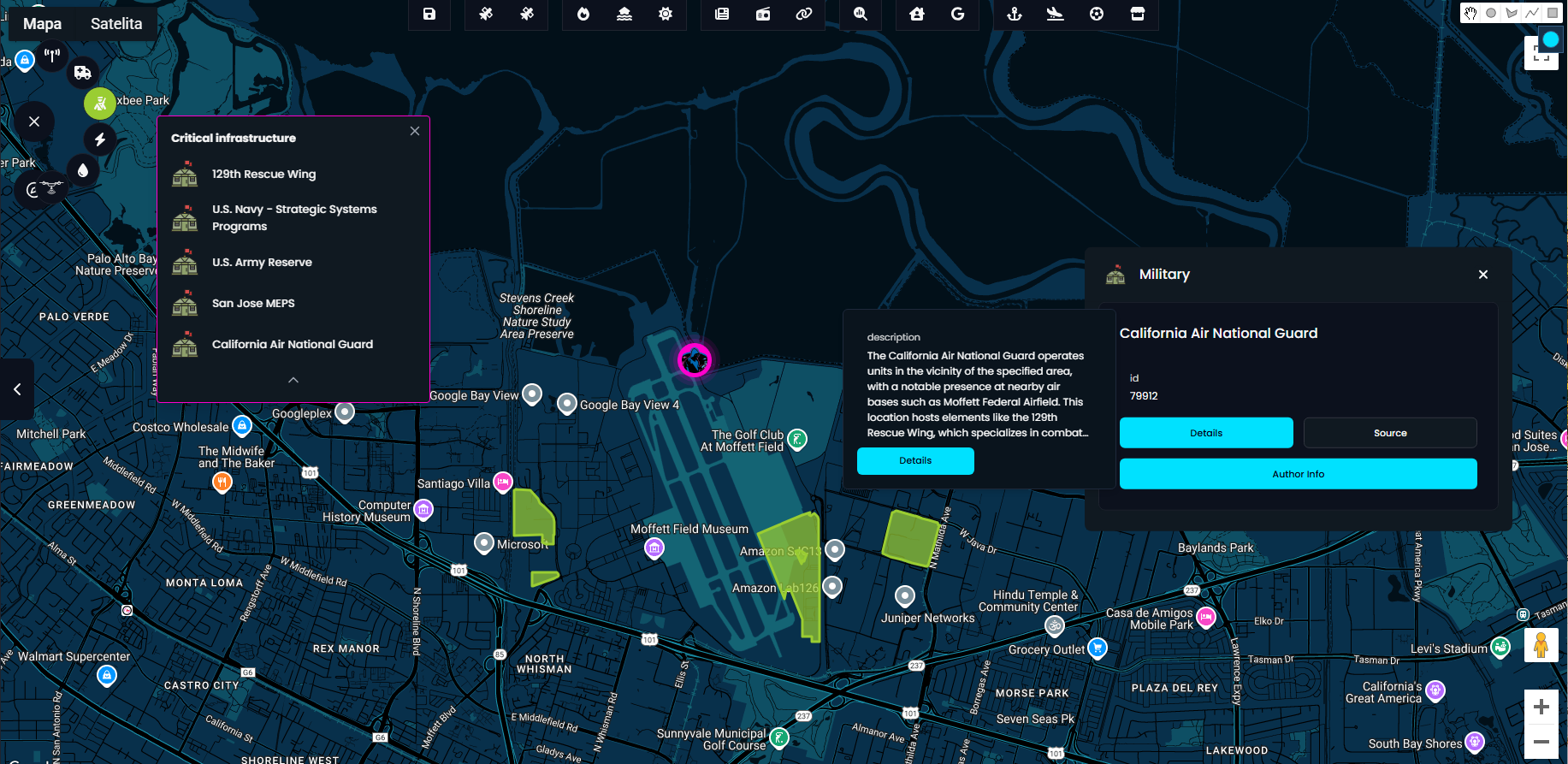
Critical infrastructure
The system supports five types of critical infrastructure: Power, Water, Communication, Emergency Services, and Military. With a single click, all relevant facilities within a selected area are instantly highlighted on the map what gives immediate insight into the region strategic assets.
For deeper context, simply click on Author Info to access additional details about a specific facility or building.
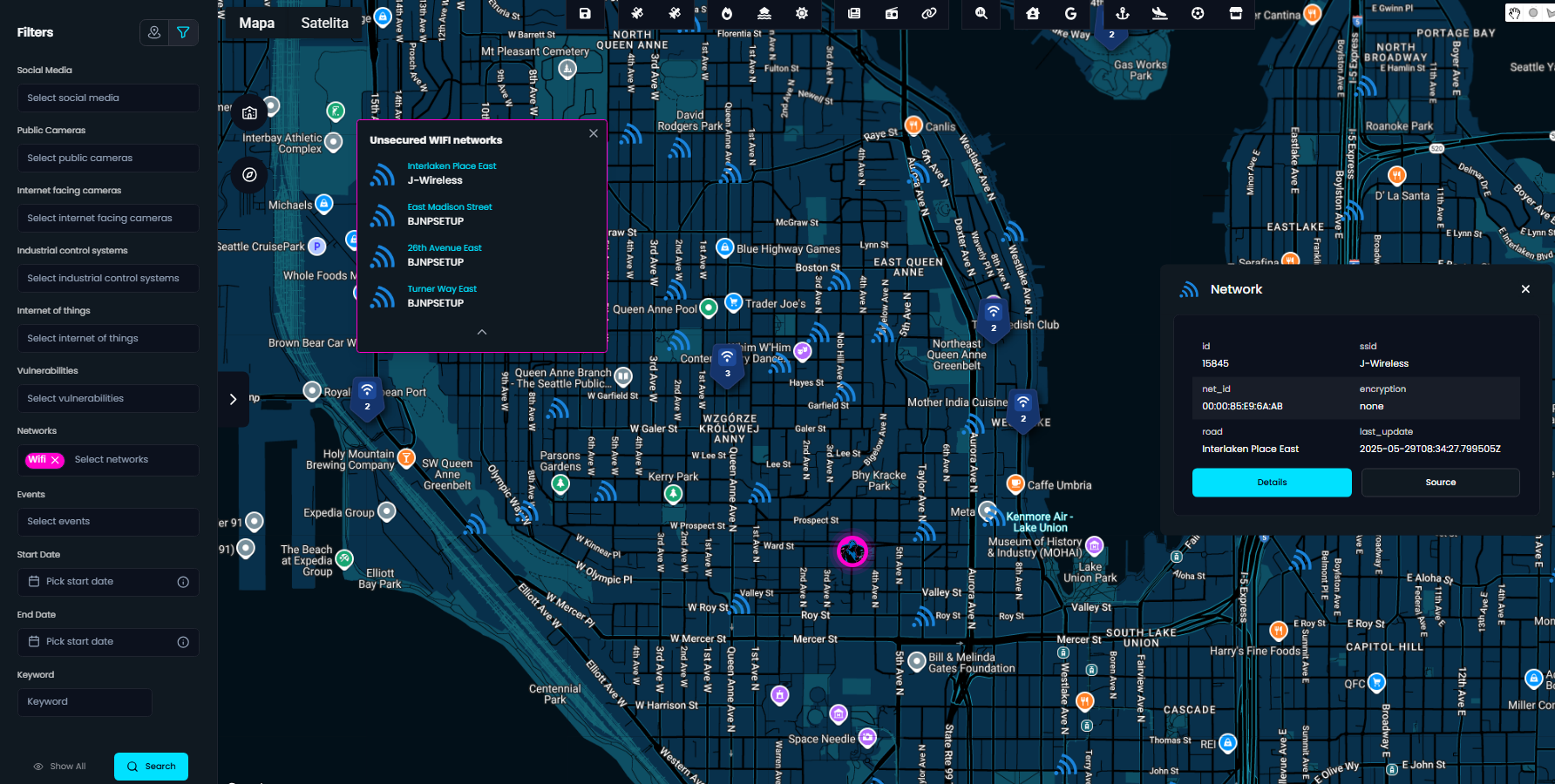
Unsecured Wi-Fi networks
From a security standpoint, it’s crucial to consider all potential attack vectors and public, unsecured Wi-Fi networks are often overlooked.
The system now automatically filters and displays only those access points using WEP encryption or no encryption at all, helping you quickly identify vulnerable networks during territory reconnaissance. This provides valuable context in both urban security assessments and threat surface mapping.
Social media & events & crimes
Every search returns a wealth of activity from various time ranges and sources, but in situational awareness, staying up to date is absolutely critical. That’s why the system now highlights the latest crimes, social media posts, and upcoming events directly in the search results.
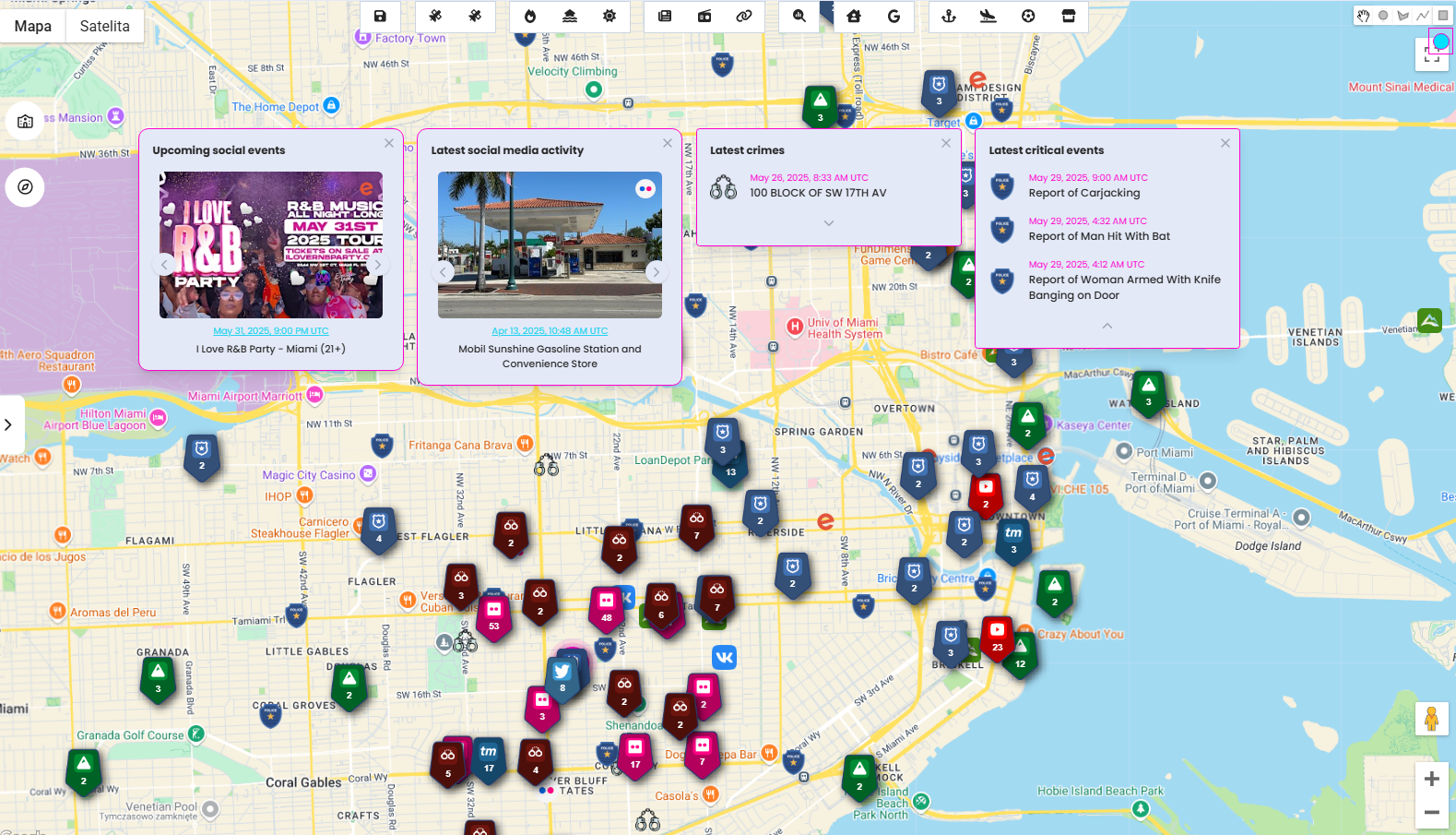
Of course, you can still dive deeper into any location using the timeline and statistical view for historical context and trend analysis.
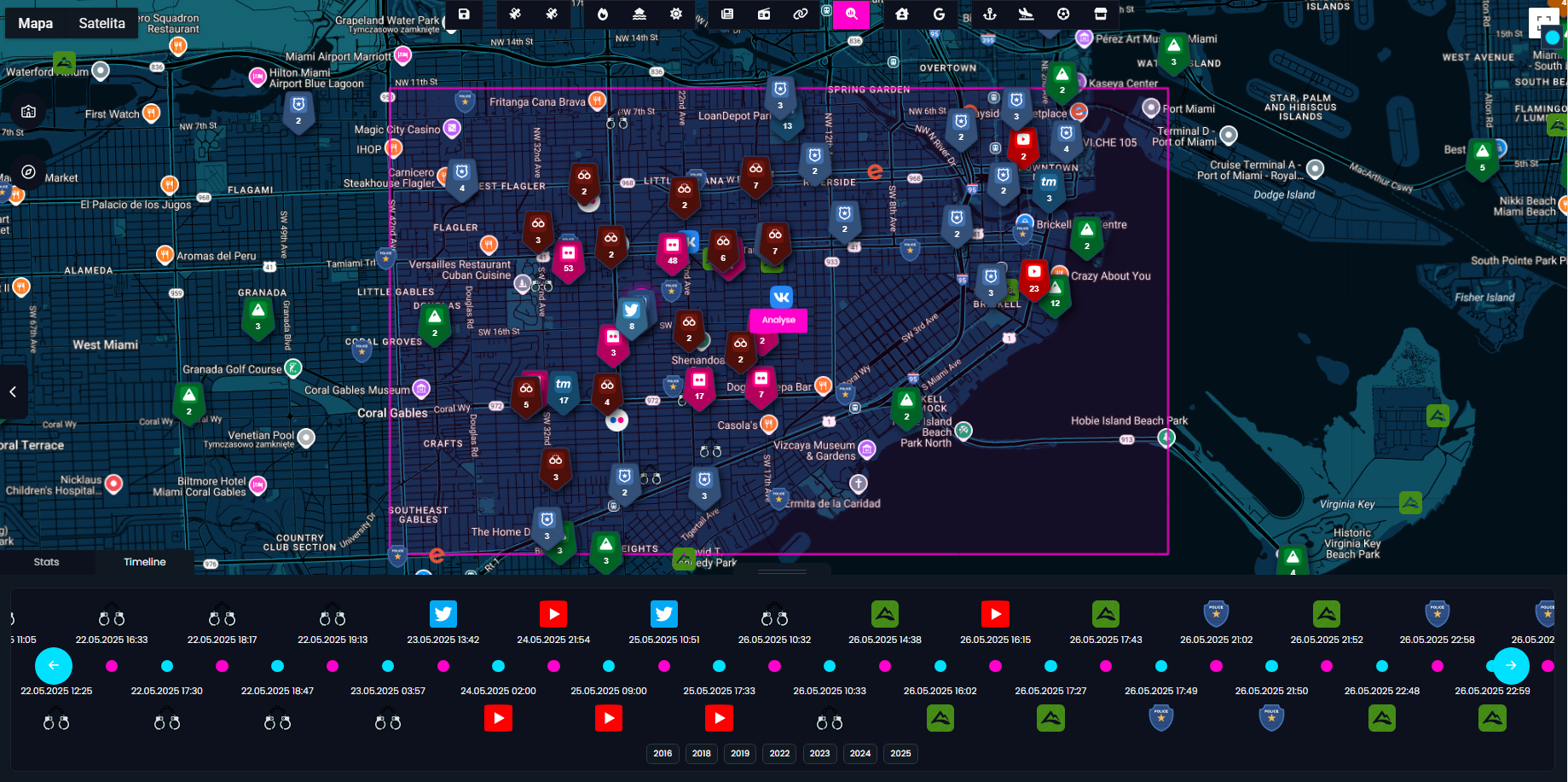
Tracking real-time developments helps you spot emerging threats, detect patterns before they escalate, and respond to incidents while they’re still unfolding. Whether you're monitoring for public safety, crisis response, or operational planning, timing is everything and this feature ensures you're never skip anything.
Have an improvement idea? Want to cooperate? Contact me via email

Summary
Context and anomaly detection are what transform raw data into actionable intelligence and they are the core of any effective situational awareness system, including OS-Surveillance. These capabilities take the platform one step closer to being fully automated, enabling smarter, faster territory reconnaissance without manual filtering.
By identifying deviations from the norm, such as unusual flight patterns, unexpected vessel movements, or abnormal social activity, the system helps users focus on what truly matters, rather than drowning in a noise.
Furthermore, as more data sources are integrated and detection models refined, the platform will continue to evolve into a truly autonomous real-time intelligence engine designed to spot critical activity the moment it happens.





