Script parses Pastebin email:password dumps and collects information about each email address. It supports Google, Trumail, Pipl, FullContact and HaveIBeenPwned. Moreover, it allows you to send an informational mail to person about his leaked password. At the end every information is stored in Elasticsearch for further exploration.
Tool here
DISCLAMER
No one was hurt during the research and no accounts have been compromised. Accessing any account that doesn’t belong to you is a crime.
Introduction
Pastebin gives great OSINT opportunity, you can find there really valuable, from intelligence point of view, material. First to mention are doxing i.e. personal identification information of specific individual — physical address, social media accounts, relatives, etc (if contains SSN and more private info — it’s called fullz).

A lot of malware configuration are hosted on Pastebin as well as malwares indeed. Bad actor can upload base64 encoded file or scrip,t and then retrieve it, decode and execute on victim’s machine. Monitoring it in real time gives big playground for OSINT hunters and researchers.
Another type of „pastes” are dumps, which are credentials in different format from variety of sources. The accounts may come from freshly compromised database or previous old hacks.
Among mentioned, Pastebin „offers” connection strings, API tokens, compromised Netflix & Spotify accounts, onion sites and much more.
Post Exploitation Pastebin Emails
Do you remember all sites that you have ever registered? And every password? Even at times when you weren’t using password manager?

These sites, if existed, still have your information like email and password. One of the first test to join one of the forum on Darknet was to successfully execute sql injection on random site, and as a proof of hack candidate send database details. After that, he puts whole database on Pastebin, including plain text credentials (because why not). If your account is there would you be safe?
The most important thing is, whether or not you reused your password on any other service. That’s how credential stuffing works.
A lot of dumps are posted on daily basis, with thousand of credentials. Pepe.py parses these dumps in order to get information about other possible accounts associated with particular email address.
It’s worth to mention that your search can be more precisely, pepe.py supports white and black lists. Black list makes that emails contained common domains like „gmail.com”,”yahoo.com” or”hotmail.com” won’t be checked. However, with white list approach, it will look only for the given domains like „protonmail.com”, „tutanota.com” or „bundestag.de”
Google module gives links where it finds appearances of the email address, by that you can find more and more dumps, because email may appear in multiple leaks. It can also lead to forum posts or Facebook groups where stolen credentials are traded. Additionally, you can determine if email address is in public domain or private/corporate. That’s bad if someone would use this same email and password for private and work related accounts.
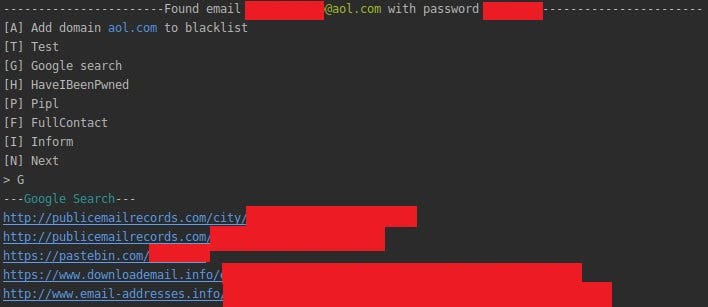
HaveIBeenPwned
Have I been Pwned gives you access to all the breaches that email address occurred in, it’s another lead that might point to potential account compromise. If your account or whole vendor database has been compromised, you should change your password as soon as possible. If not, having your email address and password, it’s possible to try this same password on other services.
Pipl & FullContact
Pipl and FullContact modules are really like knowledge base about people. You can retrieve information like social media profiles, name, address (or country at least), job and more. It’s perfect tool to filter the results, the most valuable accounts are for example: Twitter accounts that have more than 100 followers or CEO/Director position appears in job’s description. You can connect it with black/white list method.

Trumail & Sending info
Last stage allows you to verify email address, whether it’s deliverable or not and inform the person about possible leak. First thing you can achieve with Trumail and second by choosing „I” in interactive mode and send him/her email.

Hunting for a big fish
A lot was said about hack/leak? of private information of German's politicians but still I haven’t seen any statement about how the guy got access or what method was used. The graphical theme of every published leak — ascii art, mirrors to Pastebin-like services and content which came from personal social media accounts might suggest credential stuffing attack. Pastebin constantly tries to remove and react to every report and take down the paste but still there is some time to scrape it.

In Pepe you can choose between two methods, interactive and non-interactive. In non-interactive you need to pick modules and wait for the output in console or Elasticsearch. Moreover, it’s possible to setup a push notification if specific criteria will be met, for example mentioned Director position on LinkedIn.
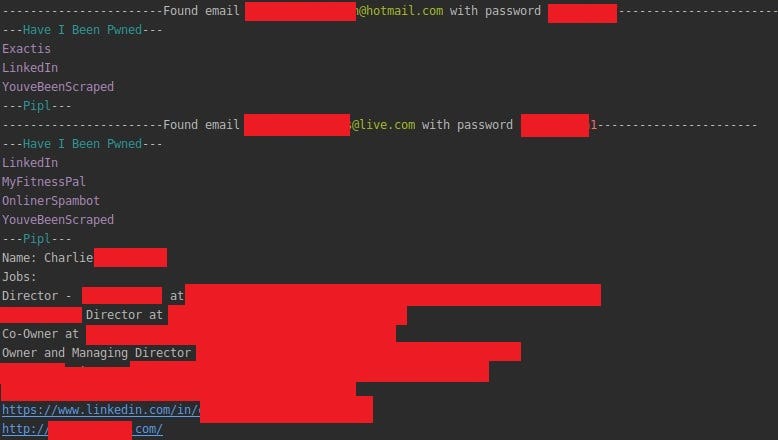
Interactive mode allows to decide which module will run for which email address. You can review whole dump this way and find potential „big fish”. Also here, every information is saved to Elasticsearch.

When it’s possible to associate any high profile member with his password then also his pattern revealed.Is it something easy to remember like “zaq12wsx”? Something personal like spouse’s name? If someone knows the pattern, he can easily gather more evidence to figure out possible new password.
Setting up blacklist and excluding common email providers will give more chances to find high profile person with customized private domain.
At the end you can inform person about potential leak. Message can be customize in config file.
Conclusion — password problem
As an advice for red-teamers, some of the password for LinkedIn breach are still sort of valid. I saw case when one change from „W!inter2017” to „Spr!ng2019”, leads to domain compromise. Some old patterns never change.
Protip#2 If you come across account which uses name of his child as a password, you can check for other „artifacts” like other kids’ names. It’s pretty common to have password that actually means something for someone. It’s like a cat and mouse game between password and hacker. It might be child’s name, favorite soap opera actor or chess player. People usually are not aware about consequences of simplicity of passwords they have.
When you figure out someone’s password, is it still #OSINT or #hacking?
That’s everything, remember to follow Troy Hunt to check for data breaches, use password manager together with 2FA and you will be fine.
In addition, there is no point in publishing more posts here, so most probably this blog will not be updated. Thanks for every view and follow!
Originally published on 12nd of April, 2019



